Introduction
Threat modeling is the procedure whereby an enterprise evaluates its architecture, systems, and assets with the mindset of a hacker. How could someone access this system without legitimate credentials? If a third party looked at the enterprise’s systems and assets with a critical eye, what are the obvious vulnerabilities? Threat modeling is a practical, proactive way for an enterprise to take control of its cybersecurity, make informed decisions, and prioritize properly. This paper can help all security professionals who need to know how to make threat modeling work and why it matters.
Threat modeling is the procedure whereby an enterprise evaluates its architecture, systems, and assets with the mindset of a hacker.The cybersecurity threat landscape is dynamic, with threats evolving faster than many enterprises can respond to. Too often, enterprises are reactive, addressing vulnerabilities only after they are exploited. To stay ahead, they must adopt a proactive, threat-informed approach to cyberoperations, leveraging structured threat modeling to anticipate and address risk effectively. Drawing on proven expertise, this white paper explores the strategic importance of threat modeling, demonstrating that it is one of many tools enterprises can use to avoid costly breaches or security incidents that lead to financial losses, reputational damage, and operational disruptions.
The Value of Threat Modeling
Today, many enterprises do the bare minimum, accepting the possibility of experiencing a breach.1 Tools and practices for addressing vulnerabilities include a combination of firewalls, intrusion detection systems, encryption, regular updates, and patches, while building a defense-in-depth security posture. Common cybersecurity standards like the Payment Card Industry Data Security Standard (PCI DSS),2 New York State Department of Financial Services regulations,3 and the Health Insurance Portability and Accountability Act (HIPAA).4 Structured threat modeling empowers enterprises to proactively identify relevant cyberthreats, assure compliance with standards, and build enduring resilience. By anticipating sophisticated attacks, threat modeling equips enterprises to secure critical assets and maintain operational success in an era of escalating cyberrisk, whether this involves a tech executive building resilient stacks or a business leader guarding revenue. Threat modeling helps protect data, stakeholder trust, and cash flow without adding unhelpful complexity. Threat modeling can assist enterprises with detecting security threats and making well-informed decisions about how to address them.5
Far from being a stand-alone technical exercise, threat modeling integrates foresight, risk prioritization, and actionable controls to safeguard critical assets such as customer data, proprietary technology, and operational continuity, while aligning security efforts with business objectives.
Threat modeling is a structured, proactive process that allows enterprises to identify, assess, and mitigate a potential security risk before it can be exploited. It involves analyzing business systems, data flows, and operational processes through an adversarial lens to uncover vulnerabilities, evaluate the likelihood and impact of an attack, and implement targeted defenses.
The Five Steps of Threat Modeling
Figure 1 illustrates a five-step strategic threat modeling process designed to integrate threat modeling into an enterprise’s business strategy.6
Figure 1: Five-Step Threat Modeling Process

This approach prioritizes understanding the business environment, identifying risk to critical assets, and embedding security into decision making, all while remaining technology or software agnostic.
Step 1: Identify Business Objectives and Define Threat Modeling Scope
The first step in threat modeling is to establish the scope and align it with the enterprise’s strategic goals. This is the time to take a close look at what is important to the enterprise and decide how extensive threat modeling should be.
Actions:
- Identify business objectives (e.g., market expansion, operational efficiency, customer trust).
- Determine the scope of the threat model, such as key business processes (e.g., supply chain, customer data handling, financial operations), critical assets (e.g., brand reputation, intellectual property), or strategic initiatives (e.g., mergers, new product launches).
- Engage leadership (e.g., C-suite executives, board members) to ensure that threat modeling supports corporate priorities.
- Document the scope, including stakeholders (e.g., employees, partners, regulators) and external dependencies (e.g., vendors, third-party services).
Outcome: A clear statement of what the enterprise is protecting and why, with leadership buy-in to prioritize security as a strategic enabler.
Example: A financial institution identifies the objectives of enhancing profitability and ensuring privacy compliance. It defines the threat modeling scope as securing online banking platforms and transaction data against ransomware and breaches.
Step 2: Map the Business Ecosystem
The second step entails creating a high-level model of business operations to understand how value is created and where risk may emerge. In this important step, business assets are identified to better understand what needs to be protected.
Actions:
- Develop a visual representation (e.g., process flow diagram, value chain map) of key business processes such as procurement, sales, or HR. Include inputs (e.g., raw materials and data), outputs (e.g., products and services), and interactions with external entities (e.g., suppliers and customers).
