Two key quantum developments have emerged in the cybersecurity space: post-quantum cryptography (PQC) and quantum key distribution (QKD).1 PQC has emerged due to advances in quantum computing that threaten to break classical algorithms such as RSA. Conversely, QKD has been developed as a method of secure key exchange, definitively addressing the issue of secrecy in algorithmic key exchange. While both topics relate to several basic implications of quantum physics in cryptography, they differ in their approaches to mitigating the risk of quantum computers being able to successfully break RSA encryption. In the case of PQC, it is a cipher change taking place, whereas QKD revolves around how keys are distributed. By analyzing these differences, practitioners will be able to better understand how quantum-based solutions are incorporated into different aspects of the cryptographic system—and how they will be affected by each one.
Figure 1 summarizes the key concepts of quantum computing and QKD advances and the basic physics required.

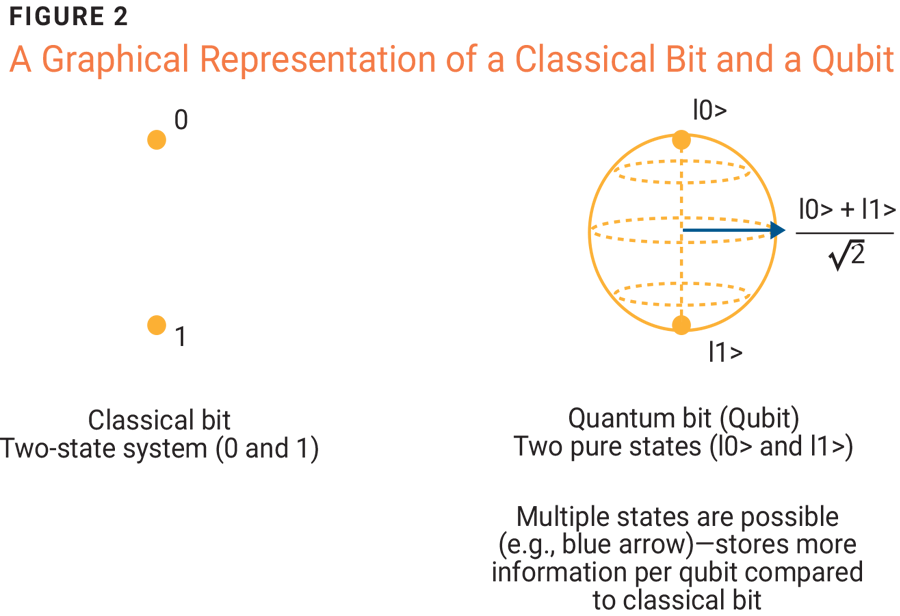
Introduction to a Qubit
A classical bit can only store data as 1 or 0. Think of it as a two-state system capable of storing information scales with 2^n, where n is the number of classical bits.
A quantum bit, also known as a qubit, uses a quantum mechanical property of superposition that allows it to be in the “1” quantum state, “0” quantum state, or any combination of these two quantum states (physicists refer to this as a linear combination of states). The “1” quantum state and “0” quantum states are known to be orthogonal.
Being allowed many more states implies a significantly more powerful way to store information, as fewer qubits are required to describe the entirety of a system's state. But once a qubit is being measured (i.e., observed), the qubit resolves to one of two orthogonal states, depending on how the measurement was conducted. The BB84 protocol, developed by Charles Bennett and Gilles Brassard in 1984, was the first protocol that exploited this property of quantum measurement to ensure the perfect forward secrecy (PFS) property of the system, which was validated by Peter Shor and John Preskill in 20002. In the case of BB84, the quantum no–cloning theorem ensures that, should a man in the middle attempt to steal the private key being sent, the act of stealing said key results in a quantum measurement. This disturbs the private key, which can then be detected by the recipient, as the information sent in two different bases will be different, revealing the presence of a man in the middle.3 But if PFS is assured, why is QKD still not more widespread?
QKD in the European Union and the United States
In 2009, electronic engineer Alan Mink published an overview of QKD that guarantees PFS and explains how commonly used security protocols such as IPsec and Transport Layer Security (TLS) can leverage QKD to achieve secure key exchange.4 The US National Security Agency (NSA), however, advised caution on QKD through a publication on quantum key distribution,5 which highlighted the following issues:
- QKD is expensive for what it offers; quantum-resistant cryptography (another name for PQC) is less expensive and better understood.
- QKD requires significant, special-purpose hardware because of the stringent error tolerances and limited flexibility for upgrades.
- The basic premise of QKD deterring eavesdroppers can expose the QKD system to a risk of denial of service.
