New tech legislation, the increased importance of cybersecurity, and the due diligence required during mergers and acquisitions impose growing demands on investors’ and supervisory bodies’ time and resources. The number of enterprises subject to regulatory requirements has increased significantly under existing and new legislation such as the EU General Data Protection Regulation (GDPR)1, the Security of Network and Information Systems (NIS) regulations NIS 1 and NIS 2,2 and the EU Digital Operational Resilience Act (DORA).3 In some cases, the national competent authority (NCA) has not yet been identified. Likewise, cybersecurity adds complexity for investors, financiers, and buyers in the acquisition market, necessitating more thorough due diligence regarding an enterprise’s technology stack. There are three methods proposed herein to relieve this burden: Enterprises should improve governance, form a digital due diligence strategy, and create proactive in-control statements via a top-down approach.
What is the Problem, and Who is Affected?
Regulatory and industry requirements related to cybersecurity are skyrocketing. They include standards imposed by DORA,4 the International Organization for Standardization (ISO) standard ISO 27001,5 the Payment Card Industry Data Security Standards (PCI DSS)6, and many others. Managing all of these regulations is a complex process for enterprises and for the regulators that need to supervise their correct implementation. The number of enterprises affected in the European Union alone runs into the millions (figure 1).7
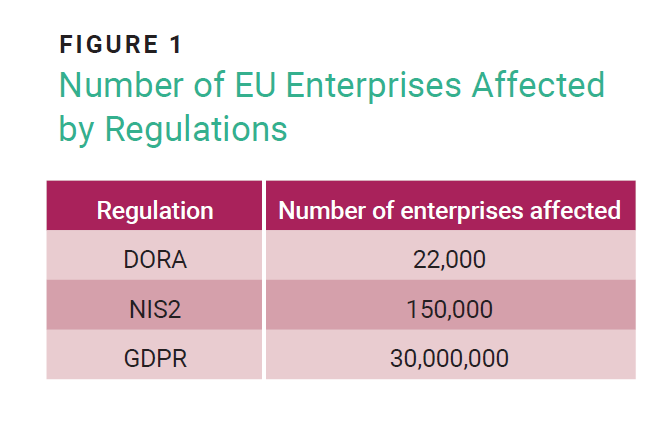
As made evident by the enactment of the EU GDPR, enterprises can complete the necessary paperwork to demonstrate compliance. However, the difficulty lies in implementing the right technology and sufficient processes, capabilities, and structures to adequately monitor and report on an enterprise’s data protection and security efforts. This is highlighted by the fact that many EU GDPR violations relate to failure to implement the technical and organizational measures required to ensure information security. Implementing information security controls is cumbersome for many enterprises due to scarce resources and limited capabilities.
GDPR and upcoming regulations will only be sustainable by requiring enhanced due diligence and mandatory, proactive submission of in-control statements. Given the number of regulated enterprises and their associated burdens, the only way forward is an inverse burden of proof: Organizations must be able to prove that they comply.
As enterprises evolve in the digital age, the ability to assess and effectively manage potential cybersecurity risk has become fundamental to ensuring the success, integrity, and sustainability of mergers, acquisitions, and ongoing operations.Good Governance
Complying with all applicable regulations while implementing proper security management is a difficult task. One way to navigate this complexity is to use an existing framework as the basis for managing cybersecurity, whether within a specific country or a specific industry. For example, when the United States experienced a major attack on the Colonial Pipeline,8 adherence to NIST SP 800-053 and NIST 800-2079, principles became mandatory after a presidential executive order. Europe is moving in the same direction, taking a similar top-down approach to digital security. This is comparable to what happened after the MCI WorldCom10 and Enron11 accounting scandals, which led to the passage of the Sarbanes-Oxley Act (SOX)12 in the United States to improve auditing and public disclosure requirements.
Treating cybersecurity management in the same way as financial reporting standards ensures a structured and comprehensive approach that provides monitoring that can detect deviations or malfunctions. It also encourages good stewardship among owners.
Additional Complexity in the Acquisition Market
In mergers and acquisitions, buyers impose strict conditions on entrepreneurs seeking to sell their enterprises, including requirements related to data and privacy.13 The heightened scrutiny of cybersecurity underscores the critical need for digital due diligence with regard to digital assets and comprehensive risk assessments. In mergers and acquisitions, even a single misstep can have profound consequences, leading to substantial financial losses and reputational damage.
