Introduction
Many essential, important, and critical services, such as energy, water, finance, and entities providing domain name registration services leverage information and communication technology (ICT). The resilience of this technology is essential to ensure uninterrupted provision of essential services. Outages and cybersecurity incidents in these sectors can lead to significant health, safety, financial, legal, reputational, and operational harm for affected individuals and enterprises.
To address the continuity of vital services, some jurisdictions have enacted directives and regulations applicable to certain entities. In the European Union, two key pieces of guidance in this area are the Digital Operational Resilience Act (DORA) and the Security of Network and Information Systems (NIS2) Directive.
DORA applies to the financial sector, while NIS2 is not limited to the financial sector and is aimed at essential and important entities. Enterprises may be subject to DORA, NIS2, neither, or both. Because it is a regulation, DORA is more prescriptive than NIS2. It outlines specific obligations for enterprises. In contrast, NIS2 is a directive, which means it provides goals that EU countries must achieve, but it is the responsibility of EU member states to create laws that help achieve these goals.1 Note that DORA also has some supplementary EU Commission-delegated regulatory technical standards (RTS) and supporting guidance, and these are legally binding.2 NIS2 has one implementation regulation relating to technical and methodological requirements.3
NIS2 replaced the original NIS1 directive. NIS2 has a broader scope than its predecessor, incorporating public electronic communications services, digital services, critical product manufacturers, postal services, and public administration.4
Another important European directive, the Payment Services Directive (PSD), is aimed at electronic payments. While this directive has an impact on many enterprises across the European Union and enterprises could be subject to PSD in addition to NIS2 and/or DORA, the latest version, PSD3, is currently in draft form5 and is out of scope for this white paper.
NIS2 and DORA compliance can support resilience, continuity, and risk management activities. Enterprises covered by NIS2 and DORA should learn their obligations to ensure resiliency, maintain customer access to their services, and avoid potential penalties for noncompliance.
Scope
NIS2 and DORA were enacted in the European Union, but they may have impacts for enterprises around the world. This is especially true for third parties working with entities in the European Union that are subject to NIS2 or DORA.
NIS2, which impacts enterprises that provide their services or conduct activities in the European Union, may apply to some enterprises in the financial sector, but its scope is larger than DORA’s. NIS2 applies to entities that are considered essential and important.6 Sector and enterprise size determine whether an entity is considered essential or important, but these are not the only factors in the decision. Other factors include if an entity is the sole provider of a service or if a disruption to the entity’s service could have a significant impact on public order, public security, or public health, among other factors.
Figure 1 shows which sectors are considered high criticality and which are critical according to the NIS2 directive.7
Figure 1: NIS2 Sectors
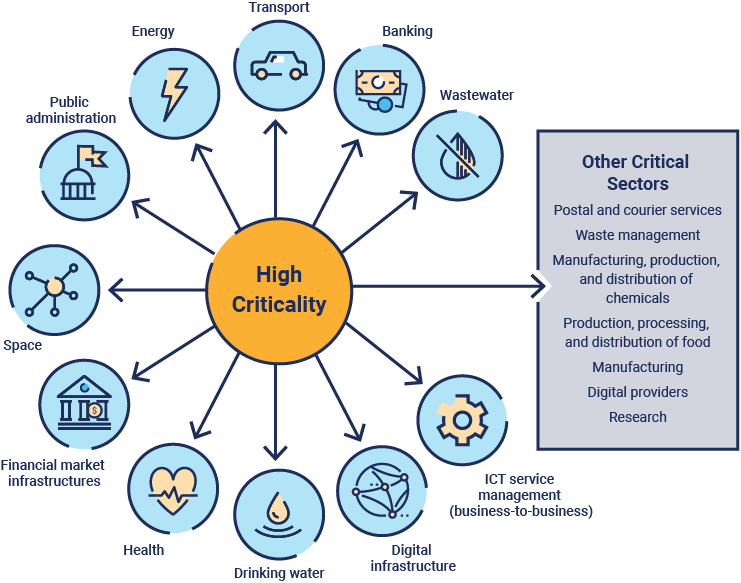
DORA applies to entities in the financial sector, including credit institutions, payment institutions, and investment firms.8
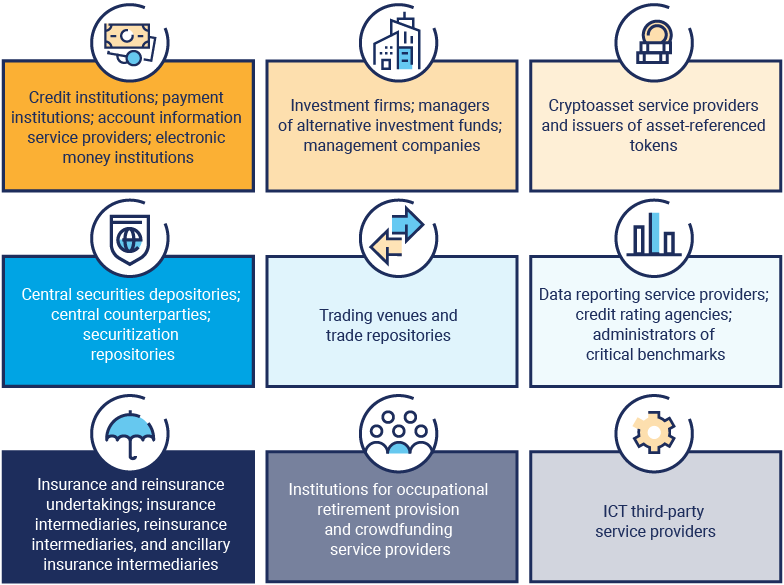