However, the European Union has taken a different view of QKD. The European Quantum Communication Initiative (EuroQCI) has decided to design, develop, and deploy QKD solutions6 based on the developments by researchers of the European Union-funded Quantum Technologies Flagship7 and the Horizon 2020 OPENQKD Project.8 The European Union has also referenced QKD9 standards established by the International Telecommunications Union, which set the benchmark for secure communication protocols.10
The typical reader will likely not be building a QKD network due to its high cost. However, QKD remains relevant as the fundamental properties of quantum physics (specifically, the quantum no-cloning theorem)11 guaranteeing that key exchange remains secure are a more robust solution than PQC. Within the realm of PQC, advancements in technology can lead to ciphers based on different mathematical problems being cracked, necessitating yet another change of cipher. QKD discussions thus far have been limited to government and telecommunications applications as QKD involves the need to overhaul key distribution infrastructure, unlike PQC, where it is easier to implement cipher changes with vendor support. Hence, PQC is likely more pertinent to the average chief information security officer (CISO), head of IT security, or global cybersecurity team. For instance, the PQC Alliance12 includes some of the largest vendors currently cooperating to implement post-quantum cryptographic algorithms, some of which have already been announced by the US National Institute of Standards and Technology (NIST) through its FIPS 203–205 standards.13
An Introduction to PQC
In 2016, NIST solicited feedback and nominations to evaluate candidates for PQC,14 which led to four candidates being selected in 2022. Overall, the objective of this challenge in identifying PQC algorithms was to mitigate the risk of RSA being broken by a sufficiently powerful enough quantum computer that can factorize large numbers into their two primes.
PQC algorithms address this issue effectively, as quantum computers are built to solve highly specialized tasks, setting them apart from traditional computers. Changing the mathematical premise on which the algorithm is based should, in theory, circumvent this issue. Unfortunately, this is easier said than done.
One such candidate, SIKE, advanced through the final stages of NIST’s PQC selection process but was broken by a legacy computer chip.15 The broader implication was that one such class of mathematical problems,16 which at one point boasted small key sizes as an advantage, is not considered secure enough for PQC algorithms.
Among the four algorithms that have been selected for PQC standardization (NIST FIPS 203–205 have since been published, with NIST FIPS 206 soon to follow as of the time of this writing), three of them rely on lattice-based cryptography and hash functions.17
Quantum Computers
The elephant in the room, however, is the race against time due to advances in quantum computing.
In 2019, the MIT Technology Review18 purported that advances in quantum computing could in a few decades feasibly break the RSA algorithm. However, it also cautioned that the growing number of qubits in a quantum computer accentuates the issue of noise, which could slow quantum computer developments.
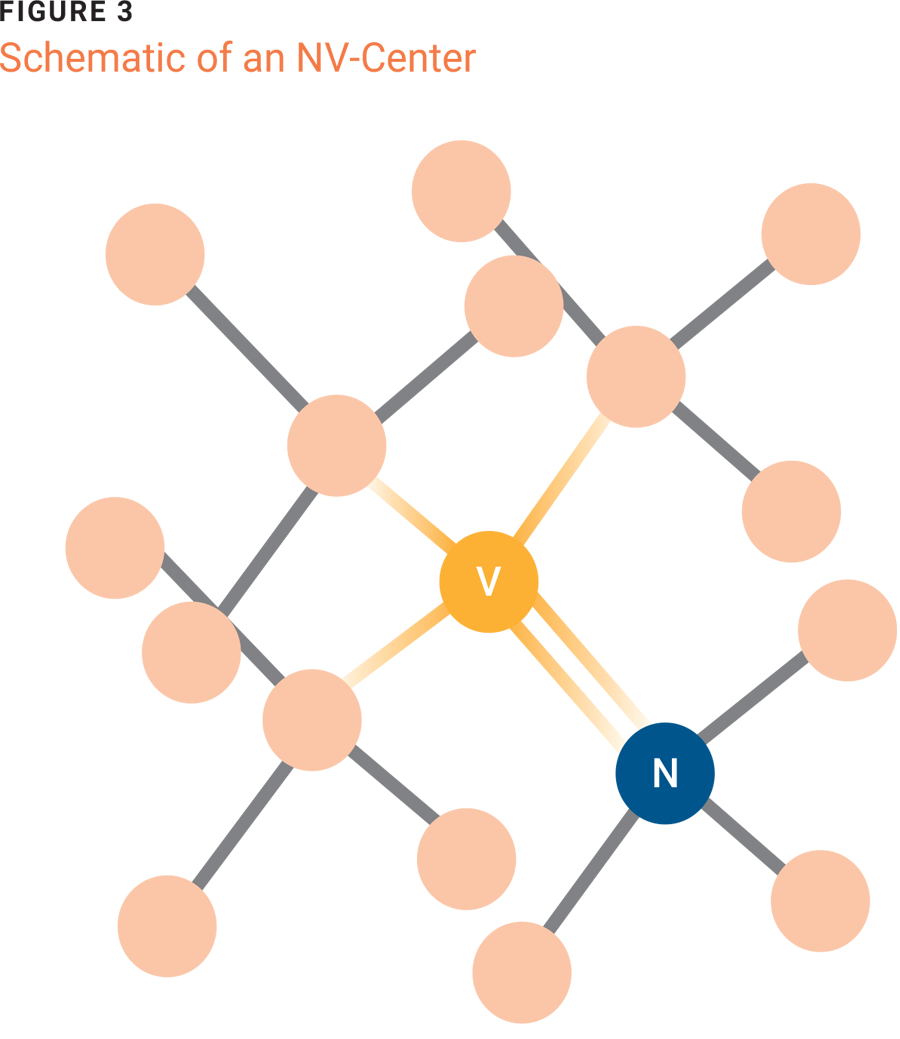
Quantum computers, until recently, have also faced cryogenic limitations. The earlier quantum computers, such as those that used superconductors or trapped ions, had to be cooled to very low temperatures to ensure that their quantum states stayed the way that they were (this is known as quantum coherence).19 Research has been conducted involving other types of quantum computers that could operate at room temperature, such as nitrogen-vacancy (NV) centers in diamonds.20 Such NV centers function as qubits that maintain their quantum coherence, potentially making quantum computers more accessible as they do not require supercooling mechanisms that otherwise may be too costly or inconvenient to site.
