The audit process has drastically evolved over the years due to advances in technology and changes in the field. This includes the migration of systems and applications to cloud platforms and the exponential increase of systems that capture, store, and process personally identifiable information (PII), alongside intensified privacy regulations and an increasingly complex cybersecurity landscape.1 For the last decade, organizations have been immersed in digital transformation. This transformation includes the utilization of new technologies such as robotic process automation (RPA), artificial intelligence (AI), cloud computing, and Internet of Things (IoT), which have introduced new challenges in terms of how to audit these emerging technologies and mitigate the risk they present to organizations.2
From another perspective, organizations are experiencing the digital transformation of auditing itself, which includes using new technologies to improve the audit process and achieve continuous auditing, predictive auditing, and more. Furthermore, AI, natural language processing (NLP), and machine learning (ML) will play a crucial role in driving this transformation.3
Since the release of OpenAI’s ChatGPT4 and the popularization of large language models (LLMs), there has been an increasing interest in integrating these technologies into organizations to improve operational efficiency. There are many examples use cases and applications across various sectors, including software acquisition,5 code assessment and improvement,6 test generation,7 cybersecurity,8 and continuous account auditing.9
This context has set the stage for integrating audit with emerging technologies such as LLMs, which have the potential to revolutionize the audit process with greater accuracy, automation, and a proactive approach.
As LLMs become more widely adopted, organizations must explore and evaluate how these models can be applied within the field of information systems auditing. In other words, the focus must be on auditing with LLMs rather than auditing LLMs themselves. The question arises as to what extent these technologies can be integrated into the various phases of the audit process, from planning and execution to reporting and follow-up. It is critical to assess their potential to improve efficiency, accuracy, and effectiveness in risk identification and compliance. Organizations must identify areas where LLMs can add tangible value and where human intervention remains essential, ensuring alignment with established audit standards such as those outlined by ISACA® in the IT Audit Framework (ITAF).10 By strategically integrating LLMs, organizations can enhance the efficiency and effectiveness of their audit processes.
LLMs help auditors focus their efforts on the areas that present the greatest risk or require immediate attention.The analysis herein builds upon the typical audit process phases: Planning, Fieldwork and Documentation, and Reporting. Each phase in the audit process is subsequently divided into key steps (figure 1).
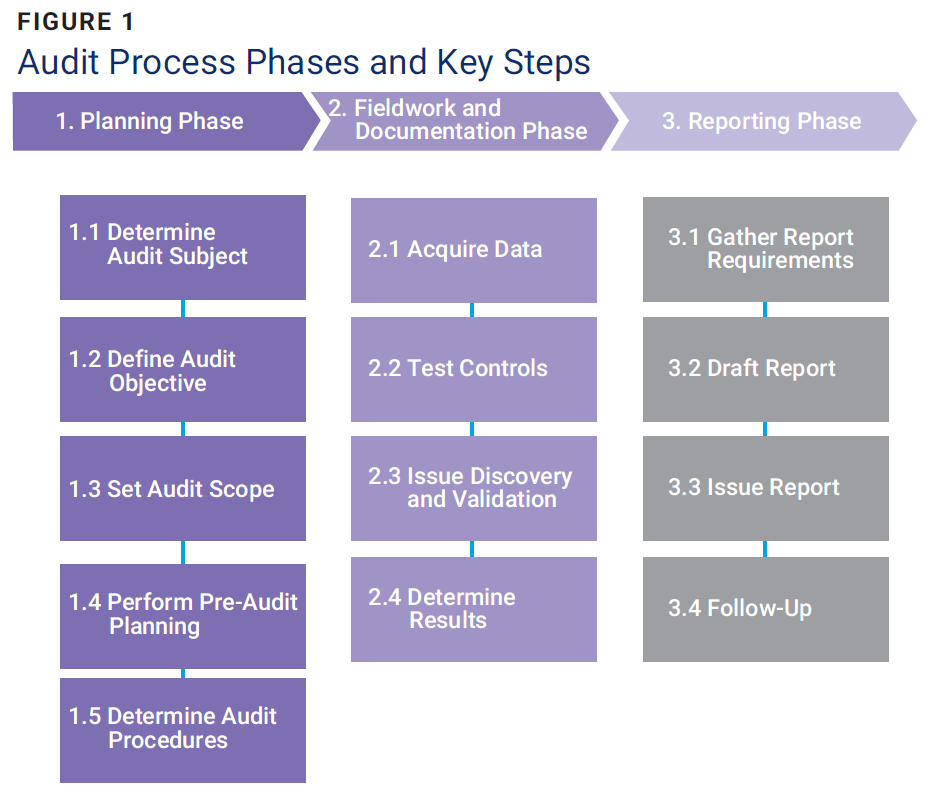
These foundational steps demonstrate how LLMs can be integrated effectively to augment and modernize the audit process.