Figure 2 shows the financial institutions in the scope of DORA. Note that some micro and small- or medium-sized enterprises are not subject to all aspects of DORA or may have different obligations.9
Figure 2: DORA Scope
Risk Management, Business Continuity, and Disaster Recovery
To promote a harmonized approach to risk management across the European Union, NIS2 and DORA have certain requirements related to risk management. NIS2 calls for putting adequate measures in place to address risk to network and information system security. This includes developing policies related to risk analysis and assessing the efficacy of cybersecurity risk management measures.10
In contrast, DORA has several specific requirements related to establishing and maintaining an ICT risk management framework. This framework must, at a minimum, include strategies, policies, procedures, ICT protocols, and tools needed to protect information and ICT assets. The framework must ensure ICT management, control, and internal audit functions are adequately segregated, and the ICT risk framework must be:11
- Documented
- Reviewed at least annually12 and after major ICT-related incidents
- Subject to internal audit
The ICT risk management framework must incorporate a digital operational resilience strategy that establishes how the framework will be implemented. This strategy must include:13
- An explanation of how the framework can support the enterprise’s business strategy and objectives
- The ICT risk tolerance level
- Information security objectives, including key performance indicators (KPIs) and key risk indicators (KRIs)
- The ICT reference architecture
- The methods in place to detect, prevent, and protect in the event of an ICT-related incident
- The current state of digital operational resilience
- Digital operational resilience testing
- A strategy for communicating and disclosing ICT-related incidents
Employee training is a vital part of risk management, as humans are often the weakest security link. Tailoring security-related training based on roles and responsibilities is vital to ensure all staff understand how they can support enterprise security. DORA requires organizations to develop ICT security awareness programs and digital operational resilience training as part of the employee training program. All employees and senior management must complete this training, which should contain content appropriate to their roles.14 NIS2 also requires essential and important entities to offer training related to cybersecurity risk management.15
Tailoring security-related training based on roles and responsibilities is vital to ensure all staff understand how they can support enterprise security.DORA calls for continuous monitoring of ICT systems and tools in an effort to minimize ICT risk.16 It also requires having mechanisms to detect anomalies and ICT-related incidents and that these mechanisms are tested regularly.17 Business continuity is a key element of operational resilience, and DORA has requirements around response and recovery. ICT business continuity plans and procedures must:18
- Provide for the continuity of critical or important functions
- Respond to ICT-related incidents in a timely manner to limit damage and facilitate resumption of activities and recovery
- Activate containment measures, processes, and technologies
- Estimate initial impacts, damages, and losses
- Communicate and conduct crisis management actions
Financial entities subject to DORA must establish an ICT business continuity policy and an associated ICT disaster recovery plan. For enterprises that are not microenterprises, this plan is subject to independent audit reviews. To validate ICT efforts, the ICT business continuity policy and ICT disaster recovery plan must be tested.