Predicting when a quantum computer will break RSA is difficult because it is not clear which technology or entity’s quantum computer is the leading candidate to do so.Figure 3 illustrates an NV center. One carbon atom has been substituted with a nitrogen atom, which creates a hole (vacancy) that functions as the qubit.
Predicting when a quantum computer will break RSA is difficult because it is not clear which technology or entity’s quantum computer is the leading candidate to do so. Different consulting firms predict different time frames wherein a quantum computer could be practically used to crack RSA (also termed a “cryptographically relevant quantum computer” in this context). For instance, the German Federal Office for Information Security has concluded that new developments in algorithms, error correction, and mitigation, as well as the larger variety of actors in the quantum computer space (firms and nation states) and the classified nature of some of these developments, makes it difficult to predict when RSA can be cracked by a cryptographically relevant quantum computer.21
Regardless of when RSA will eventually be broken, there are certain types of secrets that, if unable to be decrypted today, could still be valuable to decrypt even after two or three decades, (e.g., intellectual property, classified correspondence). This forms the basis of the Harvest Now, Decrypt Later (HNDL) problem. Because the HNDL threat varies largely depending on the nature of the organization, each industry will likely weigh such threats differently.
Concerns for CISOs
At an architectural and data level, CISOs will likely need to identify data most susceptible to the HNDL threat. This can include information that needs to be kept classified for many years, such as patents and other associated intellectual property; multiyear project deals; closed-source programs; and biometric minutia. Additionally, CISOs will also need to consider cryptographic agility, which refers to the ability to switch between multiple cryptographic algorithms. In some products, this may be as simple as switching the set of supported cryptographic algorithms as part of a setting to enable or disable various cryptographic algorithms. This will help ease the transition between current cryptographic algorithms to newer ones. Cryptographic agility is not a simple one-to-one swap of algorithms, as can be seen by the increased key sizes of newer PQC algorithms. This likely affects the entire system infrastructure due to the ubiquity of cryptographic implementations in all modern communications today.
Ultimately, cybersecurity questions, including those of the quantum variety, boil down to risk. The good news is that not all cryptography will be upended by quantum computers. Symmetric key algorithms such as AES-256 remain quantum-safe.22 However, most organizations use some form of asymmetric keys, such as RSA or ECC, due to their implementation of PKI. These will be affected and necessitate planning for a migration strategy once vendors come on board with suitable PQC algorithms. The PKI Consortium has published a table of vendors that shows who has started incorporating PQC algorithms into their products,23 and the bigger technology players such as Apple24 have released their own implementation of PQC algorithms.
Another issue with migration to PQC that will likely be top of mind for CISOs is the size of keys, which affects the speed of cryptographic operations. RSA-2048 keys are generally compact, but many of the candidates and alternates report larger public key and/or signature lengths and take a slightly longer amount of time to perform various cryptographic operations such as encryption or decryption.25 Attempting to create a best-of-breed by incorporating multiple cryptographic algorithms may be an excessive load on the devices themselves, and Cloudflare has also noted how the slight performance degradation, put together in series, can result in user-observable performance drops.26
Conclusion
It is critical to address the intersection of two seemingly disparate quantum topics relevant to cryptography related to quantum physics, highlighting their different trajectories of discussion.
Specifically, while QKD is relevant for large-scale infrastructure projects, there is great interest in PQC developments, as these are more actionable for the average practitioner.