- Identify critical assets within these processes, such as proprietary data, physical infrastructure, or employee expertise.
- Define trust boundaries, such as those for internal departments vs. external partners, where control over assets or processes diminishes.
- Assess and document the risk of external dependencies in the ecosystem, such as third-party data providers, open-source model repositories (e.g., Hugging Face), or cloud service providers (e.g., AWS, Azure). Evaluate their reliability, security practices, and potential vulnerabilities (e.g., supply chain attacks, unverified data sources) to prioritize mitigation strategies.
Helpful tools include whiteboards or general diagramming software for collaborative mapping sessions with cross-functional teams.
Outcome: A comprehensive map of the business ecosystem, highlighting assets, processes, and boundaries that are vulnerable to threats.
Example: A financial institution maps its artificial intelligence (AI) fraud detection system for its online banking platform. A data flow diagram visualizes transaction data inputs processed by a cloud-based inference server and an AI model trained on proprietary datasets. Critical assets include the AI model and inference server. Trust boundaries are set between the server and a third-party cloud provider. The team assesses the cloud provider for supply chain risk and reviews the map quarterly to address new data sources and identify risk such as data leakage at the cloud boundary.
Step 3: Identify and Prioritize Threats
Step three is crucial in the identification and prioritization of threats. It includes evaluating the likelihood and potential impact of each identified threat.
All identified threats need to be assessed for the potential consequences of security incidents. This is important for making informed decisions about how to manage and prioritize threats effectively.
Actions:
- Conduct brainstorming sessions with stakeholders (e.g., operations, finance, legal) to identify what could go wrong. Consider threats such as fraud, regulatory violations, reputational damage, and operational disruptions.
- Use an established framework (e.g., STRIDE) as a guide to common categories of risk.
- Evaluate threats using a qualitative risk matrix (e.g., likelihood vs. impact).
- Prioritize threats that could derail strategic objectives or cause significant financial, legal, or reputational harm.
Outcome: A ranked list of threats based on impact (e.g., financial loss, privacy breach), likelihood, and strategic objectives, with a clear rationale for such ranking.
Example: Once an enterprise’s high-priority threats are identified, data is ranked by its likelihood of risk exposure (frequent data updates) and impact (financial loss, privacy breach). This allows prioritization of the mitigation strategies.
Step 4: Develop Mitigation Strategies
This step utilizes all the threat information identified to create a workable plan of action to address the threats. This reduces not only the likelihood of an attack but also the damage inflicted if one occurs.
Actions:
- Assign risk owners to oversee mitigation efforts for threats exceeding the enterprise’s risk appetite and tolerance (e.g., zero tolerance for privacy breaches). Confirm these risk boundaries with stakeholders to prioritize controls, ensuring accountability for systemic risk management.
- Develop countermeasures such as hardening, compensating controls, or supplemental education and awareness training for threats exceeding risk tolerance.
- Integrate mitigations for threats exceeding acceptable risk levels, guided by risk appetite and tolerance, to focus resources on critical risk (e.g., privacy breaches) and to minimize disruption.
- Balance cost and effectiveness, prioritizing controls that protect critical assets without undermining operational efficiency.
- Document a risk treatment strategy, including timelines, budgets, and responsible parties.
Outcome: A set of actionable mitigation plans that combat threats and systemic risk exceeding the enterprise’s risk appetite and tolerance. Plans should include clear ownership, integration into processes, and alignment with strategic objectives.
Example: A financial institution implements robust data validation to mitigate data poisoning in its fraud detection system, but the results still exceed its risk tolerance for privacy breaches; it therefore deploys multicloud redundancy to address systemic cloud outages. Security engineers oversee controls, which are integrated into data governance, reducing financial and compliance risk while supporting real-time fraud detection.
Step 5: Review, Validate, and Iterate
Reviewing the threat modeling process is very important. The process should not be static; it needs to change as the threat landscape changes.
An evaluation of the model’s ability to identify and prioritize potential threats accurately is also crucial. The sharing of information derived from a threat model needs to be shared with everyone involved in the process, including upper management.
Actions:
- Conduct regular reviews (e.g., quarterly, after model updates or new data integrations) with stakeholders to validate the threat model against new risk (e.g., emerging adversarial techniques) or system changes, ensuring that risk aligns with the enterprise’s risk appetite and tolerance (e.g., zero tolerance for privacy breaches).
