



The digital era presents both unprecedented opportunities and formidable challenges. As organizations and governments strive to leverage its potential, they face an escalating array of cyber threats that jeopardize security and operational stability. With digital transformation accelerating, the sophistication and scale of these risks necessitate robust, cost-effective strategies. This analysis examines the evolving cyber-threat landscape—its drivers, consequences, and underlying causes—before proposing a pragmatic, data-driven cybersecurity approach that delivers measurable returns on investment.
The Dual Nature of the Digital Revolution
Digital transformation has fundamentally reshaped societal operations. Consumers now manage finances online, businesses conduct virtual meetings via cloud platforms and governments digitize public services at an unprecedented pace. McKinsey estimates that 90% of organizations are actively undergoing this shift, while the World Bank’s 2023 Digital Progress Report highlights a post-pandemic surge in digital infrastructure adoption. The benefits—enhanced efficiency and expanded reach—are clear. Yet, this transformation has exposed new vulnerabilities, which agile cyber adversaries exploit through tactics that outstrip conventional defenses.
The Threat Landscape
Today’s cyber risks are diverse, persistent and increasingly sophisticated. The following overview, informed by multiple studies, highlights the most critical threats (note: figures are indicative due to varying methodologies):
- DDoS Attacks: The 2016 Mirai botnet, which commandeered IoT devices to disrupt vast internet segments, remains a benchmark. Distributed denial-of-service attacks accounted for over 50% of incidents in 2024, according to one analysis.
- Phishing: In August 2024, the Storm-2372 group deployed “device code phishing” to steal authentication tokens, targeting governments and NGOs globally. In Hong Kong, phishing incidents surged 108% year-over-year, comprising 62% of reported cases in 2024.
- Eavesdropping: State-sponsored surveillance, such as the PRISM program (revealed in 2013) or the 2023 rerouting of Google and Amazon traffic to Russian servers, remains a significant concern. “Harvest now, decrypt later” strategies, anticipating quantum computing advances, heighten the stakes.
- Account Takeovers (ATO): A 2024 cloud provider breach exposed billions of records from companies like AT&T and Santander due to weak credentials. One report estimated identity theft losses has reached $635 billion in 2023.
- Ransomware: The 2021 Colonial Pipeline attack, yielding hackers $4.4 million in Bitcoin, exemplifies this threat. A 2024 study reported 59% of organizations were hit, with ransom demands quintupling within a year.
- API Attacks: T-Mobile’s 2023 breach, exposing data on 37 million customers via a vulnerable API, underscores this growing vector. APIs now account for 71% of web traffic, per one estimate.
- Software Supply-Chain & Malware Strikes: The 2020 SolarWinds attack affected 18,000 entities; the 2025 Bybit breach cost US$1.5 billion. Gartner forecasts that 45% of firms will face such incidents by year-end, tripling 2021’s rate.
- Human Error: Missteps drive 34% of cloud breaches, with insider incidents averaging $4.99 million in damages.
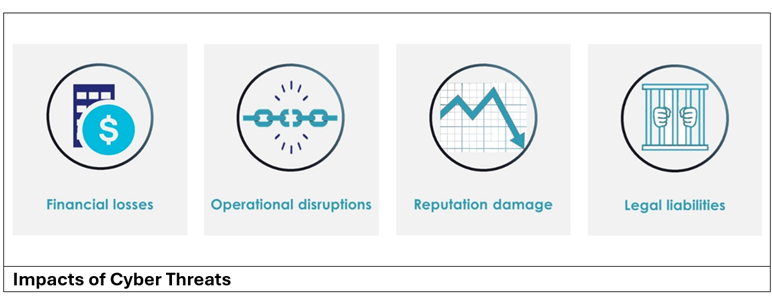
The Consequences
Cybersecurity has become a boardroom priority. The financial toll is staggering: global cybercrime costs reached US$8 trillion in 2023 and are projected to hit $10.5 trillion this year. A typical breach costs $4.88 million. Beyond finances, operations suffer—evident in the Colonial Pipeline’s fuel disruptions or the Optus 2022 data leak. Reputations erode, with 21% of consumers abandoning compromised brands and stock values dropping 7.5% on average. Legal risks also escalate: GDPR fines totaled €4.5 billion by May 2024, while in jurisdictions like Australia, negligent directors face personal liability.
Roots of Vulnerability
Several factors fuel this crisis:
- Visibility Gaps: Many organizations lack a comprehensive view of their data—its access points, locations, and usage—leaving blind spots.
- Complexity: Cloud proliferation and vendor dependencies create silos and fatigue, compounded by geopolitical disputes over digital sovereignty.
- Supply-Chain Weaknesses: Human error and outdated systems persist despite patches, while poor vendor security and unauthenticated code undermine resilience.
- Credential Frailty: Weak passwords and phishing susceptibility drive account breaches.