Financial entities subject to DORA must establish an ICT business continuity policy and an associated ICT disaster recovery plan.DORA also emphasizes the importance of backups, which are critical in the event of an incident. DORA requires financial entities to create a backup policy. This policy should include which data is subject to being backed up as well as the minimum frequency of the backup. This frequency should be determined based on the criticality of the information or the sensitivity of the data. Financial entities must also develop recovery methods.
Information and Cybersecurity
NIS2 and DORA both contain provisions about the security of network and information systems. Security is vital to ensuring customers can have uninterrupted access to service and have their information protected. To that end, NIS2 and DORA both have security-related obligations.
NIS2 requires enterprises to address security in a way that can prevent or minimize the impact of incidents. Per NIS2, enterprises must have:19
- Risk analysis and information system security policies
- Incident handling procedures
- Business continuity measures
- Supply chain security
- Security in network and system acquisition, development, and maintenance
- Assessments of cybersecurity risk management measures
- Cybersecurity training and cyberhygiene
- Encryption and cryptography policies and procedures
- Human resources security
- Multifactor authentication (MFA) or continuous authentication
DORA has multiple requirements related to the security of ICT systems and tools. These systems and tools must be continuously monitored, which can help identify potential service interruptions. Financial entities must define alert thresholds and criteria that would trigger ICT incident detection and response processes. Multiple layers of control must be enabled.
DORA requires that financial entities develop policies and protocols for strong authentication mechanisms. At a minimum, they must annually review the adequacy of classification of information assets as well as any relevant documentation.
Audits
Audits can help ensure that enacted measures achieve desired outcomes. NIS2 and DORA address audits pertaining to security and third parties. Enterprises that are considered essential entities under NIS2 are subject to regular, targeted, and ad hoc security audits. These audits may be conducted by an independent body or competent authority, and results must be made available to the competent authority.20 Important entities are also subject to targeted security audits by an independent body or competent authority, with results being made available to the competent authority.21
DORA allows financial entities and competent authorities to audit ICT third-party service providers.22 This is critical, as third-party issues could impact the financial entity, which, in turn, impacts their customers. Additionally, the ICT risk management framework is subject to internal audit. There must be a formal follow-up process to act upon any critical ICT audit findings. DORA requires that audit functions have the appropriate knowledge, skills, and expertise in ICT risk and that they are independent. ICT audit frequency and focus will vary based on the enterprise’s ICT risk. Note that microenterprises are exempt from many of these internal audit requirements.
DORA requires that audit functions have the appropriate knowledge, skills, and expertise in ICT risk and that they are independent.Incident Reporting
Reporting an incident to the appropriate authorities and affected people is a core component of operational resilience and supports transparency. Authorities may need to act to protect people and ensure vital services can still be provided, and it is crucial for them to know about incidents in the event of an adversarial state-sponsored attack. Incident details may also help others in the same industry prepare for or address these incidents should they experience them.
NIS2 and DORA both have requirements around incident reporting as well as specific time frames by which certain information must be provided to designated authorities.
The requirements in this directive and regulation help harmonize reporting obligations across the European Union, which could vary considerably from member state to member state.
NIS1 required member states to create one or more computer security incident response teams (CSIRTs). CSIRTs should participate in deploying secure information-sharing tools and, as appropriate, share relevant information with communities of essential and important entities.23 CSIRTs play a vital role in incident reporting.
