

Despite unprecedented advances in technology, phishing remains one of the most persistent cybersecurity threats organizations face.1 Phishing refers to deceptive emails, messages, calls, or other forms of correspondence that are purposely crafted to trick individuals into revealing sensitive information, downloading malicious files, or performing unauthorized actions that compromise security. Organizations, in turn, have sought to address this risk through security awareness training and phishing simulation exercises. These simulations send fake phishing emails to employees to evaluate whether they can spot and accurately report real phishing threats when they occur.
At face value, the logic of phishing simulations is sound—by exposing employees to simulated attacks, enterprises gain insight into the vulnerabilities that exist within its workforce and can deploy targeted training to those individuals or departments to better improve security culture. However, many organizations continue to rely on outdated approaches that do not reflect the evolving sophistication of real-world attacks, introducing a dangerously misleading sense of security rather than genuine preparedness. Recent data demonstrates that phishing tactics have grown increasingly advanced, highlighting that static or outdated templates fail to mirror the current attack landscape.2 To effectively combat tomorrow's threats, phishing tests must evolve beyond traditional methods and adopt a more proactive approach.
Crafting Realistic Simulations
One of the major flaws of many phishing simulations is the continuous use of rudimentary and unrealistic templates. It is common for organizations to deploy test emails that resemble the phishing attempts of a decade ago: full of grammatical errors and clumsy formatting. Employees, unsurprisingly, usually pass these tests with ease, and management subsequently records a low click rate as evidence of a security-aware workforce. Such outcomes, however, are deceptive.
The challenge lies in the fact that email is no longer the sole medium of phishing attacks. Modern day attackers exploit multiple digital avenues, from SMS to social media platforms. For example, an email offering a limited time discount on Amazon Prime, a notification about a shipment from AliExpress, or a routine invoice sent from what appears to be a known contractor is far more representative of current phishing strategies than the implausible “lottery winner” emails of the past, as demonstrated in figure 1.3
Figure 1—Outdated Phishing Email Example
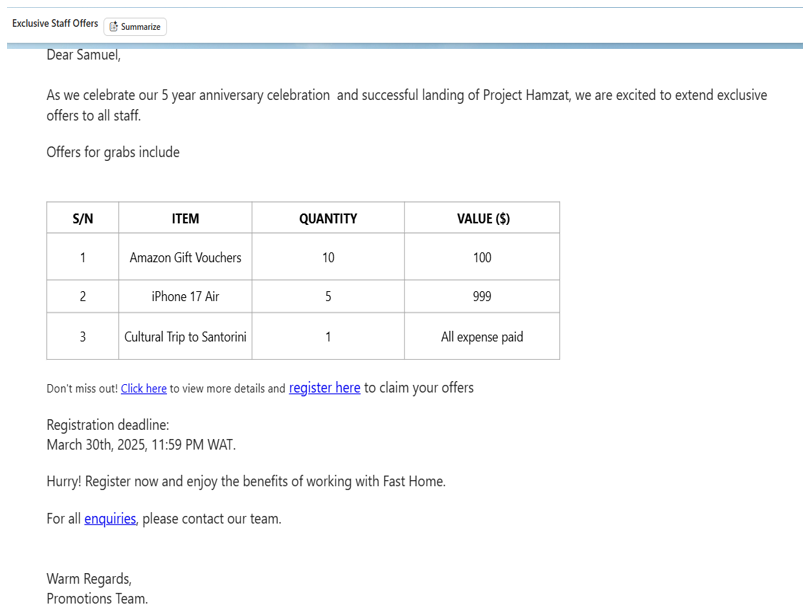
The truth is that genuine attackers rarely use such poorly executed scams in today’s dynamic environment. Instead, cybercriminals seek to exploit familiarity and trust by deploying meticulously crafted and highly convincing messages, as seen in figure 2. When simulations fail to mirror these sophisticated social engineering tactics, employees are ill-prepared to recognize authentic threats. In effect, organizations are training their staff not to detect phishing, but merely to pass low-bar tests.
Figure 2—Modern Phishing Email

Source: Wizer, “Top 5 Must-Know Phishing Simulation Templates - May 2024,” 13 May 2024
Today’s more sophisticated phishing techniques often involve a variety of platforms. One such platform, WhatsApp, has emerged as a critical channel not only for personal communication but also for internal organizational exchanges and professional correspondence. With over 3.14 billion active users and 150 billion messages exchanged daily in 2024, the platform has become indispensable for real-time team coordination, updates, and client engagement.4 This shift in communication has created a new and rapidly expanding attack surface.
There are documented cases of enterprise WhatsApp accounts being compromised, with attackers impersonating executives to redirect payments, extract sensitive data, or spread misinformation.5 The informal and rapid nature of instant messaging fosters a sense of familiarity and ease which is harder to replicate in emails. Thus, the use of phishing simulations tailored exclusively to email no longer addresses the practical landscape of cyberthreats..