The HNDL dilemma and its relevance to certain types of organizations is likely to provide CISOs with an impetus to move away from quantum-unsafe algorithms such as RSA-2048. However, PQC presents challenges in how larger key sizes and signing can impact performance. This is likely of concern for devices with little processing power, such as Internet of Things (IoT) devices or devices with time-sensitive applications (e.g., in the defense context).
Quantum research will continue to progress as researchers strive to develop more advanced quantum computers that can break RSA encryption. However, it remains unclear which entity will emerge as the market leader or when RSA will eventually be broken. What is clear is that cryptographic agility will become a more important topic as the quantum threat continues to evolve.
Author Note
The views expressed in this article are those of the author alone and do not reflect the views of the author's employer.
Endnotes
1 IDQuantique, “Quantum Key Distribution”2 Prisco, J.; “Another Security Plus for QKD: Perfect Forward Secrecy,” Forbes, 11 December 2023, Shor, P.; Preskill, J.; “Simple Proof of Security of the BB84 Quantum Key Distribution Protocol,” 12 May 2000
3 QuIC Lab, “Quantum Key Distribution (QKD),” 2019
4 Mink, A.; Frankel, S.; et al.; “Quantum Key Distribution (QKD) and Commodity Security Protocols: Introduction and Integration,” International Journal of Network Security & Its Applications, vol.1, iss. 2, 2009
5 National Security Agency, “Quantum Key Distribution (QKD) and Quantum Cryptography,” USA
6 European Commission, “The European Quantum Communication Infrastructure (EuroQCI) Initiative”
7 Quantum Flagship
8 OpenQKD
9 Interoperable Europe (European Commission), “Rolling Plan for ICT Standardisation”
10 International Telecommunications Union (ITU), “FG-QIT4N - D2.3-Part 2 - Quantum Key Distribution Network Protocols: Key Management Layer, QKDN Control Layer and QKDN Management Layer,”
11 Zhao, B.; Liu, B.; Qu, C.; et al.; “,” Institute of Electrical and Electronics Engineers (IEEE) Xplore, 3 March 2016
12 Post-Quantum Cryptography Alliance
13 National Institute of Standards and Technology Computer Security Resource Center, FIPS 203 – Module-Lattice-Based Key-Encapsulation Mechanism Standard, USA, 13 August 2024, National Institute of Standards and Technology Computer Security Resource Center, FIPS 204 – Module-Lattice-Based Digital Signature Standard, USA, August 2024, National Institute of Standards and Technology Computer Security Resource Center, FIPS 205 – Stateless Hash-Based Digital Signature Standard, USA, 13 August 2024
14 National Institute of Standards and Technology Computer Security Resource Center, “Post-Quantum Cryptography”
15 Geer, D.; “NIST Post-Quantum Cryptography Candidate Cracked,” Communications of the ACM, 24 January 2023
16 Castryck, W.; Decru, T.; “An Efficient Key Recovery Attack on SIDH,” Cryptology ePrint Archive, 15 May 2023
17 National Institute of Standards and Technology (NIST), “NIST Announces First Four Quantum-Resistant Crytographic Algorithms,” 5 July 2022
18 MIT Technology Review, “How a Quantum Computer Could Break 2048-bit RSA Encryption in 8 Hours,” 20 May 2019
19 Berggren, K.; “Quantum Computing With Superconductors,” Proceedings of the IEEE, vol. 92, iss. 10, p. 1630–1638, 20 September 2004
20 Pezzagna, S.; Meijer, J.; “Quantum Computer Based on Color Centers in Diamond,” Applied Physics Reviews, vol. 8, iss. 1, 2021
21 Federal Office for Information Security, Study: Development Status of Quantum Computer Version 2.0, Germany, 13 November 2023
22 ETSI, “Electronic Signatures And Infrastructures (ESI), Algorithms and Parameters for Secure Electronic Signatures; Part 2: Secure Channel Protocols and Algorithms for Signature Creation Devices,” vol. 1, no. 2, 2005-2007
23 PKI Consortium, “PQC Capabilities Matrix (PQCCM)”
24 Apple Security Research, “iMessage with PQ3: The New State of the Art in Quantum-Secure Messaging at Scale,” 21 February 2024
25 Westerbaan, B.; “Sizing Up Post-Quantum Signatures,” Cloudflare, 08 November 2021
26 Westerbaan; "Sizing Up Post-Quantum”
DONAVAN CHEAH | CRISC, CISSP, OSCE3, OSCP
Is a senior cybersecurity consultant with Thales. He has spoken at conferences about various topics such as threat modeling with the system development life cycle (SDLC) and moderated C-suite panel discussions on contemporary cybersecurity topics. He is also the creator of a Thales cybersecurity gamification experience, "Defend the Breach.”