- Test simulations or conduct tabletop exercises to verify the model’s effectiveness against threats and systemic risk, confirming that residual risk remains within tolerance levels.
- Identify gaps or inefficiencies by collecting feedback from stakeholders, fostering a culture of security.
- Update the threat model to reflect new strategic initiatives, market conditions, or emerging threats (e.g., new regulations and competitor actions).
- Report progress to leadership, detailing validation results, residual risk, and alignment with risk appetite, to secure resources and maintain support for ongoing threat modeling, ensuring that strategic objectives are met.
Outcome: A dynamic threat modeling process that evolves with the business, ensuring sustained protection of strategic objectives.
Example: An enterprise reviews its fraud detection system’s threat model after integrating a new transaction dataset in May 2025. It tests data validation against simulated attacks and updates multicloud redundancy to address potential cloud outages, which previously exceeded privacy breach tolerance. Security engineers validate controls and ensure compliance, reporting the results to leadership.
Strategic Considerations
By prioritizing business processes and risk scenarios over an exclusive focus on technology and assets, the five-step threat modeling framework enables enterprises to proactively manage risk in a way that aligns with risk appetite and tolerance and sustains strategic objectives such as privacy compliance and financial stability in a dynamic ecosystem. It is important to have both stakeholder engagement in—and sufficient resources allocated to—any threat modeling exercise.
It is important to have both stakeholder engagement in—and sufficient resources allocated to—any threat modeling exercise.Stakeholder engagement and resource allocation are defined as follows:
- Stakeholder engagement—Engage diverse stakeholders (e.g., data scientists, security engineers, compliance officers) with clear accountability for identifying threats, implementing mitigations (e.g., data validation) and validating controls, to foster a security culture aligned with risk appetite and tolerance.
- Resource allocation—Balance investment in threat modeling with other business priorities, focusing on high-impact risk to justify costs to leadership.
Fostering a Security-Conscious and Risk-Driven Culture
To implement successful threat modeling, enterprises must cultivate a security-conscious and risk-driven culture by framing threat modeling as a strategic business process, not a burden. Accountable leaders (e.g., security managers) should conduct regular workshops and cross-functional collaboration (e.g., with data science and compliance teams) to garner employee buy-in, heighten risk awareness, and prioritize mitigation for risk that exceeds tolerance levels, ensuring alignment with strategic objectives.
To implement successful threat modeling, enterprises must cultivate a security-conscious and risk-driven culture by framing threat modeling as a strategic business process, not a burden.Threat Modeling at the Executive Level
Executives play an important part in threat modeling. They do so through strategic leadership and governance, safeguarding mission-critical assets and ensuring organizational resilience. Their responsibilities include:
- Setting a strategic direction—Establish the vision for security, aligning threat modeling with objectives such as privacy compliance, financial stability, and real-time fraud detection.
- Determining risk appetite—Set risk boundaries to guide threat prioritization and resource allocation.
- Approving priorities—Approve mission-critical assets and processes (e.g., real-time fraud detection workflows) recommended by technical teams.
- Overseeing governance—Approve prioritized risk and mitigation strategies (e.g., data encryption, multicloud redundancy), ensuring alignment with the five-step framework.
- Fostering culture—Promote a security-conscious culture through leadership, enhancing stakeholder trust.
- Representing externally—Communicate security priorities to regulators and shareholders, reinforcing brand integrity.
Tying It All Together
Effective cybersecurity is about protecting what matters most. Enterprises must first define their business priorities, such as revenue streams, operational uptime, customer trust, or regulatory compliance. Then, they must map cyberrisk to these critical objectives. For example, if uptime is a business imperative, leadership should ask: What could take the systems offline? Scenario-based threat analysis can help connect risk to tangible outcomes—dollars lost, reputational damage, or noncompliance penalties.
This approach grounds technical conversations in business impact, ensuring alignment among IT, security, and the executive team. Threat modeling is not just about firewalls and servers; it is about enterprise protection. It bridges the gap between technical vulnerabilities and strategic outcomes, helping to reduce breach response times, streamline audit readiness, and minimize regulatory exposure. It also strengthens an enterprise’s ability to innovate securely.
