

In the landscape of enterprise technology, Systems, Applications, and Products (SAP) has played a key role as a reliable platform supporting business operations of more than 400,000 enterprises globally.1 This reach spans organizations of all sizes and industries, from local small and medium sized enterprises (SMEs) to multinational conglomerates.
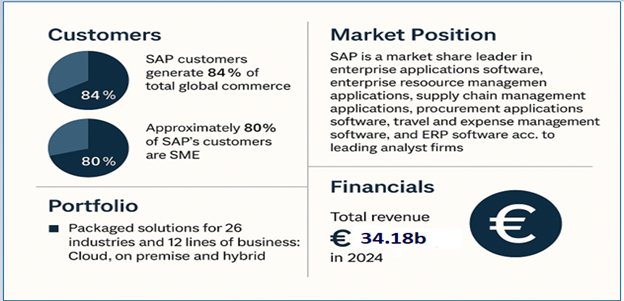
The relevance of SAP extends beyond finance and logistics. With its packaged solutions tailored for 26 industries and 12 lines of business, SAP delivers integrated tools for manufacturing, life sciences, public services, retail, and more. It is a leader in critical enterprise categories including enterprise resource planning (ERP), supply chain management (SCM), procurement, travel and expense management, and enterprise application software. Figure 1 illustrates that approximately 80% of its customers are SMEs, demonstrating its adaptability and accessibility. Financially, SAP reported a total revenue of €34.18 billion in 2024,2 affirming its performance and ongoing relevance in a rapidly evolving tech economy.
Figure 1—SAP Fast Facts
SAP functions as more than just a software provider, supporting organizations in areas such as operational efficiency, regulatory compliance, sustainability initiatives, and long-term growth. As digital transformation continues to evolve globally, SAP’s role as a technology partner remains vital—helping organizations navigate an increasingly complex landscape and manage risk, including critical vulnerabilities that could threaten enterprise operations. Because SAP systems are highly valuable targets for malicious actors, organizations must prioritize securing them.
The Importance of SAP
SAP's importance can be distilled into 3 key elements:
Comprehensive business integration—SAP touches nearly every aspect of an enterprise’s business processes, from finance and accounting to logistics and customer relationship management (CRM). One example where this is especially evident is travel and expense management, as seen in Nestle's adoption of SAP Concur solutions. This automation significantly reduced manual tasks, allowing employees to submit expense claims more easily and speeding up reimbursements. Following a successful global rollout, Nestlé has entered a new era of streamlined and controlled travel and expense operations.3
Sensitive data and process ownership—SAP systems hold sensitive employee data, confidential contracts, intellectual property, and real-time transactional data. For regulated industries, such as pharmaceuticals, defense, and utilities, SAP environments often contain data governed by compliance frameworks such as the Sarbanes–Oxley Act (SOX), EU General Data Protection Regulation (GDPR), and the US Health Insurance Portability and Accountability Act (HIPAA). For example, Pfizer Inc., a global leader in pharmaceuticals and biotechnology, recognized the importance of strengthening its governance, risk, and compliance (GRC) framework to support its growth. By adopting continuous control monitoring and access governance using applications such as SAP Process Control and SAP Access Control, Pfizer was able to transition from multiple market-specific audits to a unified, centralized global audit powered by advanced analytics. This transformation enhanced efficiency, minimized errors, and delivered more effective audit results.4
Complexity and customization—Unlike off-the-shelf software, SAP provides a wide range of customization options, enabling organizations to adapt the ERP system to their specific processes and needs. Customizations can have long-term implications, so it is important to consider the approach and understand the associated costs.5
Given these traits, SAP cannot be considered just another enterprise application, it is often the very core of business continuity and competitiveness. A SAP compromise can lead to manufacturing delays, corruption of financial ledgers, or the leakage of trade secrets which all have devastating consequences. Hackers and nation-state attackers target SAP because it holds critical business data and processes. They seek financial gain through data theft, fraud, or ransomware attacks. Organizations must be aware of these threats and proactively secure SAP platforms with the understanding that not doing so will inevitably lead to deleterious consequences.
