The role of the chief information security officer (CISO) has evolved significantly since its emergence in the mid-1990s. Today, it represents a critical pillar in an organization's cybersecurity framework. Initially finding its footing in an enterprise landscape that had yet to fully recognize its significance, the CISO role has undergone a considerable transformation, adapting to
ever-changing technological advancements, regulatory requirements, emerging threats, and increasingly sophisticated threat actors.
As custodian of the organization's cybersecurity defenses, the modern-day CISO grapples with diverse challenges ranging from combating cyberthreats to navigating intricate regulatory frameworks, all while ensuring seamless alignment between cybersecurity strategies and overarching business goals.
Effectively fortifying organizations in an increasingly precarious digital environment requires delving into the historical evolution of the CISO role, examining the current challenges CISOs face, and outlining strategic approaches and best practices essential to modern CISOs.
The Evolving Nature of the CISO Role
The CISO role is a relatively new position. Steve Katz, widely considered the first CISO in the world, filled the security executive role at Citicorp in 1995 after the bank experienced a major cyberbreach that affected its electronic funds transfer system.1 In contrast, the chief information officer (CIO) role was defined in the boardroom in the early 1980s,2 a decade before its CISO counterpart. To put this into perspective, in 2023 it was estimated that there were more than 69,240 CIOs employed in the United States,3 compared to an estimated 7,523 CISOs currently employed in the United States.4 However, the CISO role continues to be integral to the organizational governance of IT security, as demonstrated by the fact that almost every Fortune 500 company has hired a CISO within the last 20 years.5
The demands of the CISO have shifted since its introduction in the mid-1990s.6 Figure 1 provides an overview of the historical phases of the CISO.
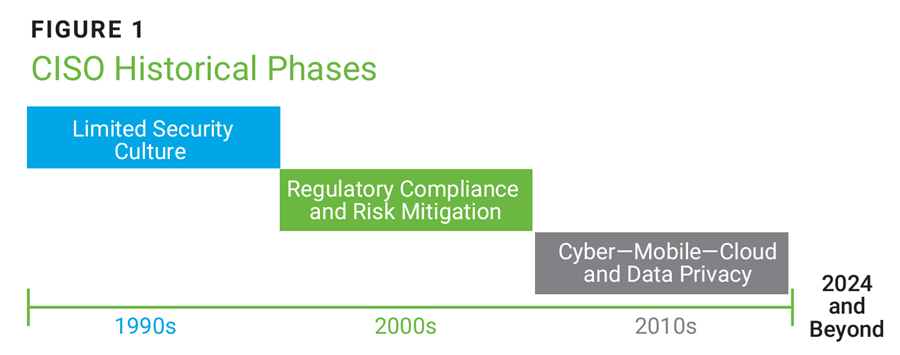
Source: Fitzgerald, T.; CISO COMPASS: Navigating Cybersecurity Leadership Challenges with Insights from Pioneers, Auerbach Publications, USA, 2018
Pre-2000s
During the pre-2000s, the CISO role was in a “limited security” phase.7 The central focus of the CISO was on internal login IDs, password provisioning, and control of physical access. Security by obscurity was at the forefront of many security strategies. Further, security leaders during this time came from a predominantly technical background and were usually positioned within the IT department. During this time, it was the norm for a security leader to occupy a manager, director, or technical system administrator position.
The 2000s
In the early 2000s, jurisdictions in the United States adopted various laws focusing on information security and privacy.8 Regulations such as the US Health Insurance Portability and Accountability Act of 1996 (HIPAA), the US Gramm-Leach-Bliley Act (GLBA) of 1999, the US Sarbanes-Oxley Act (SOX) of 2002, and the US Federal Information Security Modernization Act (FISMA) of 2002 established requirements for private and public organizations to safeguard sensitive information.
Additionally, US states began adopting breach notification laws after the US State of California’s S.B 1386 became law in July 2003. In response to the increase in rulemaking, CISOs took a more compliance-oriented approach to their security strategizing, working with legal departments to ensure that organizational processes effectively covered applicable regulations.
The 2010s
The 2010s were characterized by astronomical growth in Internet-connected devices and the prevalence of the smartphone.9 The smartphone enabled the masses to easily surf the Internet and engage on social networking websites. For example, it is estimated that in 2010 Facebook had nearly 500 million monthly active users (MAUs).10 By 2017, the number of Facebook MAUs surpassed 2 billion.11 In addition to the challenges presented by social networking, CISOs were faced with the growing trend of bring-your-own-device (BYOD) policies. Many CISOs found themselves in the position of having to expand their organization’s attack surface by allowing personal devices to enter the internal network—or worse, struggle to counteract the sentiment of “Don’t bring this matter to the security team, they always say no.” Ultimately, solutions such as mobile device management allowed exploration of this new security frontier while lowering the risk to the organization.