Transforming Audit Planning with LLMs
The Planning Phase is a foundational step in an audit, as it defines the parameters and focus of the entire audit engagement.
1.1 Determine Audit Subject
In the Determine Audit Subject subphase, LLMs can enhance efficiency by identifying key audit areas. To achieve this, the LLMs are trained to analyze large volumes of historical data, including past audits, safety incident and risk logs, and other relevant documented data. LLMs analyze this data to identify patterns of recurring problems or areas that have not been sufficiently audited. This gives auditors a stronger basis for making strategic decisions about which areas to audit, as they must rely on objective, factual data rather than solely on intuition or previous experience.
In addition, LLMs can analyze historical data to identify emerging trends in the risk environment and regulatory landscape. This includes identifying new cyberthreats and changes in compliance regulations that could affect the organization. These models can anticipate trends, which enables auditors to stay one step ahead by focusing on emerging risk and ensuring that the organization is prepared for new threats. Further, LLMs assist organizations in maintaining compliance with updated regulatory requirements. For example, if an LLM detects an increase in ransomware attacks in the industry, it may suggest prioritizing audits in areas most vulnerable to ransomware attacks. Likewise, if there have been recent changes in regulations, the LLM might recommend the inclusion of compliance audits to ensure that the organization is aligned with these new regulations.
LLMs are also useful for mapping interdependencies when analyzing IT architecture and the relationships between systems or functions. This capability is crucial in complex IT environments, where a failure in one system can trigger a ripple effect in others. In this way, LLMs ensure that the audit encompasses both the obvious areas and those that could be critical due to their interactions with other systems.
This capability helps to prevent systemic failures that might not be evident without a thorough analysis of interdependencies.
Leveraging LLMs in the Determine Audit Subject subphase enables organizations to streamline the identification of audit areas, leading to more strategic and data-driven selections. By integrating predictive analytics and regulatory contextualization capabilities, LLMs help auditors focus their efforts on the areas that present the greatest risk or require immediate attention, thus ensuring a more effective audit that is aligned with the organization’s priorities.
1.2 Define Audit Objective
In the Define Audit Objective subphase, LLMs can assist in defining clear audit objectives that are aligned with relevant regulations and standards, such as the EU General Data Protection Regulation (GDPR),11 the US Sarbanes-Oxley Act (SOX),12 or the International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC) standard ISO/IEC 27001:2022 Information security, cybersecurity and privacy protection―Information security management systems―Requirement.13 LLMs can analyze regulations, industry standards, and internal policies to extract key requirements that must be met. This allows auditors to set objectives that align with regulatory expectations and the organization’s internal policies.
LLMs are also effective in creating risk-based objectives. By analyzing historical vulnerabilities and risk, LLMs can help define objectives that address the areas of greatest risk, ensuring that the audit focuses on the organization’s most vulnerable points.
Furthermore, LLMs can determine and adjust audit approaches tailored to different levels of exhaustiveness, formality, and rigor, depending on the specific needs of each process. If an audit involves high criticality or occurs in regulated environments, such as reviewing a financial system under SOX or GDPR, the LLM may recommend a comprehensive approach. This approach would include a detailed analysis of all transactions and records, rigorous technical testing, and thorough regulatory compliance checks. On the other hand, in a preliminary internal audit or routine low-risk reviews, the LLM may adjust the approach by suggesting a sampling method, concentrating efforts on areas with the highest probability of failure. This agile approach saves resources and time by focusing on only the most critical areas, avoiding the need to audit the entire system. Ultimately, LLMs adjust the recommended approach according to the auditor’s preferences but will also tailor the rigor and formality of the approach according to the objectives, ensuring that the process is efficient and relevant to the specific situation.
Utilizing LLMs in the Define Audit Objective subphase streamlines the process of establishing clear, regulation-aligned objectives and ensures that efforts are focused on the most critical aspects, facilitating a more precise and strategic approach.
1.3 Set Audit Scope
In the Set Audit Scope subphase, LLMs can help auditors identify critical systems, functions, units, and applications within the technology infrastructure. They can process and analyze many documents such as network maps, detailed asset inventories, application and system configuration logs, user and permission listings, activity logs, incident logs, and all relevant policies and procedures. With this information, LLMs can highlight key interdependencies between different components of the IT environment, identify potential weaknesses, or highlight areas that may be high risk. This helps auditors gain a more complete picture of the relationships between systems, allowing them to make more informed decisions about which areas should be included in the audit scope. This ensures that resources are focused on the areas of greatest criticality or vulnerability.
