Within the cybersecurity space, quantum computing has often been linked to doomsday scenarios such as the cracking of RSA.
But quantum computing already goes beyond that. Large firms such as IBM have already done research into how quantum computing, exploring multiple generations of quantum computers. Later generations of quantum computers may eventually be used for general applications in the 2030s.
While it is important to consider quantum computing risks, ISACA’s global Quantum Computing Pulse Poll found that 37% of firms have not discussed the topic of quantum computing at all and only 5% consider it a high-priority area for near-term planning.
Quantum computing is not just a cybersecurity issue. Due to its potential business enablement, more firms need to look at how quantum computing could potentially transform their business as part of an overall technological transformation roadmap. Forbes recently highlighted how quantum computing can help potentially solve complex problems such as supply chain and logistic operations.
Fighting Human Nature
The main difficulty behind quantum computing threats in the cybersecurity space revolves around classic risk mismanagement. To recap how risk is being perceived, we recall a cartoon.

Research has shown that human behavior tends to be uncertain, and often misjudge the appropriate response when dealing with low-probability, high-impact events, which is the current state of quantum computing threats. But risk is also not a static concept. As quantum computing continues to develop, the assumption of “low probability/likelihood” begins to be challenged much more. For the case of quantum computing risks, the likelihood profile over time might be more accurately plotted as such:
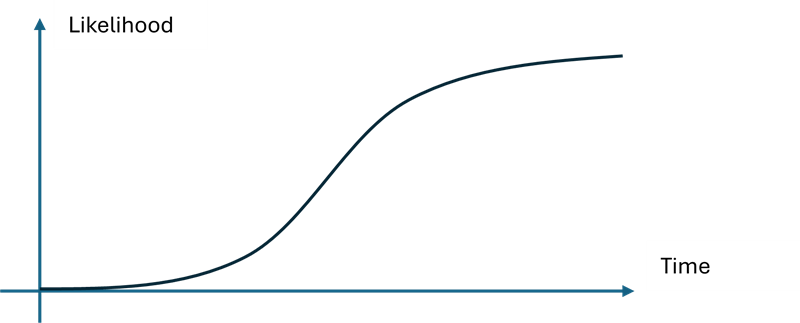
This graph is well-known in many fields, such as autocatalysis in chemistry, or the S-curve in business. One reason such an S-curve is appropriate is due to the sharp transition between low-likelihood risk pictures (when no one has openly managed to publish a breakthrough on the RSA algorithm) and high-likelihood risk pictures (once breakthroughs are published, and threat actors such as nation-states begin to copy, at scale, the quantum computer setup to perform mass-scale attacks).
Such graphs are difficult for risk analysts because given uncertainty around the key question: when does the inflection point occur?
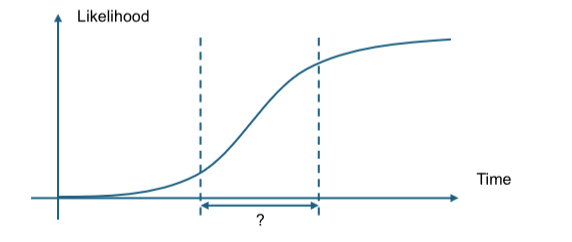
These risks present two major problems for enterprise risk management. First, the likelihood of a risk is so low at the initial stage that firms often overlook them. This can be the case even with NIST prioritizing the search for post-quantum cryptography algorithms due to known risks such as “harvest now, decrypt later.”
But the inflection period could be short, a matter of months, should a breakthrough occur. This will likely outspeed reactive cybersecurity measures; transitioning to new cryptographic standards for brownfield projects often involves large overhauls of infrastructure. The procurement process alone for such types of projects can easily take a year, not even considering the implementation challenges of such a large overhaul, without the necessary bandwidth to perform industry-appropriate tests to ensure that the business continues to operate with the appropriate supported post-quantum cryptographic algorithm.
More Developments in the PQC Space
NIST recently announced new PQC algorithms, which helps to build resiliency against attacks that could arise due to weaknesses in the existing candidates for post-quantum cryptography. But this also influences how vendors must adapt to the quickly-changing lens in which cryptography is viewed due to the advent of quantum computers; no longer can an enterprise expect to assume that a standard set of cryptographic algorithms could last for the lifetime of the system from cradle to grave. Now systems must be crypto-agile.
As recently as 9 April 2025, open-source libraries such as OpenSSL have incorporated PQC support as well. It is no longer a matter of “if,” but “when” PQC arrives.
Education and User Awareness
While quantum computers have started to regularly make the headlines, it is clear that enterprises have not grasped the significance of quantum advances, as 55% of respondents to the ISACA poll have not taken steps to prepare for quantum computing, even if 46% of them think quantum computing would likely lead to revolutionary innovations.
Perhaps one difficulty in the discussion today is the translation of technological concepts to risk-based discussions, which is also what I seek to do in my own work as a cybersecurity practitioner. From the S-curve illustration shown, risk-based concepts are not entirely within the remit of cybersecurity. However, similar concepts from different disciplines can be used to understand time-based cybersecurity risk. What we have to do is to find the right language and right tonality to communicate what quantum computing is, its implications to cryptography, and the necessary mindset changes.
I am Convinced, But I Don’t Know My Risks
Often, a risk assessment involves an exercise of asset identification. From a cybersecurity lens, one of the most useful ways to assess such risk is to begin with a thought experiment that aims to answer these four questions:
- What are we working on?
- What can go wrong?
- What are we going to do about it?
- Did we do a good enough job?
Perhaps we don’t know the eventual end-state of PQC. NIST could continue to evaluate more algorithms and recommend more of them for the industry. But what is definitely within the control of an organization is to understand their assets, which is the crux of Question 1. That then sets the stage for a threat modelling exercise, of which I have previously written how threat models can be performed for critical infrastructure. These will facilitate a strategic discussion on transitioning the enterprise away from potentially vulnerable algorithms, such as RSA, toward a more crypto-resilient approach.
A Change in How We View Technology
Broadly, quantum computing advances will change how we view technology significantly. This is consistent with the maxim on how cybersecurity evolves in tandem with technological innovation. And because cybersecurity is transversal (almost every discipline with a digital footprint has to consider cybersecurity as some point), it is vital that cybersecurity practitioners like us pick up relevant risk models to educate our stakeholders and protect them from risks that they may only have a vague idea of, but not grasp its full significance.
