

As cyberthreats emerge more frequently and in various capacities, it has become essential for organizations to employ the best security measures possible. To this end, multifactor authentication (MFA) is vital to today's security protection and serves as a significant step beyond traditional, static password protection. MFA allows users to provide several identification factors before sensitive data is released, which minimizes the chances of unauthorized individuals accessing sensitive information.1 MFA has the potential to revolutionize cyberdefense in the 21st century. There is value to be gained from delving into its benefits, limitations, and the possibilities it offers when integrated with emerging technologies.
The Rise of Cyberthreats
The technological environment has evolved dramatically in the last 2 decades, mainly due to the advancement of the internet and Web 2.0 technology.2 These technologies have created new forms of connection globally, but have also broadened the landscape of cybercrimes.3 The COVID-19 pandemic played a significant role in enhancing the use of these evolving technologies as organizations and people transferred to remote work and digital environments, which has inevitably led to new loopholes for hackers to exploit.4 Advanced technology has given way to new connections across the globe, where there are more opportunities for hackers to gain access to sensitive data, thus creating a rise in cybercrimes. In response to the growing threat, many organizations have adopted secondary protection mechanisms, such as MFA, to provide more security. This shift not only bolsters security but also boosts user confidence, as users are becoming more aware of cyberattack threats and are increasingly open to using MFA as an added security layer.
According to recent statistics by the US Federal Bureau of Investigation (FBI), cyberattacks on organizations have increased by more than 400% since the COVID-19 outbreak.5 This rising trend surpasses previous rates of cyberthreats, highlighting the rapid advancement and increasing frequency of attacks such as phishing, ransomware, and credential stuffing. Phishing attacks, which aim to mislead and convince users to disclose confidential information through informative email or other related web resources, have advanced a great deal. Perpetrators often use social engineering techniques to manipulate their target completely.6 Similarly, ransomware attacks—where cybercriminals encrypt a victim's data and then demand payment for the decryption—have intensified, affecting organizations across all industries and scales.7
Organizational losses, both financial and reputational, resulting from data breaches are becoming increasingly more commonplace and are intensifying in severity. According to an IBM report, the average cost of a data breach was estimated to be US$4.2 million in 2021.8 In 2024, the average cost of a data breach now stands at US$4.88 million, the highest it has ever been.9 Studies indicate that the latest generation of cybercriminals is achieving unprecedented profits from cybercrime, with damages estimated to reach US$10.5 trillion annually by 2025, a figure that is 75% higher than the current estimates of about US$6 trillion.10 These figures represent not only the direct monetary costs of breaches and subsequent loss but also anticipated additional expenses over time, including regulatory penalties, legal services, and the erosion of organizational reputation. It is a fact that data breaches lead to a loss in customer trust and business. This fact alone should compel many organizations to reconsider their cybersecurity strategy.
As internet usage rises every day,11 so too does the pressure to enforce the appropriate level of security. In recent years, MFA has emerged as one of the key components of robust security, as it helps prevent unauthorized access to a user's account.12 MFA is reliable because several factors are involved when authenticating a user, and thus, fewer breaches occur due to compromised passwords.13 It is for this reason that it is essential to recommend MFA as a preventative measure and an essential practice for organizations eager to minimize threats to sensitive data.
MFA as a Game-Changer
MFA complements standard security paradigms by adding several barriers. While single factor authentication, as the name suggests, only requires a password, MFA requires that the user provide at least 2 factors.
These factors can depend on something the user knows, such as a password; something the user has, such as a mobile device or security token; and something that the user is, i.e., biometrics such as fingerprints or facial identification, as illustrated in figure 1. This multi-layer solution offers excellent protection against most threats that target passwords.14
Figure 1—How MFA Works
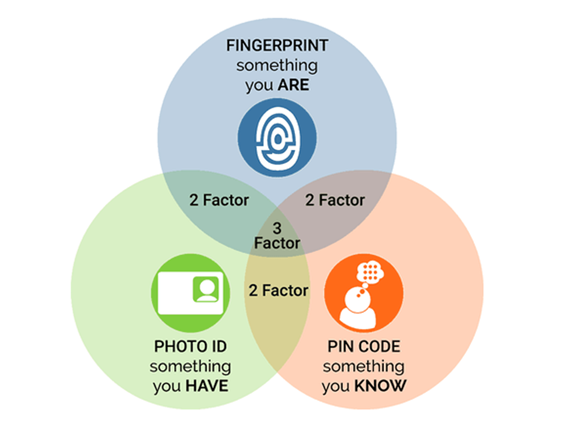
Source: St. Mary's University, “Multi-Factor Authentication (MFA),“ https://stmuservicedesk.stmarytx.edu/TDClient/74/Portal/KB/ArticleDet?ID=4195
Another strength of MFA is its effectiveness in mitigating the risk associated with phishing attacks. For example, in a potential phishing scenario, even if an attacker manages to spoof or guess a password, they will still need to provide the second authentication factor before being granted access to the account. This additional requirement diminishes the opportunities for penetration because it poses an extra barrier to access for attackers.