- Web Exposures: Unsecured APIs and applications invite automated attacks, with bots responsible for 27% of API incidents.
- Data Risks: Inadequate encryption and lax controls leave data vulnerable in transit and at rest.
- Recovery Delays: Slow restoration prolongs damage post-attack.
- Resource Constraints: Underinvestment in tools and training widens gaps.
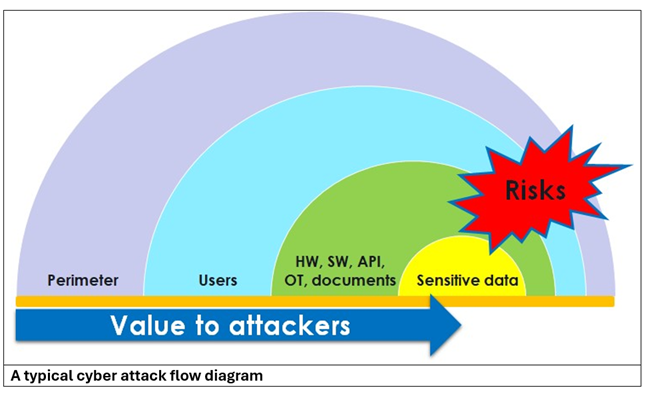
The Attack Lifecycle
Most cyber assaults follow a recognizable pattern. External actors—or occasionally insiders—breach perimeters via phishing or exploits, often using DDoS as a diversion. They escalate privileges by stealing credentials from authorized users, then reconnoiter to locate critical assets—hardware, software or data. The objective is typically financial gain through stolen information or ransom, though state-sponsored attacks may pursue sabotage. Disrupting this sequence is essential to mitigation.
User-Level Safeguards
Individuals form the first line of defense, with identity as the new perimeter. Core practices include online vigilance, avoiding suspicious links, monitoring device anomalies and adopting password-less solutions like FIDO2. Regular backups are indispensable.
Organizational Strategy
Organizations require more than basic measures—they need a cohesive strategy. Frameworks like NIST or Hong Kong’s Digital Policy Office guidelines provide a foundation, with success hinging on execution. Three principles stand out:
- Governance as Priority: A robust Digital Trust Framework—integrating people, processes, technology, and organization —ensures accountability and adaptability. The CIA triad (confidentiality, integrity, availability) must underpin risk management across identities, networks, applications, devices and data.
- Beyond Compliance: View compliance as a component of risk management, not a standalone task, aligning it with business objectives rather than regulatory mandates alone.
- Strategic Implementation:
- Human-Centric Design: Deploy intuitive, low-friction systems to reduce user errors.
- Embedded Security: Integrate privacy and zero-trust principles (never trust, always verify) from inception, reinforced by multi-factor authentication, code signing, and vendor scrutiny.
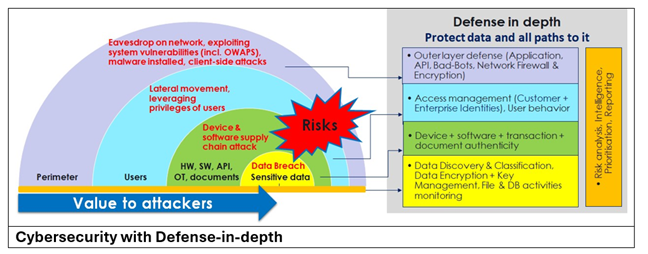
- Unified Platform: Consolidate defenses—spanning identity management, application/API security, data protection, risk analytics, intelligence, and prioritization—to eliminate silos and detect threats proactively.
- Resilience: Adopt a 3-2-1 backup strategy (three copies, two media types, one offsite) and rehearse recovery protocols to minimize downtime.
- Talent Development: Continuously train staff and certify cybersecurity professionals.
The Cost-Benefit Analysis
Cybersecurity investments are substantial but far less costly than breaches. Prioritize spending based on risk reduction and returns: lower exposure, operational efficiencies (e.g., reduced server reliance, less manual effort), and unlocked opportunities. When benefits exceed costs, the case for investment is clear, supported by extensive research.
A Unified Defense
Envision a platform that protects identities, networks, applications, devices, and data with layered resilience. Real-time monitoring and rapid response neutralize external attacks and insider errors alike. The outcome is an organization that not only withstands the digital storm but prospers—secure, compliant and efficient.
Charting the Course Ahead
Cyber threats will persist, but defenses must not waver. A data-driven, cost-effective strategy—grounded in governance, technology, and human expertise—charts the course ahead. For organizations that master this approach, the digital economy transforms from a threat-laden landscape into a realm of opportunity.
About the author: Welland Chu, Ph.D., CISA, CISM, is the Cybersecurity Specialist, APAC, at Thales (cpl.thalesgroup.com). He serves as Secretary and Vice President of Certification at the ISACA China–Hong Kong Chapter. Comments and discussions are welcome via email at Welland.Chu@thalesgroup.com.