A particularly insidious example unfolded in 2024, when over 100 organizations across Europe and the United States were attacked by the StrelaStealer phishing campaign.6 Attackers distributed emails that contained malicious ZIP files with embedded JavaScript that, when executed, installed malware to steal email credentials posing severe threats to enterprise data integrity and operational security. The main objective was to harvest email login credentials and then use those credentials in follow-up attacks..
If the purpose of phishing tests is to prepare employees for risk that they will actually encounter, then these programs must extend beyond traditional email-based scenarios to include WhatsApp, SMS, and other commonly used messaging platforms. Organizations that fail to include these aspects are increasingly vulnerable to the kinds of attacks that are most prevalent in everyday enterprise environments.
Genuine attackers rarely use such poorly executed scams in today’s dynamic environment. Instead, cybercriminals seek to exploit familiarity and trust by deploying highly convincing messages.The Future of Phishing Tests
To resolve these issues, organizations must think differently about the design and implementation of phishing simulations. There are 3 considerations that are pertinent for organizations:
- Phishing tests must be based on real-world scenarios. This can be achieved by building a library of templates that closely recreate the strategies of contemporary cybercriminals. This library should be maintained by the organization’s security awareness or threat intelligence team, who must ensure it remains current by tracking emerging phishing techniques. These templates should employ believable scenarios relevant to local and industry-specific contexts. This can include shipping notifications for logistics enterprises, financial settlement requests for banks, or vendor negotiation updates for procurement officers.
- Phishing tests should be adaptive and ongoing rather than uniform, one-off events. Many organizations implement simulations by delivering a single email blast to all employees simultaneously, as if an attacker would attempt to deceive an entire workforce on the same day. Real-world adversaries, however, employ staggered tactics, probing different entry points at different times. Simulations should therefore mirror this gradual, targeted approach: teams should receive tailored phishing attempts across varying timelines to measure organizational resilience more accurately in real-world conditions.
- The objective of phishing exercises should not solely be punitive. Too often, employees who fail phishing tests are shamed or disciplined, creating a blame culture that discourages openness about mistakes. A more constructive approach emphasizes education: If an employee falls for a simulated phishing attempt, the test should become a direct learning opportunity, guiding individuals on how to spot subtle red flags and encouraging a culture of proactive reporting. When organizations adopt this approach, employees become more engaged and confident in identifying real threats. Over time this builds a stronger security culture, one rooted in learning, accountability, and shared responsibility for protecting the organization.
When organizations take these considerations seriously, phishing simulations shift from being a compliance checkbox to a practical tool for risk reduction. By grounding tests in real-world scenarios, running them continuously and adaptively, and treating every failure as a chance to learn rather than punish, organizations will begin to see measurable improvements to security posture. These improvements include fewer risky clicks from employees, increased reporting of suspicious messages, and stronger engagement from employees across business functions. Over time, this approach creates a workplace where vigilance becomes second nature, minimizing breach risk and empowering teams to safeguard assets against an ever-advancing threat landscape.
Conclusion
The future of phishing simulations lies in creating practical, adaptive, and contextual tests. Outdated email-only exercises using unconvincing templates are no longer adequate, they merely teach employees to pass low bar security checks. True resilience requires employees to be exposed to realistic, multichannel simulations that incorporate modern phishing tactics across email, WhatsApp, SMS, and other platforms attackers actively use. Moreover, the design must mirror adversarial behavior: gradual rollouts, contextual templates, and immediate, constructive feedback for employees who fall victim. The organization that fails to evolve its testing methods is not building a secure defense strategy—it is simply operating with a false sense of security. When simulations reflect real-world adversarial behavior, security efforts can move from compliance to true risk reduction, transforming the workforce from a vulnerability into an organization's strongest line of defense.
Endnotes
1 Fortinet, “Cyber Awareness Month: Phishing and Software Updates Still Matter Most,” 1 October 2025
2 Cofense, 2024 Annual State of Email Security, UK, 2024
3 United States Federal Trade Commission (FTC), “Three Signs of a Prize Scam”
4 Jaimes, R.; “WhatsApp Statistics And Users Trends 2025,” Quantumrun Foresight, 12 November 2025
5 Bonaobra, J.F.; Policarpio, M.; et al.; “Self-Propagating Malware Spreading Via WhatsApp, Targets Brazilian Users,” Trend Micro, 3 October 2025
6 Cox, K.; “The 5 Biggest Phishing Attacks of 2024,” Memcyco, 21 January 2025
Phil Odai-Ayiku
Is an information security analyst who leverages his background in mechanical engineering to approach cybersecurity challenges with precision and structured thinking. He has extensive experience in SOC operations and security governance across multiple industries, with a commitment to fortifying both human and technical safeguards.