The Alarm Bell: CVE-2025-31324 in SAP NetWeaver Visual Composer
SAP systems are increasingly under siege. As demonstrated by the recent disclosure of a critical vulnerability, CVE-2025-31324,6 cybersecurity professionals must double down on defending SAP systems like never before. A common vulnerabilities and exposures (CVE) is a unique identifier assigned to a publicly known cybersecurity vulnerability, serving as a standardized reference for security professionals to discuss specific flaws. Alongside this, the common vulnerability scoring system (CVSS) provides a numerical score, from 0 to 10, that measures the severity and potential impact of a vulnerability. On April 2025, SAP issued a patch for CVE-2025-31324, a newly discovered critical vulnerability in the SAP NetWeaver Visual Composer component. The vulnerability was assigned a CVSS score of 10.0, the highest possible severity rating, indicating an urgent and potentially devastating risk.
What CVE-2025-31324 Signals About SAP Cybersecurity
This is not the first time SAP has faced a critical vulnerability, and it will not be the last. CVE-2025-31324 is part of a broader trend in which attackers increasingly target business logic, application programming interfaces (APIs), and upload functions within enterprise applications. It also underscores several key truths:
Perimeter security is no longer enough. Unauthenticated upload vulnerabilities in SAP applications are a major security risk, especially when these systems are connected to the internet, even indirectly. Hackers can take advantage of these flaws to upload harmful files, slipping past normal security defenses. Many organizations rely on firewalls and virtual private networks (VPNs) to protect SAP systems, but these are not always enough to stop more advanced attacks, such as CVE-2025-31324, that target weaknesses within the applications themselves. To reduce the risk, organizations must do more than just rely on perimeter security. Instead, organizations should use specialized SAP threat detection tools, keeping a close eye on organizational systems, and making sure system configurations are locked down and secure. Taking these steps will help organizations detect threats early and keeps vulnerable enterprise applications safer.
Zero trust must extend to SAP. Unauthorized access to SAP systems can result in data breaches, fraud, and significant operational disruptions. Without strong access controls and ongoing monitoring, attackers, and even well-meaning employees, can misuse sensitive SAP functions without being detected. While many organizations have basic access controls in place, they often lack detailed privilege management, strong authentication methods, and sufficient visibility into internal SAP activity, creating security blind spots that increase risk. To close these gaps, enterprises should adopt a zero trust architecture7 ,which means never automatically trusting any user or device, even those inside the network, and always verifying every access request. This approach involves enforcing least privilege access, ensuring users only have the permissions they absolutely need, implementing multifactor authentication (MFA) for an extra layer of protection, and continuously monitoring SAP activity using native logs and threat detection tools to quickly identify and respond to suspicious behavior.
Patching discipline is crucial. Unpatched vulnerabilities in SAP systems—especially those classified as critical and high priority—pose a serious risk, as attackers can exploit them to gain unauthorized access, disrupt operations, or steal sensitive data. Delays in applying patches leave these systems vulnerable to known threats. Although organizations understand the importance of patching, SAP environments often experience delays due to complex system dependencies, extensive testing requirements, and a lack of dedicated resources. Slow patch management processes create a larger window of exposure for potential attacks. To address this, enterprises need to implement disciplined and efficient patch management processes tailored to SAP systems, prioritizing critical patches and automating deployment where possible to minimize risk and strengthen overall security.
Security must be embedded in DevOps and change management. During SAP project rollouts, upgrades, or customization efforts, there is an increased risk that security controls may be overlooked, misconfigured, or bypassed, whether intentionally or unintentionally, thus creating vulnerabilities that attackers can exploit. These projects are often driven by functional or technical teams with limited input from security experts, which means critical security issues may be addressed too late or missed altogether, raising risk after deployment. To mitigate this, security professionals need to be involved throughout the entire SAP project lifecycle from planning and design to deployment and testing, ensuring that security controls are properly integrated, risk is continuously assessed, and compliance requirements are met without compromise.
Ways to Secure SAP Environments
Just as organizations protect other critical endpoints such as laptops, servers, and cloud services, they must safeguard SAP systems with the same level of vigilance. These systems are the lifeblood of modern business operations, and their compromise can be catastrophic. To secure SAP environments effectively, organizations must take several measures:
Manage inventories and define security baselines—The first step in securing any SAP landscape is visibility. Organizations must maintain a complete and up-to-date inventory of all SAP systems, components, interfaces, and related applications. With this inventory in place, security teams can establish system-specific baselines that define the minimum acceptable security standards, such as password policies, logging requirements, and access controls. These baselines provide a benchmark for compliance and a foundation for continuous improvement in an organization’s security posture.
Implement centralized monitoring and threat detection—Continuous system monitoring is essential to early threat detection. Security teams should monitor key indicators, such as debug change actions, failed login attempts, unusual transaction patterns, or changes to critical configurations. Establishing real-time alerting and automated responses helps reduce detection and response times.