In addition, LLMs can help optimize resources. Defining audit scope includes considering the resources available, both in terms of time and the technical skills of the audit team. LLMs can suggest approaches that maximize the use of these resources, such as concentrating on areas where the team has the greatest expertise or recommending the use of automated tools to assist in more technical areas.
LLMs can optimize the scope of the audit by analyzing a wide variety of information related to the capabilities of the audit team, such as the number of staff available, their technical skills, and the time frames allotted to complete the audit. It can suggest optimizations based on resource and time constraints. For example, they can help identify which areas of the audit might require more or less time and effort. If the team is constrained, it can propose reallocating resources to the most critical areas, ensuring efficient use of resources.
In summary, LLMs can transform the audit scoping process by ensuring that it is accurate, focused, and aligned with available resources. By mapping technology interdependencies, prioritizing critical areas, and optimizing the use of resources, LLMs enable auditors to establish a scope that covers relevant points and maximizes audit effectiveness, ensuring a comprehensive and meaningful assessment.
1.4 Perform Preaudit Planning
In the Perform Preaudit Planning subphase, LLMs can automate the risk assessment, identifying critical areas that require further attention during the audit. This capability is essential for planning how to mitigate the areas of greatest risk and ensure an effective audit.
LLMs can also assist in generating interview questions by identifying areas of concern. LLMs can generate specific interview questions for auditors, ensuring comprehensive coverage of all issues, and record responses for further analysis.
Last, in resource and logistics planning, LLMs can recommend allocations for resources, budgets, and logistics, optimizing the planning process based on the complexity and scope defined. For example, during the planning of a cybersecurity audit, an LLM might identify the technical skills needed, such as cloud security knowledge, and suggest the inclusion of an expert in that field on the audit team.
1.5 Determine Audit Procedures and Steps for Data Gathering
In the Determine Audit Procedures and Steps for Data Gathering subphase, LLMs are essential to the development of customized audit tools. They can help develop scripts and tools that are tailored to the organization’s specific systems and technologies, ensuring that the tools are effective and meet the audit objectives.
LLMs are also helpful in the selection of assessment methods. Based on the risk identified, they can suggest the most appropriate assessment methods, such as penetration testing, access reviews, or log analysis.
In addition, LLMs can be integrated with existing systems to automate data collection for audits, ensuring the accuracy and completeness of the data. For example, while auditing the security of a database system, an LLM could automatically generate a script to assess security settings, identify users with elevated privileges, and analyze access logs for suspicious activity.
LLMs in Action: Enhancing Fieldwork and Documentation
The Fieldwork and Documentation Phase is the operational core of the audit, where data is gathered, controls are tested, issues are identified, and results are documented.
2.1 Acquire Data
The Acquire Data subphase benefits significantly from the use of LLMs during the fieldwork and documentation phase. LLMs can be integrated with the organization’s databases and systems to automate the collection of audit-relevant data. This includes extracting logs, activity logs, system configurations, and other necessary information. It should be noted, however, that granting LLMs access to sensitive audit data presents potential risk, such as unauthorized access, data leakage, privacy concerns, and regulatory compliance challenges, reinforcing the need for strong oversight and control measures to maintain data integrity.
LLMs can also verify the integrity of the acquired data, ensuring that there is no missing or corrupt data that could compromise the validity of the audit. For example, in a network security audit, an LLM could connect to network monitoring systems to extract access logs, firewall configuration change logs, and user activity data. By seamlessly connecting to these systems and logs, LLMs can validate that all required records are complete and unaltered.
2.2 Test Controls
In the Test Controls subphase, LLMs can generate and execute custom scripts to test the organization’s internal controls. These scripts can verify the effectiveness of access controls, application security settings, and the correct implementation of compliance policies. In addition, LLMs can analyze the results of these tests in real time, identifying any anomalies or control failures that require immediate attention. For example, in an audit of access controls, an LLM could run a script that verifies whether all access is limited to authorized personnel and whether session time and multifactor authentication (MFA) policies are being followed. By using this script, LLMs can immediately identify and report any noncompliance.
