In the high-stakes world of cybersecurity, effective leadership is more important than ever. In 2024, global cybercrime costs are projected to reach US$9.5 trillion, underscoring the escalating severity of cyberthreats.1 This surge highlights the critical need for strategic foresight and adaptability in cybersecurity leadership. As cyberthreats grow in sophistication and scale, drawing insights from unconventional sources can offer a fresh perspective. One such timeless source is Sun Tzu’s The Art of War.2 Written more than 2,500 years ago, its principles of warfare have proven adaptable to various modern-day challenges, including cybersecurity.
Sun Tzu’s strategic philosophy centers around knowledge, preparation, and adaptability—qualities that are vital for cybersecurity leaders navigating today’s digital battlefield. Just as Sun Tzu emphasizes understanding the enemy, anticipating their moves, and knowing oneself, cybersecurity leaders must master the evolving threat landscape and the capabilities of their own teams.
Leaders must continually evaluate their defenses to adapt to the ever-changing tactics of cybercriminals.There are actionable insights for effective cyberleadership that can be gleaned by exploring select examples of Sun Tzu’s enduring leadership principles (figure 1). Applying these ancient lessons to modern challenges enables cybersecurity leaders to enhance their preparedness and respond to daily threats.
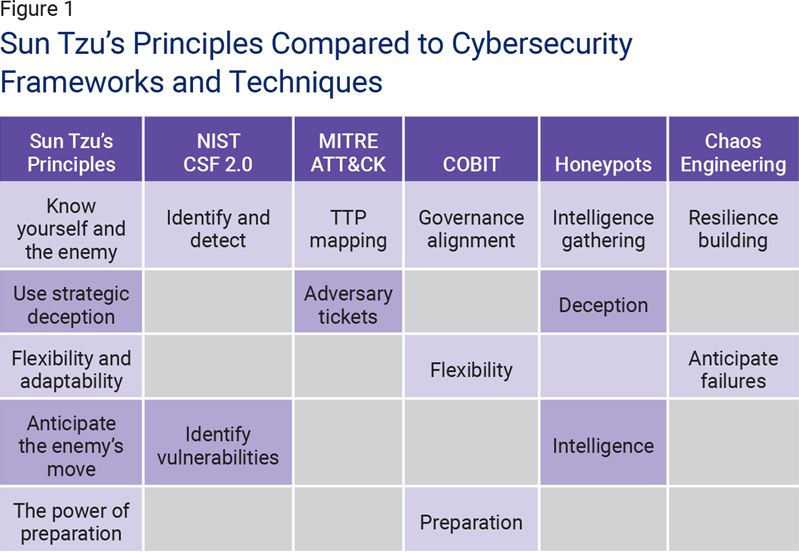
Understanding the Threat Landscape
To lead effectively in cybersecurity, it is crucial to understand the constantly evolving threat landscape. Similar to Sun Tzu in The Art of War, modern leaders must prioritize strategy, foresight, and adaptability. Sun Tzu’s wisdom on knowing both the enemy and oneself is highly relevant to cybersecurity. He famously stated, “If you know the enemy and know yourself, you need not fear the result of a hundred battles.”3 This principle underscores the need for cybersecurity leaders to understand both their organizations’ strengths and the external threats they face. Just as Sun Tzu assessed the terrain and capabilities of his forces and adversaries, leaders must continually evaluate their defenses to adapt to the ever-changing tactics of cybercriminals.
To address modern cyberthreats, many organizations utilize MITRE ATT&CK.4 This comprehensive knowledge base categorizes the tactics, techniques, and procedures (TTPs) used by adversaries in various stages of an attack (figure 2). It serves as a modern-day map that helps leaders understand the lay of the land, identify vulnerabilities, and predict potential attack strategies.