Breaches can stall product launches, shake investor confidence, invite penalties (e.g., General Data Protection Regulation [GDPR] fines), and send customers running. However, when enterprises implement threat modeling effectively, the return on investment (ROI) is clear. By providing insight into how cyberattacks could happen before they occur, threat modeling helps an enterprise prepare and reduces the risk of experiencing a breach.
One might assume that this requires deep technical expertise, but that is not true. Some of the most successful threat modeling programs have been championed by executives with little hands-on technical background but who bring curiosity, discipline, and leadership to the process.
Learning From the Mistakes of Others
An excellent way to jump-start a threat modeling initiative is to conduct a tabletop exercise that uses a real-world, industry-specific breach the team can walk through. Verizon’s “2025 Data Breach Investigations Report” is a great place to start.7
The team should be prepared to answer the following questions:
- If this breach happened, where would the enterprise be exposed?
- Could the team detect it?
- Would the team be able to contain the breach before damage escalates?
These scenario-based exercises are often more enlightening than an audit or compliance checklist.
History is filled with lessons learned too late. High-profile incidents such as those affecting Equifax, Target, and Colonial Pipeline were not the result of attackers being “too sophisticated.” Rather, they stemmed from a lack of proactive, structured questioning—“what-if” conversations that did not take place at the right time.
How to Include the Executive Team in Threat Modeling
Ultimately, threat modeling falls to the chief information security officer (CISO). It requires executive leaders who ask the right questions, foster cross-functional collaboration, and hold the enterprise accountable for protecting what matters most.
Figure 2 illustrates how to prepare and execute a plan that involves executive staff in the threat modeling process.
Figure 2: Involving the Executive Team in Threat Modeling
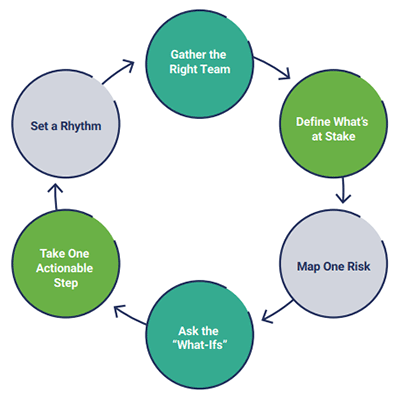
These steps include the following activities:
- Gather the Right Team—First, enterprises need to gather the executive team. This team might include the chief executive officer (CEO), chief financial officer (CFO), chief operations officer (COO), and a strong IT or security leader. The objective is to assemble business and technical minds in the same room to align priorities and enable effective, risk-informed decision making.
- Define What’s at Stake—Shift the conversation from technology to business value. Clearly define what must be protected—customer trust, financial stability, operational continuity, and brand reputation. These are the enterprise’s mission-critical assets, not just servers or endpoints.
- Map One Risk—The security team selects one high-impact business function—such as customer login or payment processing—and maps out its end-to-end process. Once the process is clearly visualized, the team identifies potential vulnerabilities and associated risk scenarios that could impact its integrity, availability, or confidentiality.
- Ask the “What-Ifs”—Executives should engage in scenario thinking:
- What if this function becomes unavailable?
- What if sensitive data is leaked or altered?
- What would be the regulatory, reputational, and financial impact?
- Take One Actionable Step—Pick one tangible improvement, have the security team set up an alert, and run a phishing drill. These small wins often build the momentum needed for full enterprise buy-in.
- Set a Rhythm—Institutionalize threat modeling as a regular governance process. Periodic reviews—especially after major events such as vendor onboarding, new product launches, or entering new markets—keep risk assessments aligned with business changes. Threats evolve rapidly; threat modeling must evolve too.
CISOs and CIOs and Threat Modeling
Veterans in cybersecurity understand that threat modeling is not a side project to be addressed only when time permits. It is a fundamental part of proactive risk management. Every executive, not just those in technical roles, has a vested interest in cyberrisk.
Whether driven by the CISO, the chief information officer (CIO), or another executive, threat modeling is a core management responsibility. It enables enterprises to move from hoping they are secure to knowing where they are exposed to risk. More importantly, it aligns directly with what matters most, such as uptime, customer trust, and operational continuity. Threat modeling is not merely a technical exercise; it is a business-critical discipline.
Three Practical Plays for CISOs and CIOs
The following are three practical strategies CISOs and CIOs can consider when implementing threat modeling.
