In the rapidly evolving digital age, enterprises are grappling with shadow IT, which encompasses IT systems, devices, software, applications, and services used by employees without explicit approval.1 Employees often turn to such unauthorized alternatives to enhance productivity and overcome the limitations of sanctioned IT solutions, creating a parallel IT infrastructure that operates outside the official IT department’s control. This phenomenon presents both opportunity and significant risk for modern enterprises.
The prevalence of shadow IT in large enterprises is substantial, with studies suggesting that up to 40% of IT spending may be attributed to these unauthorized solutions.2 Factors driving this trend include the consumerization of IT, the proliferation of cloud-based services, and increasing employee tech savviness.3 Although shadow IT can promote innovation and agility, it can also lead to data security breaches, compliance violations, and inefficiency due to fragmented IT landscapes. The growing complexity of organizational IT environments complicates the management of shadow IT and underscores the need for robust data quality management integration.
Given shadow IT’s complex nature and significant impact on organizational performance, there is a pressing need for a comprehensive management framework. The framework discussed includes proactive anticipation strategies, effective identification processes, and adaptive management approaches. Practical recommendations are offered to help enterprises navigate the challenges of shadow IT while taking advantage of its innovative potential.
Understanding Shadow IT
Shadow IT must be distinguished from business-managed IT. The former involves IT solutions adopted without the IT department’s knowledge, while the latter refers to sanctioned but externally managed IT solutions.4 This distinction is crucial for determining appropriate management and governance strategies. Organizational shortcomings such as inadequate IT resources and slow response times often drive employees toward shadow IT, given its perceived benefits and ease of use.5 Although shadow IT can enhance productivity, innovation, and employee satisfaction, it can also pose risk, including data insecurity, regulatory noncompliance, and inefficiency.6 Balancing these pros and cons is essential for developing effective management strategies that harness the innovative potential of shadow IT while mitigating its associated risk.
Anticipating and Identifying Shadow IT
Managing shadow IT requires understanding the organizational factors contributing to its development, such as rigid IT policies, insufficient resources, poor communication between IT and business units, and slow adoption of new technologies.7 Enterprises can mitigate the likelihood of employees adopting shadow IT by fostering open communication and regularly assessing their IT resources and policies. These policies should include clear guidelines on the evaluation and approval process for new technologies, establish channels for employees to suggest IT solutions, outline the potential risk and consequences of using unauthorized systems, and provide a framework for integrating valuable shadow IT solutions into the official IT portfolio. Resources should encompass user-friendly documentation of approved tools, regular training on emerging technologies, and easily accessible support channels for IT-related inquiries. At the individual level, factors such as shadow IT’s perceived advantages and ease of use and employees’ job characteristics, IT experience, and attitudes toward organizational policies also play a role. Employees whose jobs require flexibility and creativity may be more inclined to adopt shadow IT solutions.8 This tendency stems from the nature of their work, which often demands rapid adaptation and innovative problem solving. Standard IT solutions may not always provide the agility or specialized functionality these employees require, leading them to seek more tailored or customizable shadow IT alternatives.
The consumerization of IT and the rise of bring-your-own-device (BYOD) policies also contribute to shadow IT, as employees seek to replicate high-tech personal devices and applications in their work environment, facilitated by user-friendly cloud services and mobile applications. Enterprises must consider these broader technological trends and the evolving landscape of shadow IT solutions when developing strategies to anticipate and manage shadow IT effectively.
Identifying shadow IT requires a multifaceted approach, including network traffic analysis, cloud access security broker (CASB) solutions, employee surveys and interviews, and IT asset management tools. Network traffic analysis can reveal unauthorized applications accessing enterprise networks, and CASB solutions offer visibility into the use of cloud services.9 Nonpunitive employee surveys and interviews can provide insights into the types of shadow IT used and the motivations behind their adoption. Despite these methods, however, challenges remain due to the dynamic nature of shadow IT, the difficulty of distinguishing authorized from unauthorized IT usage, and employee resistance due to fear of repercussions. Overcoming these challenges requires a nuanced approach that balances control with an understanding of employee motivations. Fostering a culture of transparency and trust helps encourage employees to disclose their use of shadow IT, providing valuable insights into the limitations of existing IT solutions and helping to refine official IT offerings and policies.