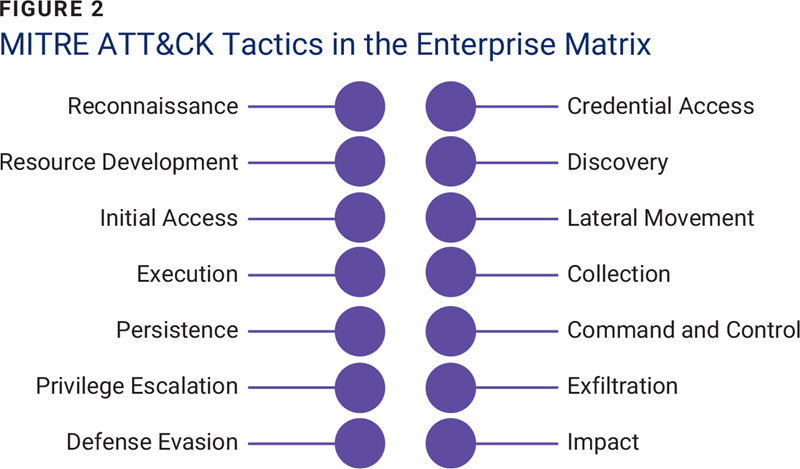
Sun Tzu’s principle of deception also aligns with the importance of understanding attacker behavior. “All warfare is based on deception,”5 he wrote, underscoring the need for strategy and unpredictability. Similarly, ATT&CK enables cybersecurity leaders to stay one step ahead of adversaries by categorizing known methods of attack and helping devise countermeasures that exploit weaknesses in the enemy’s approach.
Leaders can implement ATT&CK by integrating it into their threat modeling and risk assessment processes. This allows organizations to anticipate potential attack vectors and create more tailored defense mechanisms. Additionally, using the knowledge base to refine incident response strategies improves the ability to detect and neutralize threats more quickly and effectively. Finally, incorporating these tactics into employee training builds a culture of readiness and vigilance, ensuring that teams are fully equipped to recognize and respond to cyberattacks.
By blending Sun Tzu’s ancient wisdom with modern tools such as ATT&CK, cybersecurity leaders can cultivate a proactive defense strategy that keeps their organization secure in an increasingly hostile digital landscape.
Building Trust and Loyalty
Having frameworks and policies in place, while important, cannot guarantee security without cultivating an organizational culture that prioritizes readiness and adaptability.
For cybersecurity leaders, trust is the cornerstone of resilience. In both warfare and cybersecurity, success depends not only on the loyalty of internal teams but also on the trust of external partners and stakeholders. Sun Tzu’s strategies emphasize commanding respect while fostering deep trust, ensuring a united front against adversaries.
Building trust across teams, partners, and stakeholders strengthens an organization’s ability to not only follow frameworks but also to respond dynamically to emerging threats, maintaining a resilient security posture.
Cybersecurity leaders must build trust by demonstrating competence, protecting organizational assets, and outlining clear, actionable strategies to address cyberthreats.Cybersecurity leaders must build trust by demonstrating competence, protecting organizational assets, and outlining clear, actionable strategies to address cyberthreats. A team—and broader network—that trusts its leadership will be more cohesive, better prepared to manage risk, and more effective in collaborating against evolving threats.
A compelling example is Mastercard’s Fusion Center, an initiative designed to enhance global cybersecurity through advanced threat intelligence and response capabilities. The Fusion Center integrates real-time data from across Mastercard’s network to detect and respond to potential threats swiftly. This initiative has proven effective, reducing fraud rates and improving incident response times significantly.6
Mastercard’s Fusion Center aligns with Sun Tzu’s principles of vigilance and preparedness. By continuously analyzing threat patterns and employing sophisticated tools for detection and prevention, Mastercard ensures that trust within the organization is maintained through proactive measures. Employees and partners understand that robust security protocols are in place to protect everyone involved, thereby fostering a sense of loyalty and commitment.