MFA has proven its ability to protect an organization from cyberthreats, leading to improved security. For instance, Microsoft reported that the use of MFA brought down account hacks by up to 99.9%, a significant enhancement in the safety of user data.15 Microsoft stands as an example of how MFA fortifies security and strengthens the trust between the organization and its users. Case studies and deployments have demonstrated that MFA implementation leads to decreased security threats. As an example, organizations implementing MFA have reported that their account compromise rate has been reduced to 0.1%.16 However, though MFA substantially improves security, it is not a panacea for all security issues. Some challenges must be conquered for MFA to serve its purpose to the maximum and offer robust protection from cyberthreats.
Challenges and Limitations of MFA
The main challenge with MFA is that some of its components can be compromised, notably SMS-based authentication. Research has shown that even though SMS is one of the most popular methods of delivering one-time codes, it is still vulnerable to attacks.17 Mobile phishing poses a significant threat because criminals can penetrate mobile networks to intercept SMS messages and, therefore, log into user accounts despite not being able to provide the user’s password. This weakness defeats the purpose of implementing MFA since attackers can bypass the second authentication factor without much resistance. Moreover, social engineering attacks are also a significant concern as they may lead users to provide their second factor, such as an SMS code or accept a push notification to authenticate a device.18 These tactics could easily undermine MFA.
2 additional challenges are user adoption and accessibility. These factors significantly impact the potential for MFA to become more prevalent. Many users consider MFA a nuisance or needlessly complex and resist its implementation.19 This aversion can occur due to the extra measures needed for validation, which could interfere with perceived efficiency. Therefore, proper implementation of MFA will require a balance between security and usability so that more users can adopt the technology.
When it comes to data security, organizations must strive to educate their employees on MFA so that they can embrace the tool as a means of guarding sensitive information. Proper implementation of MFA is essential, as security measures must seamlessly integrate with employees’ workflows.
Organizations should combine MFA with other related technologies and measures to bolster MFA security capabilities and effectiveness. For example, an extra layer of authentication, such as biometrics (fingerprint or face recognition), can be added to a system, rendering it almost impossible for a malicious actor to access sensitive data. Furthermore, additional measures, such as behavioral analytics, can make security even more effective, as users' actions can be tracked to easily identify suspicious activities. The integration of these solutions with MFA ensures that organizations have a layered security approach that minimizes data breach risk.
The Future of Cyberdefense
Cyberthreats are constantly evolving and becoming more sophisticated. Thus, countermeasures applied in cybersecurity must also be progressive and elaborate. With the ability to add layers of security on various interfaces and integrate advanced technologies, MFA is a key element of future cyberdefense strategies.
MFA’s integration with other advanced technologies and its application in today’s world positions it as a cutting-edge field of innovation with the potential to shape the future of security. For instance, artificial intelligence (AI) has recently emerged as one of the most significant upgrades to MFA systems, as it is a critical technology of the future. Pattern anomaly analysis is one of many ways through which AI can scan users' behavior and identify any irregularity that will signify illegitimate activity. For instance, if the user typically logs in from a particular region and then suddenly tries to log in from another country, the AI system will automatically request more security when approving the account access. AI has the potential to strengthen MFA from a security perspective and reduce the potential for malicious illegitimate attacks, making MFA more effective and adaptive than other security solutions.
One of the most promising advancements in MFA technology is blockchain in node authentication. There are multiple blockchain applications in ID verification because of blockchain’s decentralized and secure properties, which may be incorporated into MFA systems to make them even more secure.20 Blockchain facilitates a more believable authentication system that is less susceptible to influence or scams. Its decentralized nature benefits security and helps people reclaim their identity and data.