Although shadow IT can enhance productivity, innovation, and employee satisfaction, it can also pose risk, including data insecurity, regulatory noncompliance, and inefficiency. Balancing these pros and cons is essential for developing effective management strategies that harness the innovative potential of shadow IT while mitigating its associated risk.Managing Shadow IT
Effective management of shadow IT requires a balanced governance approach that addresses risk factors and potential benefits. Key strategies include developing clear policies and guidelines for the use of nonsanctioned IT solutions, implementing a formal evaluation process for shadow IT applications, establishing a cross-functional team to oversee shadow IT management, and regularly reviewing and updating the enterprise’s IT portfolio to incorporate valuable shadow IT solutions.10 These strategies should be used to create a framework for controlled innovation while maintaining security and compliance standards. Enterprises can harness shadow IT’s innovative potential while mitigating associated risk by establishing clear guidelines and processes for evaluating and potentially integrating shadow IT.
Managing shadow IT involves striking the right balance between control and flexibility. This can be achieved with a conceptual framework that distinguishes between shadow IT and business-managed IT and advocates for some management strategies based on unofficial IT usage. A nuanced approach enables enterprises to tailor their strategies to the specific characteristics of various unofficial IT solutions. Rather than simply eliminating shadow IT, enterprises can transform valuable shadow IT solutions into business-managed IT. This process includes assessing the value and risk of shadow IT solutions, formalizing the adoption of beneficial applications and integrating them with the existing IT infrastructure, and providing support and training.11 By embracing a flexible and adaptive approach to IT management, enterprises can create an environment where the benefits of shadow IT are realized within a controlled and secure framework, fostering responsible experimentation while ensuring compliance with security and regulatory requirements.12
A Holistic Framework for Shadow IT Management
Based on a comprehensive literature review and synthesis of best practices, a holistic framework for shadow IT management should encompass three key components: proactive anticipation strategies, effective identification processes, and adaptive management approaches (figure 1). This framework provides the tools and strategies needed to navigate the complex and dynamic nature of shadow IT, harnessing its innovative potential while effectively managing its associated risk.
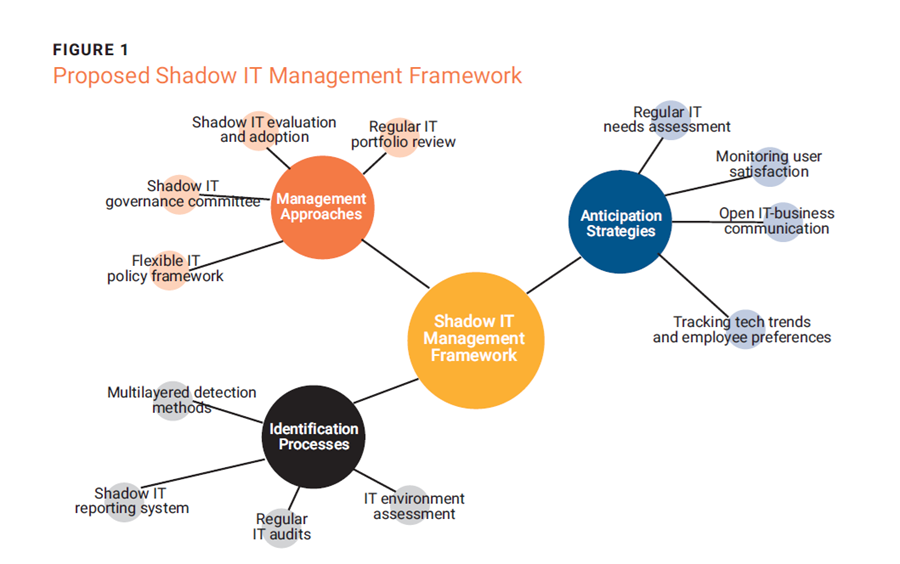
Proactive Anticipation
Strategies Proactive anticipation strategies involve regular assessment of organizational IT needs and user satisfaction, continuous monitoring of technology trends and employee preferences, and open communication channels between IT and business units.13 These strategies aim to address the root causes of the use of shadow IT before it becomes a significant issue. Enterprises can mitigate the likelihood of employees adopting shadow IT by fostering open communication and regularly assessing their IT resources and policies.