Enforce secure application integration—Many SAP environments interact with third-party systems and applications. To manage the risk introduced by these interfaces, organizations should establish policies outlining minimum security requirements for any application connecting to SAP systems. These requirements should include secure communication protocols, strong authentication methods, and appropriate authorization controls. Ensuring these integrations are securely configured helps reduce the risk of external compromise via poorly secured interfaces.
Strengthen access control with least privilege and MFA—Access control remains one of the most critical components of SAP security. Implementing the principle of least privilege ensures that users only have the access necessary for their roles. Special attention should be given to privileged users, such as administrators and developers. Additionally, implementing MFA for sensitive transactions and high-privilege accounts adds an important layer of protection. MFA is particularly effective in mitigating risk from compromised credentials and phishing attacks.
Establish secure development and code lifecycle policies—Custom advanced business application programming (ABAP) developments are common in SAP environments, but they can introduce security vulnerabilities if not properly managed. Organizations should define policies that govern the full lifecycle of ABAP code—from development and testing to deployment and retirement.
Educate end users on cyber hygiene and fraud awareness—End users play a critical role in maintaining the overall security of SAP systems, as many security incidents originate from human error or lack of awareness. Ensuring that users understand the risk associated with their daily activities is essential for reducing exposure to threats such as phishing, social engineering, and the misuse of SAP transactions. Regular awareness training should be integrated into the organization’s security strategy, covering topics such as recognizing suspicious emails, protecting login credentials, and following proper procedures when accessing or handling sensitive data. Additionally, training should be tailored to user roles to ensure relevance and effectiveness. By promoting informed behavior and reinforcing best practices, organizations can strengthen the human layer of defense within SAP environments.
Formalize SAP patch management—To effectively manage vulnerabilities within SAP environments, organizations should formalize their SAP patch management process. SAP releases monthly security updates, known as “SAP Security Notes”, which address newly identified risk across SAP platforms. A well-defined patch management policy should include regular monitoring of SAP Security Patch Day announcements,8 assessing the risk and applicability of each patch, and conducting thorough testing in controlled environments before deployment. Ensuring timely implementation of relevant patches into production systems is critical. This structured approach helps organizations minimize their exposure to known threats and maintain the overall security and stability of their SAP landscape.
Together, these actions form a proactive and resilient SAP security strategy. The emergence of CVE-2025-31324 is not just a technical footnote; it is a wake-up call for cyberprofessionals across all domains.
Conclusion
SAP plays a vital role in supporting the operations of a wide range of organizations across various industries and sizes. Its comprehensive solutions enable the integration of key business processes, from finance to supply chain management, making it a critical component of many enterprises. However, this centrality also makes SAP systems attractive targets for cyberthreats, which can disrupt operations and compromise sensitive data. Recent vulnerabilities, such as CVE-2025-31324, highlight the ongoing security challenges facing SAP environments. To mitigate risk, organizations must adopt a multilayered security approach that goes beyond perimeter defenses, including strong access controls, continuous monitoring, and timely patch management. Embedding security practices throughout SAP project lifecycles and educating users further strengthens overall protection.
Looking ahead, the shift toward SAP S/4HANA, cloud adoption, and increased digital connectivity will demand even greater focus on security. Enterprises must treat SAP security as a continuous priority, not a one-time effort, ensuring it evolves alongside enterprise and technology changes. Protecting SAP effectively means safeguarding the core of an organization’s digital future.
Endnotes
1 SAP, “SAP: A 50-Year History of Success”
2 SAP, “SAP Company Information”
3 SAP, “Nestlé: Digitalizing Expense Management From Claim Submission to Approval and Reimbursement in a New Age of Business Travel”
4 SAP, Pfizer, “Pfizer: Transforming Internal Controls with Governance, Risk, and Compliance Solutions”
5 Kofalt, J.; “How to Think Long Term About SAP ECC Customizations,” TechTarget, 23 March 2022
6 National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD), “CVE-2025-31324 Detail,” USA
7 NIST, Special Publication 800-207, Zero Trust Architecture, August 2020
8 SAP, “SAP Security Patch Day - September 2025”
Nipun Mahajan
Is actively involved in the cybersecurity community as a co-chair, presenter, and mentor, contributing to various conferences and educational initiatives. Mahajan specializes in cross-platform application security with extensive experience in SAP, business intelligence, governance risk and compliance (GRC), and segregation of duties (SoD) analysis. Mahajan is the executive vice president of the ISACA® Denver Chapter.