If a significant incident occurs, enterprises subject to NIS2 must notify the CSIRT or competent authority of the incident. NIS2 defines a significant incident as one that causes or could cause severe operational disruption of services or financial loss and has affected or could affect natural or legal persons by causing considerable damage (material or nonmaterial).24
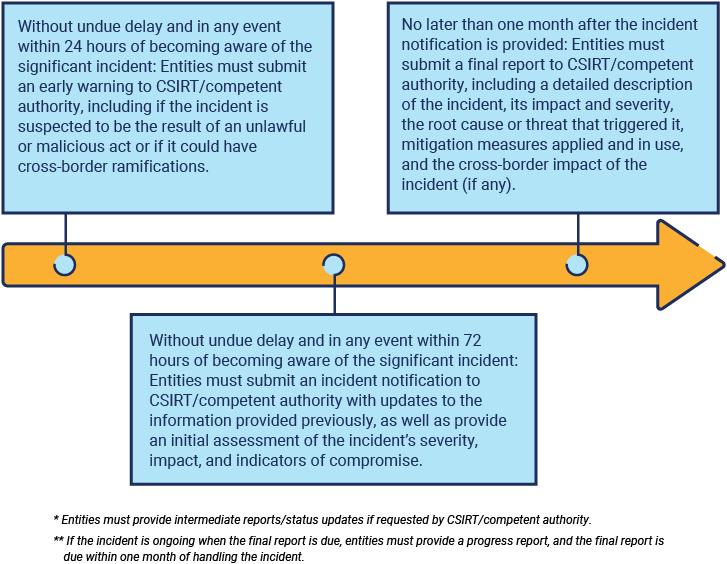
Figure 3 contains the significant incident reporting timeline under NIS2.
Figure 3: NIS2 Significant Incident Timeline
DORA defines major ICT-related incidents as those with “a high adverse impact on the network and information systems that support critical or important functions of the financial entity.”25 Financial entities must notify the relevant competent authority of any major ICT-related incidents. To promote resilience across the finance sector, financial entities may share significant cyberthreats with the relevant competent authority.26
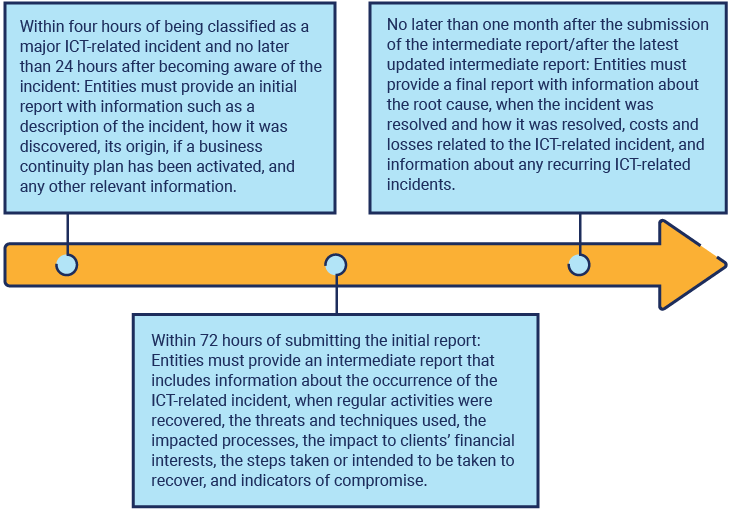
Figure 4 contains a DORA incident notification timeline for major ICT-related incidents.27
Figure 4: DORA Notification Timeline
A one-day time frame to notify authorities about significant incidents may be challenging for some enterprises. Comprehensive and regularly updated incident response plans are critical for compliance and resilience. Incident response plans must account for reporting obligations, and everyone involved with incident response should be aware of the content to report and reporting deadlines. Incident response testing and simulations can help enterprises identify areas for improvement and gauge their response capabilities.
Testing Obligations
Because proactive testing can help enterprises identify weaknesses and address them before they are exploited and result in system outages or harm to customers, some regulations include testing requirements. NIS2 does not specify testing measures that should be put in place. In contrast, DORA requires financial entities to conduct threat-led penetration testing (TLPT) every three years, at a minimum, and the scope of this testing may include ICT third-party service providers. This TLPT must cover critical or important functions and must be performed on live production systems.28
NIS2 does not specify testing measures that should be put in place. In contrast, DORA requires financial entities to conduct threat-led penetration testing (TLPT) every three years, at a minimum, and the scope of this testing may include ICT third-party service providers.Testing should incorporate criticality, business continuity, disaster recovery, and failover considerations. While three years is the minimum frequency for TLPT per DORA, conducting this testing more frequently can ensure alignment with industry best practice and allow enterprises to have more accurate and up-to-date insights on potential areas for improvement. It is recommended that, given the potential risk associated with testing on live production systems, the scope of such testing be carefully defined and managed to minimize any impact on ongoing operations.