By implementing initiatives such as the Fusion Center, cybersecurity leaders can create an environment where trust is earned through action, communication, and accountability. Just as Sun Tzu’s disciplined armies thrived on mutual respect and loyalty, today’s cybersecurity teams can excel when led with transparency and a focus on trust.
Preparedness is key to success.Loyalty, too, is essential. In Sun Tzu’s military philosophy, loyalty was fostered through mutual respect and integrity. A loyal cybersecurity team will not only follow protocols but also proactively seek ways to strengthen the organization’s defenses. Loyalty in cybersecurity is reflected in adherence to security best practices, early incident reporting, and commitment to the organization’s security vision. Leaders who cultivate loyalty will inspire their teams to go beyond mere compliance and contribute meaningfully to the organization’s overall security culture.
Just as Sun Tzu relied on the loyalty of his army to maintain a powerful, unified force, cybersecurity leaders must ensure that their team is well-trained and vigilant in the face of threats. Whether dealing with external attackers or internal risk, a team united by trust and loyalty will be more resilient. Cybersecurity threats, much like challenges faced on the battlefield, demand the collective effort of a dedicated and loyal team.
In both military strategy and cybersecurity leadership, trust and loyalty are essential pillars of success. Without these elements, even the best laid plans can collapse under persistent threats.
Beyond Hope: Building a Strategy Based on Readiness
Sun Tzu’s wisdom, “The art of war teaches us to rely not on the likelihood of the enemy not coming, but on our readiness to receive him,”7 underscores a fundamental principle of cybersecurity leadership: Preparedness is key to success. In today’s threat landscape, cybersecurity leaders must guide their organizations toward readiness and proactive defense, rather than relying on the hope that attacks will not happen. Leadership plays a pivotal role in instilling a culture of vigilance, empowering teams to anticipate and counteract threats before they materialize.
Cybersecurity leadership is responsible for integrating advanced defense strategies, such as honeypots and chaos engineering, into the organization’s security framework.
Honeypots
Honeypots, decoy systems designed to lure and trap malicious actors, provide valuable insights into the TTPs used by attackers. By spearheading the deployment of honeypots, leaders ensure that their teams are not passively awaiting an attack, but rather, are actively gathering intelligence that strengthens their security posture.
Honeypots may be placed in various layers of the organization to maximize their effectiveness:
- Honeypots in the network layer monitor unauthorized access attempts and malicious traffic. Leaders ensure that these tools are implemented to simulate vulnerable services, attracting attackers and providing critical data for defense strategies.
- Honeypots in the application layer proactively capture application-specific threats, enabling organizations to stay ahead of emerging vulnerabilities and adapt their security defenses accordingly.
- Honeypots in the endpoint layer are deployed on workstations and servers, allowing organizations to gain visibility into malware targeting endpoints and fine-tune endpoint security and containment strategies.
One prominent example of the successful use of honeypots is the Honeynet Project,8 an international cybersecurity research initiative. The project uses a network of unmodified computers with the same specifications, operating systems, and security measures as those used by many enterprises to serve as honeypots to track cybercriminal activity, analyze malicious software, and uncover new attack patterns. Through the leadership of cybersecurity experts, the Honeynet Project has exposed significant threats, including botnets and zero-day vulnerabilities, which have helped organizations worldwide strengthen their defenses and improve incident response capabilities.
Chaos Engineering
In addition to deploying honeypots, effective cybersecurity leaders must embrace and champion innovative approaches such as chaos engineering. This involves intentionally introducing system disruptions to rigorously evaluate and fortify the resilience of their infrastructure. By adopting such bold and forward-thinking methods, leaders reveal vulnerabilities under controlled conditions, thereby equipping their organizations to better withstand real-world cyberthreats. For example, tools such as Netflix’s Chaos Monkey9 and Security Monkey10 exemplify how leaders can apply chaos engineering principles to rigorously enforce security policies and enhance system reliability. These tools demonstrate the critical role of adopting courageous and inventive strategies to maintain secure, fault-tolerant environments, ultimately ensuring that cybersecurity defenses are not merely reactive but proactively robust.