1. Make Risk Part of the CISO Strategy
The CISO leads by guiding the team to identify the enterprise’s top cyberthreats, such as phishing, insider threats, and third-party exposures. These vulnerabilities are then prioritized based on potential business impact, and existing controls (e.g., multifactor authentication [MFA], endpoint protection) are mapped accordingly.
For CISOs, threat modeling provides clarity amid complexity. It focuses on the most consequential threats rather than exhaustively cataloging every theoretical vulnerability. This targeted approach leads to smarter budgeting, sharper execution, and fewer operational surprises.
Threat models foster trust—internally across business units and externally with regulators, auditors, and the board. They reveal where serious gaps exist and where risk is minimal, helping security leaders allocate resources effectively. Without this structured view, enterprises can waste time and money on low-impact issues while leaving critical exposures unaddressed.
2. Help CIOs Grow Effectively
CIOs are constantly tasked with introducing new technologies—from AI to the Internet of Things (IoT)—while ensuring that systems remain efficient, compliant, and secure. To support this growth, CISOs play a crucial role in embedding cybersecurity in the CIO’s decision-making process.
Before product launches or vendor onboarding, the CISO can help the CIO run structured risk checks: mapping data flows, identifying access points, and analyzing what could go wrong. With these forward-looking exercises, potential risk factors surface early—before implementation—preventing future data leaks, compliance violations, or costly emergency responses.
By working together, the CISO and CIO ensure that new technologies scale without introducing surprise vulnerabilities. A missed application programming interface (API) review, for instance, can result in more damage than the entire project is worth. With a shared threat modeling approach, both leaders can align innovation with security, protect the enterprise’s reputation, and make smarter investments.
3. Align CISOs and CIOs to Build Real Resilience
To foster resilience, CISOs and CIOs should colead joint working sessions, starting with a single initiative, such as a cloud migration or new vendor integration, and walk through key questions together: Where could this fail? What are the consequences if it does? The outcome does not require elaborate documentation—just clear, actionable planning. Many enterprises have developed robust security roadmaps in a single afternoon through the use of this kind of collaborative threat modeling.
This alignment has a ripple effect across the enterprise, benefiting finance, operations, customer service, and beyond. When CISOs and CIOs are misaligned, accountability gaps emerge, and unresolved risk can fall between departments. In the aftermath of incidents, this often leads to blame rather than solutions.
Conversely, when security and technology leaders work in sync, risk is identified early, enabling the enterprise to grow quickly—and safely. Threat modeling is not a luxury or an optional add-on; it is a strategic safeguard that keeps both innovation and business continuity on track. The key is to start small: pick one achievable step, build momentum, and embed this rhythm into decision making. In a landscape where adversaries move fast, resilience is achieved by those who move faster together.
Threat modeling is not a luxury or an optional add-on; it is a strategic safeguard that keeps both innovation and business continuity on track.How Does an Enterprise Keep Up?
Technology changes fast, and many teams are already moving at full speed just to keep up. However, keeping up does not require a complete overhaul of the roadmap. Even under pressure, fast-paced start-ups, healthcare organizations, and gaming companies have all managed weekly updates by picking one area at a time and staying consistent.
Threat modeling, when properly integrated, becomes less of a stand-alone project and more of a natural part of agile development. It helps teams identify meaningful risk early, apply targeted mitigations, and ship secure products without slowing down innovation.
Operationalizing Threat Modeling
Whether the goal is running IT, leading security, or just trying to keep the lights on, threat modeling is a practical tool that protects systems, saves time, and preserves reputation.
There are four time-tested strategies for transforming modeling from a one-off task to a consistent part of operations.
1. Start Small and Stay Focused
Effective threat modeling begins with a manageable scope and a clear purpose. Assemble a small team that includes representatives from product engineering, security, and relevant business functions. Together, create a visual diagram of the selected system, such as a customer portal or billing API, mapping out data flows, trust boundaries, and external integrations. It is very important to identify why the system matters (e.g., compliance requirements, customer trust, business continuity). This keeps the conversation grounded in business impact.
The number one mistake is trying to apply threat modeling to everything at once. This is overwhelming and ineffective. A team can spend weeks analyzing edge cases while a basic login flaw sits wide open. A tighter scope helps teams address the areas where risk matters most (e.g., customer apps, payment systems, or anything that holds sensitive data).