Privacy concerns also became more prevalent in the 2010s, resulting in the adoption of privacy laws.12 In 2018, the EU General Data Protection Regulation (GDPR) came into effect. The GDPR governs the way enterprises can use, process, and store the personal data of citizens of the European Union.13 That same year, the US State of California Consumer Privacy Act (CCPA) was enacted, granting certain consumer privacy rights for Californians.14 Although the chief privacy officer (CPO) role is gaining traction specifically for dealing with privacy concerns, the CISO must work closely with the privacy function of the organization to understand the implications privacy efforts may have on security and vice versa.
As custodian of the organization's cybersecurity defenses, the modern-day CISO grapples with diverse challenges ranging from combating cyberthreats to navigating intricate regulatory frameworks, all while ensuring seamless alignment between cybersecurity strategies and overarching business goals.Challenges Confronting Modern CISOs
Today, CISOs must ensure that defending against emerging threats and sophisticated cyberattacks is part of their cyberstrategies. It is predicted that cybercrime will reach US$8 trillion annually in 2023.15 In part, this high dollar value could be attributed to the increase in the number of cyberattacks year over year, as well as the growing prominence of social engineering and ransomware attacks. In a report by the cybersecurity firm zScaler, ransomware attacks increased by more than 37% in 2023, with the average enterprise ransom payment exceeding US$100,000 and an average demand of US$5.3 million.16 For a CISO, it is important to equip the organization with incident response playbooks that cover social engineering attacks and ransomware attacks.
Transparency and open communication following a security incident have been brought to the forefront for the CISO. For example, in 2023, the US Securities and Exchange Commission (SEC) issued its final ruling on disclosures related to material cybersecurity incidents experienced by publicly traded companies.17 The ruling specifically requires that an organization disclose any cybersecurity incident within four business days of determining that the cybersecurity incident is material. The challenge for CISOs now is understanding how to determine whether an incident meets the materiality threshold and how much information about the incident should be disclosed. As regulations continue to focus on information security matters, CISOs must ensure that they are meeting the demands of the diverse regulatory frameworks that govern information security and data privacy.
Best Practices and Strategies for Modern CISOs
CISOs should continue to align cyberrisk management with the strategic objectives of their organizations. According to a research study performed by TrendMicro, 50% of IT leaders and 38% of business decision-makers believe the C-suite completely understands cyberrisk.18 Furthermore, a study performed by Forrester found that fewer than 50% of security leaders framed the impact of cybersecurity threats within the context of a specific business risk.19 What this could suggest is that IT leaders and, specifically, IT security leaders are not doing a good job of framing security issues in a manner that the enterprise understands. To bridge this gap of miscommunication between the board and executive leadership, CISOs can align cyberrisk management with the organization’s strategic objectives. Strategies may include:20
- Understanding the board and executive leadership’s concerns and aligning cyberrisk to business areas including market trust, compliance, cost of controls, security liability, etc.
- Connecting security objectives to established business requirements
- Including executive oversight in cyberrisk strategy and budget planning to align cyberrisk investments and enable the business to pursue market initiatives and develop cyber key performance indicators (KPIs)
CISOs should embed cyberrisk management in the organization’s governance structure. To ensure that cyber is part of the governance structure, organizations can develop a cybergovernance committee/team and enhance the role of the CISO, such as by ensuring that the CISO is empowered to make key business decisions and provided with access to the board and other members of the executive leadership team.21 A cybercommittee will allow the organization to build strategic partnerships with various business units within the enterprise and provide cyberoversight for projects throughout the organization. Some key things to keep in mind when establishing such a committee are:22
- Members of the committee should include the leadership team, key stakeholders, and business representatives.
- The committee should have a governing charter designating authorities and responsibilities for the committee and its members.
- The committee should establish business-level reporting on business activities.