Cybersecurity leaders do more than implement tools—they cultivate a mindset focused on readiness, aligning with Sun Tzu’s philosophy that success comes from preparation, not assuming the enemy will not attack. Effective leadership fosters strategic foresight, turning cybersecurity into a proactive, intelligence-driven approach that ensures long-term resilience against evolving threats.
Effective leadership fosters strategic foresight, turning cybersecurity into a proactive, intelligence-driven approach that ensures long-term resilience against evolving threats.Navigating Ethical Challenges in a Digital Age
Sun Tzu’s timeless insight, “Regard your soldiers as your children, and they will follow you into the deepest valleys; look on them as your own beloved sons, and they will stand by you even unto death,”11 offers profound guidance for cybersecurity leaders. This principle highlights the deep connection between leadership, trust, and ethical responsibility. In the rapidly evolving digital age, where cyberthreats loom large and decisions carry significant consequences, this philosophy becomes essential for navigating the ethical complexities inherent in cybersecurity leadership.
The modern cybersecurity leader must recognize that their role extends far beyond technical expertise; it requires a commitment to ethical decision making that places people—whether employees, users, or stakeholders—at the center of every action. Sun Tzu reminds us that, just as a military leader must care for their soldiers, a cybersecurity leader must prioritize the well-being of their team and the broader community, fostering trust and loyalty through ethical leadership.
In the digital age, where data privacy and security are paramount, cybersecurity leaders face an array of ethical challenges. Users entrust organizations with their most sensitive information, from personal details to financial records. The misuse or mishandling of such data can result in breaches of trust that have long-lasting repercussions. Ethical leadership, therefore, is about more than just preventing attacks; it is about ensuring transparency, respecting privacy, and protecting the rights of users.
A September 2024 report from the US Federal Trade Commission (FTC) highlights the urgent need for rigorous privacy protections, especially for vulnerable groups such as children and teens. The FTC found that major social media and video streaming platforms have engaged in extensive data collection on young users without implementing adequate safeguards.12 This breach of trust underscores the importance of strategic foresight and adaptability in cybersecurity leadership, principles long championed by Sun Tzu. His teaching on “knowing the enemy and knowing oneself” serves as a reminder that organizations must be vigilant in identifying both external threats and internal vulnerabilities to effectively protect user data. This example illustrates the real-world consequences of failing to prioritize robust cybersecurity measures, reinforcing the need for proactive and ethical leadership in the digital landscape.
Cybersecurity leadership in the digital age requires navigating complex ethical dilemmas, particularly when responding to active threats. Whether dealing with ransomware, data breaches, or insider threats, leaders must make swift decisions that have far-reaching consequences. The pressure to act quickly can often lead to ethical shortcuts, but Sun Tzu’s principle urges caution—true leadership is about guiding your people through the toughest challenges with integrity.
For example, during a cybercrisis, a leader might face the temptation to hide a breach from the public to avoid reputational damage. However, ethical leadership would require transparency, communicating openly about the incident and taking responsibility for its impact. This approach not only aligns with moral principles but also strengthens long-term trust with stakeholders, demonstrating that the organization is committed to doing what is right, even in the face of adversity.
In September 2023, MGM Resorts faced a significant cyberattack that disrupted operations across its properties.13 The company chose not to pay the ransom demanded by the attackers, leading to substantial financial losses and reputational challenges. This incident underscores the importance of ethical leadership in cybersecurity. By refusing to capitulate to cybercriminals, MGM Resorts demonstrated a commitment to integrity and transparency, aligning with Sun Tzu’s principle of maintaining moral authority. This approach not only upholds ethical standards but also fosters long-term trust with stakeholders, reinforcing the organization’s dedication to doing what is right, even in the face of adversity.