Effective Identification Processes
Effective identification processes include implementing multilayered detection methods, establishing a shadow IT reporting system, and performing regular audits and assessments of the IT landscape.14 These processes ensure that enterprises have a comprehensive and up-to-date understanding of their shadow IT ecosystems. Nonpunitive employee surveys and interviews can provide insights into the types of shadow IT used and the motivations behind their adoption.
Adaptive Management
Approaches Adaptive management approaches involve developing a shadow IT evaluation and adoption process, creating a shadow IT governance committee, and implementing a flexible IT policy framework.15 These approaches allow enterprises to respond dynamically to the challenges and opportunities presented by shadow IT. Rather than simply eliminating shadow IT, enterprises can transform valuable shadow IT solutions by formalizing the adoption of beneficial applications, integrating them with the existing IT infrastructure, and providing support and training.
Integration with Existing IT Governance
The proposed framework emphasizes integrating shadow IT management with existing IT governance structures.16 This involves aligning shadow IT management with the overall IT strategy, incorporating shadow IT considerations into IT risk management processes, and regularly reporting on shadow IT status to senior management. Enterprises can ensure a cohesive and comprehensive approach to managing the entire IT ecosystem by embedding shadow IT management within a broader IT governance framework.17 This holistic framework provides a comprehensive approach to managing shadow IT throughout its life cycle, from anticipation to integration or elimination.
Impact
The management of shadow IT has significant implications for IT governance and organizational agility, as diverse case studies across multiple industries reveal the complexity of this challenge and the need for nuanced, context-specific approaches. For example, due to the sheer scale and diversity of shadow IT usage, large enterprises require sophisticated detection methods and clear communication strategies, given the limitations of traditional, restrictive IT governance models in addressing the underlying drivers of shadow IT adoption.18
Similarly, a case study from the financial sector illustrates the balance between security compliance and employee productivity. The European Bank’s initial restrictive approach led to decreased employee productivity and increased dissatisfaction, emphasizing the limitations of such strategies. However, the bank improved security compliance and employee productivity by adopting a more nuanced approach, including formal evaluation processes for Shadow IT reporting system.19 These cases underscore the need for adaptive management strategies and more collaborative and flexible IT governance models.
Industry-specific considerations are crucial in managing shadow IT, as shown by a study in the healthcare sector. Shadow systems for patient data management in a university hospital posed significant privacy and regulatory risk. However, the hospital’s implementation of a cross-functional team to evaluate and integrate valuable shadow IT solutions demonstrated the potential for harnessing innovation while maintaining compliance.20 This approach aligns with the proposed framework’s emphasis on maintaining balanced governance and transforming shadow IT into business-managed IT. It also demonstrates how enterprises can turn shadow IT challenges into opportunities for innovation and competitive advantage.
Conclusion
Effectively managing shadow IT is crucial for maintaining IT governance and organizational agility in the modern digital landscape. By understanding the drivers of shadow IT adoption, such as organizational shortcomings and individual preferences, and by implementing proactive anticipation strategies, enterprises can address the root causes before they become significant issues. Effective identification processes, including multilayered detection methods and regular IT landscape audits, ensure a comprehensive understanding of shadow IT.
Adaptive management approaches, such as establishing governance committees and flexible IT policies, allow enterprises to harness the innovative potential of shadow IT while maintaining the necessary security and compliance standards. Integrating shadow IT management with existing IT governance frameworks creates a cohesive approach that balances control with flexibility, turning shadow IT challenges into opportunities for innovation and competitive advantage. Case studies from various industries demonstrate the effectiveness of this holistic framework, providing valuable insights and practical strategies for enterprises to navigate the complexities of shadow IT.