Blockchain has been reported to offer enhanced security compared to other data storage technologies due to its autonomous architecture that does not allow a person or group of persons to control the data or have the sole right to alter it.21 Blockchain ensures that the authentication data is not stored in one place but is replicated across a network as nodes; therefore, the potential hacker will have to corrupt all nodes to alter information. This creates a natural synergy with MFA, as blockchain technology can securely store MFA credentials and authentication events. Blockchain addresses some of the risk associated with MFA, such as storing credentials in a central location and the existence of a single point of failure. Furthermore, blockchain's smart contracts can execute MFA policies and record the authentication procedures transparently.
Last, biometric authentication is another field that has matured enough to provide users and organizations with a practical, more reliable solution than standard identification tools. This technology includes devices such as facial identification systems and fingerprint scans, which provide unique attributes that are hard to imitate or forge. The use of biometrics in MFA systems can enhance an organization's security while simplifying the user experience, as most biometric methods demand less effort than entering passwords or codes.
The future of MFA technologies that integrate advanced technologies holds immense potential. However, as with any emerging technology, regulations must be established to prevent attempts to obtain sensitive data.
The Regulatory Landscape
There are increasing demands for regulatory oversight regarding the use of authentication methods such as MFA. Legislation such as the EU General Data Protection Regulation (GDPR) requires enhanced authentication to safeguard data and enhance information security worldwide.22 As different trends in regulations governing organizations change, MFA will likely be implemented universally, making it an essential component in an organization's security management plan.
According to the latest legal trends, MFA is anticipated to be implemented across organizations of various industries; therefore, MFA is a critical element to consider in the security management of organizations. For instance, the US has established a 2FA requirement for accessing federal information systems.23 Also, in the US, the New York Department of Financial Services (NYDFS) has mandated MFA for financial institutions and related entities.24 Additionally, The Payment Card Industry Data Security Standard (PCI DSS) 4.0 will require MFA for all access to payment transactional data in 2025.25
Likewise, the Federal Trade Commission’s (FTC) Standards for Safeguarding Customer Information (or Safeguards Rule) specifies that organizations must utilize MFA for the user profiles that give the customer data access, and violators face stiff penalties.26 Due to these regulatory requirements, the global MFA market is set to double in the period leading up to 2027.27 It is apparent that such a regulatory environment boosts the application of MFA in organizations and increases the security of measures in their activities.
Conclusion
MFA has the potential to revolutionize the way organizations tackle cyberdefense in the 21st century. This is particularly essential given the evolving nature of cybertactics. MFA provides an added layer of security that can significantly minimize the attack surface. However, organizational leaders must remember that MFA is not static, and more research and technology development is possible and necessary.
The advancement of new technologies that integrate MFA will continue to shape the future of cybersecurity. In the years to come, organizations will inevitably face challenges when it comes to protecting data. However, MFA will become a crucial component of organizational protection measures to prevent critical data leaks and maintain confidence in the era of global connections.
Endnotes
1 Yasar, K.; Shacklett, M.E.; “Multifactor Authentication”
2 Yamin, M.; “Information Technologies of 21st Century and Their Impact on the Society,” International Journal of Information Technology, iss. 11, 2019, p. 759-766
3 Utica University, “Ten Ways Evolving Technology Affects Cybersecurity,” 30 April 2020
4 Alashhab, Z.R.; Anbar, M.; et al.; “Impact of Coronavirus Pandemic Crisis on Technologies and Cloud Computing Applications,” Journal of Electronic Science and Technology, vol. 19, iss.1, 2021