Sun Tzu’s teachings offer a reminder that leadership is about protecting those who rely on you. In cybersecurity, this means not only safeguarding systems and data but also protecting the people behind them. Ethical cybersecurity leadership involves recognizing that every security decision impacts real individuals—whether they are employees, customers, or the general public. Leaders must therefore approach their role with a deep understanding of responsibility, ensuring that their actions are always in service of the greater good.
This responsibility extends to the ethical use of technologies such as artificial intelligence (AI), encryption, and biometric data. As organizations adopt these advanced tools, cybersecurity leaders must consider the broader ethical implications of their use. By ensuring that these technologies are deployed responsibly and transparently, leaders can protect user privacy while still maintaining robust security measures. For instance, cybersecurity leaders can utilize the Ethics Guidelines for Trustworthy AI by the European Commission14 to guide their implementation of AI systems. These guidelines provide specific requirements (figure 3), such as ensuring transparency in AI decision-making processes and maintaining rigorous data privacy standards.
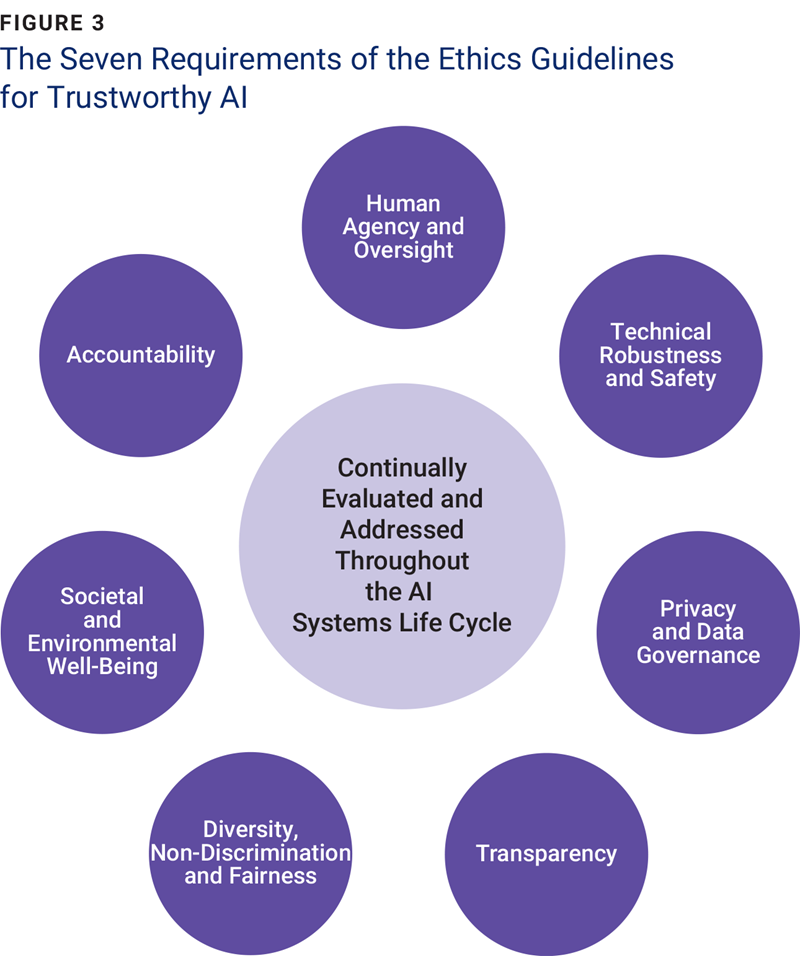
By adhering to these guidelines, leaders can develop AI systems that not only enhance security but also respect and protect user rights, fostering greater trust and compliance with ethical standards.
Conclusion
In today’s rapidly evolving digital landscape, the wisdom of Sun Tzu provides timeless guidance for cybersecurity leaders. His principles of preparation, adaptability, and strategic foresight resonate with the ongoing challenges in defending against sophisticated cyberthreats. As cybercriminals advance their techniques, cybersecurity leaders must stay ahead by cultivating resilience, making informed decisions, and fostering a culture of continuous improvement.