In addition to TLPT, DORA also requires financial entities to test their operational resilience. Pen testing and operational resilience go hand in hand, and pen testing can provide valuable insights into operational resilience. Per DORA, operational testing must be risk-based and led by independent internal or external parties.29 Testing may include:30
- Vulnerability assessments and scans
- Open-source analyses
- Gap analyses
- Reviews of physical security
- Performance testing
- Compatibility testing
NIS2 does not require operational resilience testing, but this testing can help enterprises evaluate how they may respond to an incident, so it is a worthwhile activity even if it is not mandatory.
Third-Party Service Provider Requirements
Most enterprises rely on third-party products and services, and third-party outages can have widespread consequences. Contracts with third parties can help address resilience and clearly define risk-related obligations, and enterprises should ensure that service provider requirements are clearly spelled out in contracts and service-level agreements (SLAs).
NIS2 does not outline third-party service provider contractual requirements, but DORA requires that contracts with ICT service providers address risk. Specifically, DORA requires that financial entities have:
- Contractual provisions outlining how the ICT third-party service provider promotes accessibility, availability, integrity, security, and personal data protection
- A method to access, recover, and return data if the service provider discontinues operations
- Assistance in the event of ICT-related incidents related to the services provided
DORA requires that financial entities develop and regularly review their ICT third-party risk strategy, which must include a policy about the use of ICT services supporting critical or important functions provided by ICT third-party service providers.31 Understanding which services support critical or important functions is imperative to resilience.
NIS2 does not provide enterprises with ICT third-party risk requirements, but addressing third-party risk can support an enterprise’s cybersecurity posture. Reviewing the security posture of a third party may include setting specific contractual clauses (e.g., SLAs, right to audit) and requiring providers to provide proof of alignment with specific frameworks, standards, and/or regulations.
NIS2 and DORA align on what is defined as a critical ICT third-party service provider. NIS2 references DORA Article 31 in defining critical ICT third-party service providers. The criteria for determining if a third party is considered a critical ICT third-party service provider are:32
- The impact if the service provider experiences a large-scale operational failure
- The importance of the financial entities that rely on the ICT third-party service provider
- The ICT third-party service provider’s substitutability
Governance and Accountability
NIS2 and DORA have certain requirements around governance and accountability, especially related to senior management involvement. NIS2 specifies that management bodies at essential and important entities are responsible for approving cybersecurity measures and overseeing compliance. Additionally, these individuals may be held liable for noncompliance related to cybersecurity risk management.33
DORA requires management to oversee and be responsible for implementing the ICT risk management framework.34 As with NIS2, DORA requires that this management body remain knowledgeable on the applicable topics to best perform their oversight and implementation duties.
Information Sharing
To promote resilience and cybersecurity across an industry, enterprises may wish to share cybersecurity-related information with others in the industry. NIS2 and DORA allow this type of information sharing, but it is voluntary.
NIS2 allows entities in its scope to share information about the categories shown in figure 5.
Figure 5: Cybersecurity Information to Share
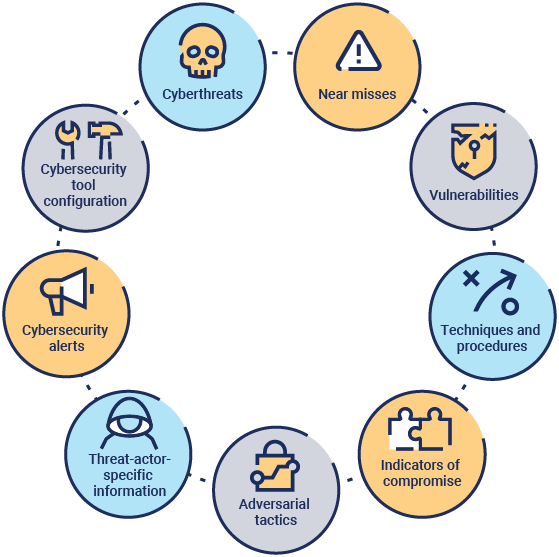
The purpose of information sharing should be to improve cybersecurity, or to prevent, detect, respond to, or recover from incidents or address their impact.35
Note that information sharing with other industry enterprises is voluntary, but significant incident reporting to competent authorities is mandatory.