2.3 Issue Discovery and Validation
In the Issue Discovery and Validation subphase, LLMs can analyze control test results and acquired data to identify issues or failures that require attention. These discoveries can be automatically categorized according to their severity and potential impact on the organization. Moreover, LLMs can validate these findings against regulations, internal policies, and industry best practices to determine if they require immediate action. For example, if an LLM detects misconfigured access permissions on a critical system, it could generate a discovery report, categorizing the risk as high and recommending an urgent review by the IT team.
2.4 Document Results
In the Document Results subphase, LLMs can automate the writing of audit reports based on validated findings. These reports can be tailored for different audiences, from detailed technical reports for IT teams to executive summaries for senior management.
From Findings to Follow-Up: LLMs in Audit Reporting
The Reporting Phase is the final stage of the audit, where findings are compiled, documented, and communicated to relevant stakeholders, ensuring that the audit’s results are clear, actionable, and accessible.
3.1 Gather Report Requirements
In the reporting phase, during the Gather Report Requirements subphase, LLMs help identify the key requirements to be included in the audit report. LLMs can review internal policies, external regulations, and industry standards to extract these requirements, ensuring that the report meets all regulatory expectations and stakeholder needs. In addition, LLMs can customize the report by analyzing the needs of different audiences within the organization, suggesting the appropriate structure and content for each group. For example, when compiling requirements for an information security audit report, an LLM might suggest including specific sections on regulatory compliance, such as ISO/IEC 27001, key security related performance metrics, and anexecutive summary with strategic recommendations for senior management.
3.2 Draft Report
In the Draft Report subphase, LLMs can generate a draft audit report based on the data and findings obtained during the previous phases. This draft may include detailed descriptions of findings, risk analysis, and recommendations tailored to the style and tone appropriate for the intended audience. LLMs may also review the initial draft of the report to ensure consistency, clarity, and accuracy. This review may include identifying areas that require further detail or simplification and suggesting improvements in the wording to ensure that the report is understandable and persuasive. For example, in a compliance audit, an LLM might draft an initial report that describes the controls assessed, key compliance findings, and recommendations for improving risk management practices. The LLM can then fine-tune the language to make it accessible to the compliance team and board executives.
3.3 Issue Report
In the Issue Report subphase, LLMs can create different versions of the final report tailored to various audiences, such as senior management, the IT team, and external regulators. This ensures that each group receives the information it needs in a format that is easy to understand and apply. In addition, LLMs can automatically send the right report to the right people at the right time and keep a record of who received it. For example, when issuing an audit report on the security of an enterprise resource planning (ERP) system, the LLM could generate a detailed version for the technical team with control specifications, a summary version for senior management highlighting critical risk areas and key recommendations, and a compliance version to be sent to regulators. LLMs can even translate the report into different languages and adapt the content for various regions or regulations, ensuring that the results are understandable and applicable in all relevant contexts. For example, after completing the audit of an ERP system, an LLM could generate a detailed report of the findings, including an executive summary for senior management that explains key areas of concern and provides recommendations in a clear and concise manner. If the enterprise operates in multiple countries, the LLM could also translate the report into multiple languages to ensure understanding in all regions.
3.4 Follow-Up
In the Follow-Up subphase, LLMs can automate the process of implementing the corrective actions recommended in the audit report. They can also schedule and perform automatic follow-ups, send reminders to responsible parties, track the progress of implemented actions, and generate status reports for auditors and management. In addition, LLMs can analyze follow-up results to assess the impact of implemented corrective actions, identifying improvements in controls or areas that require further attention. For example, after an audit reveals access management deficiencies, an LLM can automate the follow-up on recommended corrections. This includes sending reminders to the IT team, generating periodic reports on the status of implemented improvements, and assessing whether these actions have effectively reduced the risk areas initially identified.
Navigating the Risk of LLMs in Auditing
There are potential risk factors that require careful management when integrating LLMs into the IT audit. Giving LLMs access to sensitive data can lead to unintended risk including unauthorized access and potential data leakage. Compliance becomes complex when LLMs inadvertently handle data outside legal boundaries.
Compliance becomes complex when LLMs inadvertently handle data outside legal boundaries.Data integrity and bias are additional sources of risk. Because LLMs learn from historical data, any biases or inaccuracies embedded in it can affect the results and reliability of audit findings. There is also a risk of overreliance on LLMs, which, while efficient, can result in less human oversight and a loss of the nuanced insights and professional judgment that are essential to a comprehensive audit. Another important consideration is that LLMs often operate as a “black box,” making it difficult for auditors to fully understand how decisions are made, which can have an impact on the confidence and accountability of the audit results.
Furthermore, linking LLM to multiple data sources increases the attack surface of the system and introduces vulnerabilities that could be exploited.