Conclusion
The evolution of the CISO role is a testament to the relentless dynamism within the cybersecurity field. From its nascent stages marked by a lack of distinct recognition to its contemporary stature as a linchpin for organizations’ information security programs, the journey of the CISO reflects an ongoing adaptation to an ever-evolving threat landscape. As evidenced by the historical phases delineating its growth, the CISO's responsibilities have expanded exponentially, encompassing not only technological defense strategies but also regulatory compliance, strategic alignment with business objectives, and proactive resilience against emerging threats. For years to come, CISOs will face an intricate web of challenges, including the escalating sophistication of cyberthreat actors, regulatory complexities, and the imperative to bridge the understanding gap between cybersecurity risk and business impact. Nevertheless, by embracing strategic paradigms and embedding cybersecurity within the fabric of organizational governance, modern CISOs can effectively navigate these challenges, ensuring robust protection for their organizations while fostering a cohesive synergy between cybersecurity and broader business imperatives.
Endnotes
1 Townsend, K.; “CISO Conversations: Steve Katz, the World’s First CISO,” SecurityWeek, 1 December 2021, https://www.securityweek.com/ciso-conversations-steve-katz-worlds-first-ciso/
2 Synnott, W.R.; Gruber, W.H.; Information Resource Management: Opportunities and Strategies for the 1980s, John Wiley & Sons, USA, 1981
3 Zippia, “Chief Information Officer Demographics and Statistics in the US,” https://www.zippia.com/chief-information-officer-jobs/demographics/
4 Ibid.
5 Cybercrime Magazine, “List of Fortune 500 Chief Information Security Officers,” https://cybersecurityventures.com/ciso-500/#home/?view_1_page=1
6 Fitzgerald, T.; CISO COMPASS: Navigating Cybersecurity Leadership Challenges with Insights from Pioneers, Auerbach Publications, USA, 2018
7 Ibid.
8 Ibid.
9 Ibid.
10 Ortiz-Ospina, E.; “The Rise of Social Media,” Our World in Data, 18 September 2019, https://ourworldindata.org/rise-of-social-media
11 Ibid.
12 Op cit Fitzgerald
13 VinciWorks Group, “What Is GDPR in Simple Terms?,” VinciWorks, 31 March 2022, https://vinciworks.com/blog/what-is-gdpr-in-simple-terms/?pu=delta#:~:text=GDPR%20 stands%20for%20General%20Data,an%20 identifiable%2C%20living%20person
14 Bloomberg Law, “What Are the CCPA and CPRA?,” https://pro.bloomberglaw.com/insights/privacy/california-consumer-privacy-laws/#:~:text=The%20California%20Consumer%20Privacy%20Act%20(CCPA)%2C%20signed%20into%20law,1%2C%202020
15 Cybersecurity Ventures, “2022 Official Cybercrime Report,” https://s3.ca-central-1.amazonaws.com/esentire-dot-com-assets/assets/resourcefiles/2022-Official-Cybercrime-Report.pdf
16 Zscaler, “Zscaler ThreatLabz 2023 Ransomware Report,” 2023, https://info.zscaler.com/resources-industry-reports-2023-threatlabz-ransomware-report
17 US Securities and Exchange Commission, “SEC Adopts Rules on Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure by Public Companies,” USA, 26 July 2023, https://www.sec.gov/news/press-release/2023-139
18 Trend Micro, “Trend Micro: 90% of IT Decision Makers Believe Organizations Compromise on Cybersecurity in Favor of Other Goals,” November 2021, https://www.trendmicro.com/explore/en_gb_trend-micro-global-risk-study
19 Bond, R.; “Aligning Cyber Risk Management Goals to Business Objectives,” LinkedIn, 15 July 2023, https://www.linkedin.com/pulse/aligning-cyber-risk-management-goals-business-objectives-robert-bond/
20 McGlynn, M.; “3 Ways CISOs Can Align Cybersecurity to Business Goals,” TechTarget, 18 March 2021, https://www.techtarget.com/searchsecurity/post/3-ways-CISOs-can-align-cybersecurity-to-business-goals; Hudson, D.; “Aligning Enterprise Cyber Risk and Business Strategy,” Coalfire, https://coalfire.com/the-coalfire-blog/aligning-enterprise-cyber-risk-business-strategy
21 Op cit Hudson
22 Ibid.
BRIAN VASQUEZ | CISA, CEH, CISSP, GCIH, GSLC, GSTRT
Has worked in information security for more than 10 years and is currently the director of information security and compliance for California State University, San Bernardino (CSUSB) (California, USA). In this role, he leads campus information security risk management efforts. His research areas of interest include cyber workforce issues and human factors in cybersecurity. Vasquez is passionate about giving back to the information security community and regularly volunteers with industry organizations such as ISACA® and ISC2, in addition to local organizations such as the United Way and CSUSB.