5 Smith, R.; “FBI Sees a 400% Increase in Reports of Cyberattacks Since the Start of the Pandemic,” Insurance Business, 27 August 2020
6 Al‐Qahtani, A. F.; Cresci, S.; “The COVID‐19 Scamdemic: A Survey of Phishing Attacks and Their Countermeasures During COVID‐19,” IET Information Security, iss. 14, vol. 4, 2022, p. 324-345
7 Connolly, A. Y.; Borrion, H.; “Reducing Ransomware Crime: Analysis of Victims’ Payment Decisions,” Computers & Security, vol.119, 2022
8 IBM, “IBM Report: Cost of a Data Breach Hits Record High During Pandemic,” 28 July 2021
9 Sobers, R.; “157 Cybersecurity Statistics and Trends [updated 2024],” Varonis, 13 September 2024
10 PurpleSec, “2024 Cybersecurity Statistics: The Ultimate List of Stats, Data & Trends”
11 Petrosyan, A.; “Internet Usage Worldwide – Statistics & Facts,” Statista, 13 January 2025
12 Mostafa, A. M.; Ezz, M.; et al.; “Strengthening Cloud Security: An Innovative Multi-Factor Multi-Layer Authentication Framework for Cloud User Authentication,” Applied Sciences, vol. 13, iss. 19, 2023
13 Nanda, A.; Jeong, J. J.; et al.; “Examining Usable Security Features and User Perceptions of Physical Authentication Devices, Computers & Security, vol. 139, 2024
14 St. Mary's University, “Multi-Factor Authentication (MFA)“
15 Alder, S.; “Multi-Factor Authentication Blocks 99.9% of Automated Cyberattacks,” The HIPAA Journal, 13 September 2019
16 Doffman, Z.; “FBI Issues Surprise New Cyber-Attack Warning: Multi-Factor Authentication is Being Defeated,” Forbes, 7 October 2019
17 Taylor, C.; “Top Five (5) Risks From SMS-Based Multifactor Authentication,” CyberHoot, 4 April 2024
18 Impact of Social Engineering Attacks: A Literature Review, Developments and Advances in Defense and Security, Smart Innovation, Systems and Technologies, vol. 255, 2022
19 Aslam, M.; “The Impact of Multi-Factor Authentication (MFA) on Strengthening Cybersecurity in e-commerce Applications,” 2020
20 Ou, H.H.; Pan, C.H.; et al.; “Decentralized Identity Authentication Mechanism: Integrating FIDO and Blockchain for Enhanced Security,” Applied Sciences, vol. 14, iss. 9, 2024
21 Habib, G.; Sharma, S.; et al.; “Blockchain Technology: Benefits, Challenges, Applications, and Integration of Blockchain Technology With Cloud Computing,” Future Internet, vol. 14, iss. 11, 2022, p. 341
22 Li, H.; Yu, L.; et al.; “The Impact of GDPR on Global Technology Development,” Journal of Global Information Technology Management, vol. 22, iss. 1, 2019, p. 1-6
23 Amigorena, F.; “What You Should Do When Two-Factor Authentication Becomes a Security Requirement,” Info Security Magazine, 28 July 2022
24 New York State Department of Financial Services, “Re: Guidance on Multi-Factor Authentication”, 7 December 2021
25 BARR Advisory, “PCI DSS Future-Dated Controls: 7 Critical Changes that Will Shape Your Security Strategy,” 7 February 2025
26 Dempsey, J.; “The FTC’s Rapidly Evolving Standards for MFA,” IAPP, 8 November 2022
27 Business Wire, “Global Multi-Factor Authentication Market Report 2022-2027: Growing Instances of Data Breaches, Rising Adoption of BYOD Policies, and Stringent Regulations to Drive Growth - ResearchAndMarkets.com“ 11 August 2022
Alex Mathew, Ph.D., CISA, CISSP, CCNP, CEH, CEI, CHFI, ECSA, MCSA
Is an associate professor in the Department of Cybersecurity at Bethany College (West Virginia, USA) and is widely recognized for his deep expertise in cybersecurity, cybercrime investigations, next-generation networks, data science, and IoT Azure solutions. His proficiency in security best practices, particularly in IoT, cloud systems, and healthcare IoT, is complemented by his comprehensive knowledge of industry standards such as ISO 17799, ISO 31000, ISO/IEC 27001/2, and HIPAA regulations.
As a certified Information systems security professional (CISSP), Mathew’s leadership is evident in his role as a consultant across international regions, including India, Asia, Cyprus, and the Middle East. His extensive two-decade career, distinguished by numerous certifications and over 100 scholarly publications, underscores his commitment to advancing the field. Mathew has been a pivotal force in organizing cybersecurity conferences and establishing incubation centers, contributing significantly to the academic and professional community.
A highly sought-after speaker, Mathew’s influence extends to international conferences where he shares his insights on cybersecurity, technology, and data science. His remarkable interpersonal skills and openness enhanced his ability to engage and inspire diverse audiences, further cementing his position as a leader in his field.