Endnotes
1 Silic, M.; Back, A.; “Shadow IT—A View From Behind the Curtain,” Computers & Security, vol. 45, 2014, p. 274–283
2 Zimmermann, S.; Rentrop, C.; et al.; “A Multiple Case Study on the Nature and Management of Shadow Information Technology,” Journal of Information Systems, vol. 31, iss. 1, 2017, p. 79–101
3 Gregory, R.W.; Kaganer, E.; et al.; “IT Consumerization and the Transformation of IT Governance,” MIS Quarterly, vol. 42, iss. 4, 2018, p. 1225-1229
4 Kopper, A.; Furstenau, D.; et al.; “Shadow IT and Business-Managed IT: A Conceptual Framework and Empirical Illustration,” International Journal of IT/Business Alignment and Governance, vol. 9, iss. 2, 2018, p. 53-71
5 Haag, S.; Eckhardt, A.; “Shadow IT,” Business & Information Systems Engineering, vol. 59, iss. 6, 2017, p. 469-473,; Nurfitriansyah; Munir; Disman; Dirgantari, P.; “Does Individual IT Experience Affect Shadow IT Usage? Empirical Evidence from Universities With Legal Entities in Indonesia,” Organizacija, vol. 56, iss. 3, 2023, 265-277
6 Mallmann, G.L.; Maçada, A.C.G.; et al.; “The Influence of Shadow IT Usage on Knowledge Sharing: An Exploratory Study With IT Users,” Business Information Review, vol. 35, iss. 1, 2018, p. 17-28, ; Walterbusch, M.; Fietz, A.; Teuteberg, F.; “Missing Cloud Security Awareness: Investigating Risk Exposure in Shadow IT,” Journal of Enterprise Information Management, vol. 30, iss. 4, 2017, p. 644-665
7 Furstenau, D.; Rothe, H.; et al.; “Shadow Systems, Risk, and Shifting Power Relations in Organizations,” Communications of the Association for Information Systems, vol. 41, 2017, p. 43-61
8 de Vargas Pinto, A.; Beerepoot, I.; et al.; “Encourage Autonomy to Increase Individual Work Performance: The Impact of Job Characteristics on Workaround Behavior and Shadow IT Usage,” Information Technology and Management, vol. 24, iss. 3, 2023, p. 233-246
9 Silic, M.; Barlow, J.B.; et al.; “A New Perspective on Neutralization and Deterrence: Predicting Shadow IT Usage,” Information & Management, vol. 54, iss. 8, 2017, p. 1023-1037
10 Furstenau, “Shadow Systems”; Haag, “Shadow IT”
11 Kopper, “Shadow IT and Business-Managed IT”
12 Tallon, P.P.; Queiroz, M.; et al.; “Information Technology and the Search for Organizational Agility: A Systematic Review With Future Research Possibilities,” Journal of Strategic Information Systems, vol. 28, iss. 2, 2019, p. 218-237
13 Furstenau, “Shadow Systems”; Haag, “Shadow IT”
14 Silic, “A New Perspective”
15 Kopper, “Shadow IT and Business-Managed IT”; Tallon, “Information Technology and the Search”
16 Zimmermann, “A Multiple Case Study”
17 Gregory, “IT Consumerization”
18 Silic, “Shadow IT—A View”
19 Haag, “Shadow IT”
20 Furstenau, “Shadow Systems”
TIMOTHY D. SPIVEY
Is currently pursuing a Ph.D. in business administration with an emphasis in business analytics at the University of South Alabama in Mobile, Alabama (USA). He has more than 15 years of experience in operations in the US cable industry. His research focuses on the intersection of data ethics and decision-making processes in information technology.
TIMOTHY R. MCILVEENE
Is an assistant professor of business administration at the University of West Florida in Pensacola, Florida (USA). His research interests include the ethical implications of emerging technologies. Before academia, he held leadership roles at Fortune 500 companies, including directing sales enablement for cloud and advanced technology sales. McIlveene is committed to bridging the gap between theory and practice.