2. Focus on the Threats That Matter
After mapping the data flow, the next step is to identify and prioritize threats that pose the greatest risk to business objectives. Using structured methodologies—such as Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege (STRIDE) for application-level threats or Process for Attack Simulation and Threat Analysis (PASTA) for business-aligned risk scenarios—helps teams assess threats in context, not in isolation.
MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) is a great option for an operations team that is already using it. It sorts threats by likelihood and impact. A simple red/yellow/green classification system can be implemented.
The goal is not to list every possible vulnerability. Rather than brainstorming 100 theoretical threats, the goal is to find those that are likely, impactful, and fixable. When teams get distracted by low-risk cases, critical issues such as privilege escalation flaws can go undetected.
3. Turn Risk Into Fixes
To fix issues before they cause damage, security must be tied directly to critical business operations. Top risk factors are turned into action items through prevention (e.g., access controls and MFA), detection (e.g., monitoring and alerts), and recovery (e.g., backups and isolation plans). Enterprises should log tickets and make it part of development and operations.
When teams identify major risk, they cannot afford to let it sit until the next incident review. For example, one company cut its ransomware exposure down to zero by incorporating MFA into its rollout plan.
Effective threat modeling is not just about identifying problems; it is about closing the loop with actionable, prioritized fixes that protect the business.
Effective threat modeling is not just about identifying problems; it is about closing the loop with actionable, prioritized fixes that protect the business.4. Implement Continuous Threat Modeling
To remain effective, threat models must evolve alongside the systems they protect. Diagrams and documentation should be stored in secure, accessible, and searchable locations such as Confluence or Google Drive (with appropriate access controls) that support versioning and collaboration. Security should never be compromised for convenience. Threat models should be reviewed regularly—at least monthly—and after any significant changes such as new vendor integrations, system upgrades, or architectural shifts. Without timely updates, even well-built models can become outdated and lose effectiveness. Ownership should be assigned to an individual embedded in the team.
Consistent upkeep ensures that risk assessments remain aligned with the current environment and that mitigation plans are always relevant. Like any critical asset, threat models must be maintained, not just created.
Threat Modeling by Industry
Whether an enterprise is involved in healthcare, retail, financial technology (fintech), or some other sector, threat modeling must be tailored to the specific risk factors and regulatory demands of the industry. A one-size-fits-all approach often fails to address the nuances that matter most. Effective industry-specific threat modeling must focus on the enterprise’s core business.
Different industries have different priorities. For example, banks must protect against fraud, and medical clinics must safeguard protected health information (PHI). Banks may focus on APIs, healthcare facilities may focus on electronic health records, and retail enterprises may focus on carts and payments. Each industry has unique digital touchpoints and risk priorities.
Tailored threat modeling aligns security with the threats that could truly disrupt business operations, whether that involves patient safety, customer trust, or financial transactions. Unlike generic frameworks, industry-aligned models focus on what could realistically go wrong and how it would impact the business. This allows enterprises to avoid wasted resources, protect what matters, and stay resilient under pressure.
Tailored threat modeling aligns security with the threats that could truly disrupt business operations, whether that involves patient safety, customer trust, or financial transactions.Identifying compliance requirements also helps tailor threat modeling by industry. Teams can first identify compliance requirements (e.g., PCI DSS, HIPAA, system and organization controls [SOC] 2) and use this information to map out how data relates to those requirements. Then, they can align threat modeling according to best fit (e.g., asset first, threat first).
The National Institute of Standards and Technology (NIST) and the Center for Internet Security (CIS) provide helpful guides for this purpose. Documenting diagrams, controls, and evidence can ensure that existing compliance requirements are being met and that the enterprise’s systems remain aligned with applicable frameworks and standards.
Conclusion
Amid relentless cyberrisk, threat modeling is a practical way for any enterprise to thrive, not just survive.
Threats do not wait for perfect timing. The breaches affecting Equifax, Target, and Colonial Pipeline prove that ignoring risk costs more than facing it. It is important to start small and focus on what matters most.
The good news is that enterprises need not overhaul their operations to make progress. Threat modeling succeeds through intent, not complexity. It starts by choosing one system, gathering the right people, mapping data flows, and asking what could go wrong. Then, the goal is to fix one issue at a time. Momentum builds from there.
This approach empowers enterprises to move from reactive firefighting to proactive defense, protecting what truly matters, whether that is customer trust, operational continuity, or strategic goals. Threat modeling gives business leaders control over the threats that matter most—and the confidence to grow securely.