Strategic foresight is a crucial leadership challenge in cybersecurity. Sun Tzu’s belief in the power of preparation and anticipation resonates with today’s need for foresight in detecting and countering cyberthreats. His concept of “winning without fighting”15 applies to cybersecurity as proactive measures such as strengthening defenses and identifying vulnerabilities before they can be exploited.
Building trust and loyalty is another key tenet of Sun Tzu’s teachings. He recognized that a leader’s strength comes from the loyalty and commitment of their soldiers. Similarly, cybersecurity leaders must foster a culture of trust within their teams to ensure seamless collaboration. A united team, armed with a shared sense of purpose, is more resilient and capable of facing the unpredictable nature of cyberthreats.
Swift and decisive decision making under pressure is a skill both Sun Tzu and modern cybersecurity leaders must possess. In a fast-moving cyberattack, waiting too long to act can lead to devastating consequences. Sun Tzu’s advice to “move swiftly where you are not expected”16 applies to cybersecurity by encouraging rapid, well-informed responses that can neutralize threats before they escalate.
Finally, adaptability is key to winning any war, and cyberwarfare is no exception. Just as Sun Tzu stressed the importance of adapting strategies based on changing circumstances, cybersecurity leaders must remain agile to address emerging threats and new technologies.
Success in this domain depends on the ability to evolve continuously, keeping defenses strong and attackers off balance. Success in cyberdefense goes beyond mere reaction. It requires forward-thinking strategies that anticipate risk and protect what matters most: user trust and data. Ethical leadership, grounded in transparency and accountability, remains crucial for building this trust and maintaining robust security.
Ultimately, the best defense is one that neutralizes threats before they strike. By embracing innovation, foresight, and integrity, cybersecurity leaders can lead their organizations through the complexities of the modern threat landscape, transforming defense into an art that mirrors the wisdom of ancient strategy.
Endnotes
1 Morgan, S.; “Cybercrime to Cost the World $9.5 Trillion USD Annually in 2024,” Cybercrime Magazine, 25 October 2023
2 Tzu, S.; The Art of War, translated by Lionel Giles, CreateSpace Independent Publishing Platform, 24 November 2020
3 Tzu; The Art of War
4 MITRE, Getting Started With ATT&CK, 2019
5 Tzu; The Art of War
6 Security Magazine, “A Nucleus of Information-Sharing: Mastercard’s Fusion Center,” Security Magazine, 8 August 2018
7 Tzu; The Art of War
8 The Honeynet Project, “The Honeynet Project,”
9 Netflix, “Chaos Monkey”
10 Netflix, “Security Monkey”
11 Tzu; The Art of War
12 FTC, “FTC Staff Report Finds Large Social Media and Video Streaming Companies Have Engaged in Vast Surveillance of Users with Lax Privacy Controls and Inadequate Safeguards for Kids and Teens,” USA, 19 September 2024,
13 Freeh, L.J.; Mukasey, M.B.; “MGM Grand Casino: Hacked by Criminals, Probed by the FTC,” The Wall Street Journal, 10 April 2024
14 European Commission, Ethics Guidelines for Trustworthy AI, European Union, 8 April 2019
15 Tzu; The Art of War 16 Tzu; The Art of War
16 Tzu; The Art of War 16 Tzu; The Art of War
ABDELELAH ALZAGHLOUL | CISA, CISM, CGEIT, CRISC, ITIL 4 MP, ITIL 4 SL
Is an IT advisor with 20 years of experience in IT governance, service delivery, and IT transformation programs. He is experienced in the deployment of various IT governance frameworks and standards in the telecommunications sector. He is also a certified trainer in IT governance and service management and a contributing reviewer for the ITIL Maturity Model.