Given these risk scenarios, a balanced approach that combines robust security, data governance, and ongoing human oversight is essential.
Conclusion
LLMs have proven to be powerful tools that can significantly transform the way IT audits are conducted. By automating repetitive tasks, improving the accuracy of analysis, and providing data-driven insights, these models allow auditors to focus on more strategic and critical aspects of the audit.
However, it is important to recognize that while LLMs can increase the efficiency and effectiveness of the audit process, they cannot replace the expertise and professional judgment of the human auditor. The true potential of these tools is realized when they are combined with human insight to ensure audits that are both thorough and strategically aligned with organizational goals. Achieving this balance requires careful risk management that not only maximizes the benefits of LLM integration, but also ensures a secure, compliant, and effective audit environment.
As the technology environment continues to evolve and risk becomes more complex, LLMs offer a way to maximize productivity and quality in systems auditing. In a world where time is an increasingly valuable resource, LLMs can serve as valuable assistants, helping auditors navigate an increasingly complex digital environment and ensuring that organizations maintain a high level of security and compliance.
Endnotes
1 Sayana, S. A.; “The Evolution of Information Systems Audit” ISACA® Journal, vol. 1, 2022
2 Qureshi, M.A.; “Auditing Emerging Technologies: Facing New-Age Challenges,” ISACA Journal, vol. 2, 2020
3 Appelbaum, D., Kogan, A.; et al.; “Big Data and Analytics in the Modern Audit Engagement: Research Needs,” Auditing, vol. 36, iss. 4, 2017, p. 1-27, ; Menon, S.; “How Can AI Drive Audits?,” ISACA Journal, vol. 4, 2020
4 OpenAI, ChatGPT
5 Ballomo, S.; Zhang, S.; et al.; “Assessing Opportunities for LLMs in Software Engineering and Acquisition,” Carnegie Mellon University, Pennsylvania, UAS, 1 November 2023,
6 White, J.; Hays, S.; et al.; “ChatGPT Prompt Patterns for Improving Code Quality, Refactoring, Requirements Elicitation, and Software Design,” in Generative AI for Software Development, p. 71-108, Springer, 2024
7 M. Schäfer; S. Nadi; et al.; “An Empirical Evaluation of Using Large Language Models for Automated Unit Test Generation,” IEEE Transactions on Software Engineering, vol. 50, iss. 1, 2024, p. 85-105
8 Gupta, M.; Charankumar, A.; et al.; “From ChatGPT to ThreatGPT: Impact of Generative AI in Cybersecurity and Privacy,” IEEE Access, vol. 1, 2023
9 Huaxia, Li.; Machado de Freitas, M.; et al.; “Enhancing Continuous Auditing With Large Language Models: AI-Assisted Real-Time Accounting Information Cross-verification,” SSRN, 9 February 2024
10 ISACA, IT Audit Framework (ITAF), 4th Edition, 2020, https://www.isaca.org/itaf
11 Intersoft Consulting, “General Data Protection Regulation (GDPR),” https://gdpr-info.eu/
12 Fruhlinger, J.; “The Sarbanes-Oxley Act Explained: Definition, Purpose, and Provisions,” CSO, 30 November 2020
13 International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC), Joint Technical Committee on Information Technology (ISO/IEC JTC 1), ISO/IEC 27001:2022 Information security, cybersecurity and privacy protection – Information security management systems – Requirements, Edition 3, 2022, https://www.iso.org/standard/27001
DIEGO SUÁREZ | CISA, ISO/IEC 27001 LEAD ASSESSOR, TISAX LEAD AUDITOR
Is currently serving as a client manager at British Standards Institution (BSI), specializing in ISO/IEC 27001 and systems auditing. Suárez has been a volunteer at ISACA® and a member of the Board of Directors of ISACA Montevideo since 2021. Suarez was a former consultant in the information security department at NTT Data. He has also conducted financial and systems audits at the Supreme Audit Institution of Uruguay. He can be reached at diegosuarezperruccio@gmail.com.
MARIO PIATTINI | PH.D., CISA, CISM, CRISC, CGEIT, PMP
Is the director of the UCLM-Indra Joint Centre for Software Research and Development and the director of the Institute of Information Technologies and Systems. Piattini is a founder and member of several scientific and professional associations, such as the ISACA Madrid Chapter. He is also the author of dozens of papers and books on IT governance, data and software, quality, and IS audit. Piattini has received several computer science awards and is a founding partner of several companies and university spinoffs. He is a professor at the University of Castilla-La Mancha (Ciudad Real, Spain). He can be reached at mario.piattini@uclm.es.