Noncompliance
NIS2 has significant penalties for noncompliance. To complicate matters, the directive left many aspects to be executed by member states. Member states needed to transpose NIS2 into national law by 17 October 2024,36 but only Belgium, Croatia, Hungary, Italy, Latvia, and Lithuania met the deadline.37
Like many member states, enterprises also struggle with NIS2 compliance. A survey conducted in Ireland in October 2024 indicated that 38% of Irish businesses would not be prepared for NIS2 compliance.38
NIS2 allows member states to impose fines for infringing on certain parts of the directive.39
DORA allows competent authorities to determine penalties and remedial measures for noncompliance.40 This may include criminal penalties.41 DORA does not set specific fines or penalties for noncompliance.
Figure 6 shows the penalties for noncompliance with the NIS2 provisions around cybersecurity risk management measures and reporting obligations, which are outlined in Articles 21 and 23. Member states can set their own penalties for noncompliance with other aspects of NIS2.
Figure 6: NIS2 Noncompliance With Articles 21 and 23
Essential Entities |
Important Entities |
|---|---|
| Maximum fines of EUR 10,000,000 or 2% of total worldwide annual turnover, whichever is higher | Maximum fines of EUR 7,000,000 or 1.4% of total worldwide annual turnover, whichever is higher |
Conclusion
Enterprises must determine whether they are compliant with NIS2 and/or DORA, as noncompliance could lead to large fines and potential reputational damage. It is also important to note that enterprises that provide their products or services to financial entities or essential or important entities in the European Union may have additional obligations under NIS2 and/or DORA, so familiarity with the requirements of the directive and regulation is essential. Performing a gap analysis to evaluate an enterprise’s current security posture in relation to DORA and NIS2 requirements can be a crucial step to identifying areas of noncompliance and ensuring alignment with regulatory obligations.
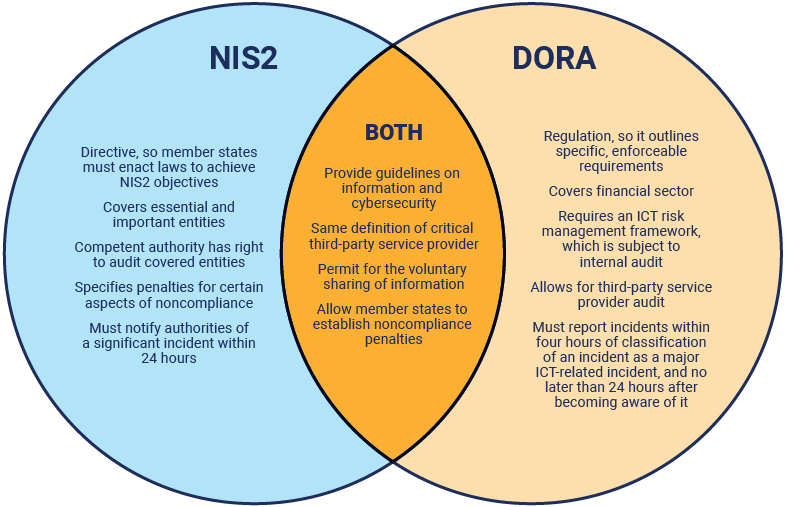
Figure 7 contains a high-level comparison of NIS2 and DORA.
Figure 7: NIS2 and DORA Comparison Overview
Even for enterprises not subject to NIS2 or DORA compliance, these frameworks provide valuable strategies for enhancing resilience and risk management practices. Regularly reviewing third-party risk, conducting penetration testing, and performing audits are essential practices that can significantly benefit enterprises of all sizes across all jurisdictions and industries.