Fortunately, more due diligence is also being performed for the technological departments of enterprises. This is not surprising, as technology is a growing factor in business processes and value drivers. Moreover, notorious examples, such as the acquisition of Yahoo by Verizon, have shown the far-reaching consequences of insufficient due diligence.14 This could have been prevented if previous audit reports, access and authorization practices, and segmentation of the network had been reviewed more thoroughly.
In the case of Yahoo, attackers successfully executed a spear-phishing attack using a Yahoo employee’s credentials to gain access to backed-up data. This example shows the importance of the principle of least privilege. Overprivileged user rights significantly simplify cybercriminals’ ability to get into and, through system hopping, explore the entire network if there is no network segmentation. Breaches such as the one experienced by Yahoo can have serious consequences. This and a separate breach caused Yahoo to lose US$350 million in the deal with Verizon.15
Arguably, all business processes are, to some extent, dependent on technology and digital processes. Business and private life are seamlessly integrated, and so is data, including intellectual property or confidential data that is valued as goodwill in an acquisition process. This data can be located anywhere, such as on in-home devices or in smartphone cloud storage.
In this context, meticulous digital due diligence (i.e., identifying valuable assets and their protection mechanisms) is not merely a best practice, but an absolute necessity. As enterprises evolve in the digital age, the ability to assess and effectively manage potential cybersecurity risk has become fundamental to ensuring the success, integrity, and sustainability of mergers, acquisitions, and ongoing operations.
At its core, due diligence is designed to unearth any potential security risk. It serves as the foundation for various essential considerations in an acquisition, such as the enterprise’s valuation, and it identifies value drivers and any potential threats to them. Value drivers include intellectual property, software technology, automation capabilities, subscriptions, and unique market propositions.
Enterprises can enhance their operational efficiency in the long run by identifying security risk before an acquisition. This insight is invaluable, as security vulnerabilities can stall or, in extreme cases, halt an acquisition, and they can certainly influence the agreed-on price of the acquisition. Consequently, being aware of these weaknesses before the acquisition allows the seller to improve security measures. The buyer’s due diligence should assess and report on the entire technology stack at each layer (figure 2), including an exhaustive set of checkpoints such as:
- Hardening
- Access/authorization management
- Intellectual property protection
- Low/no/high code usage
- Code repositories
- Data modeling
- Software architecture
- Dynamic/static (code/pen) testing
- Control effectiveness/evidencing
- Automation
- Application-/user-/network-level segmentation
- Entitlement management
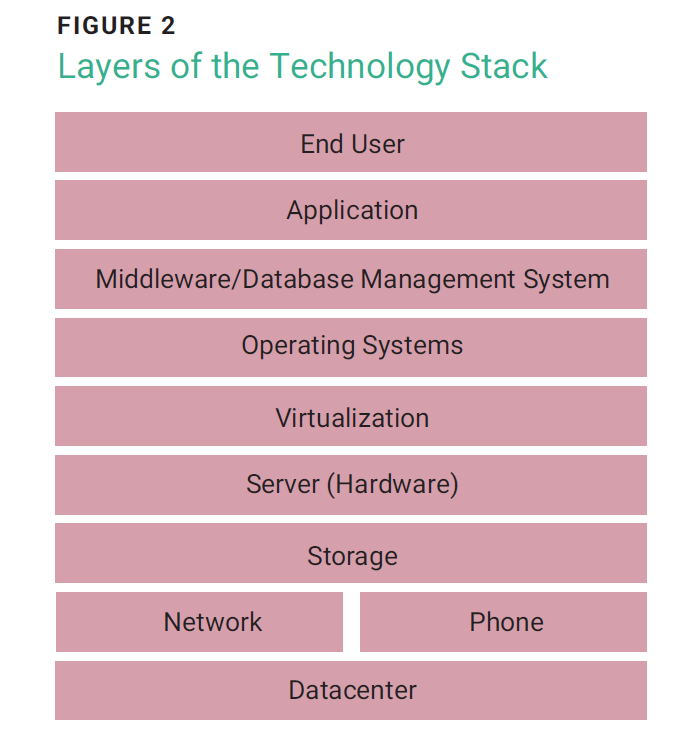
Proper digital due diligence significantly contributes to the seamless integration of the acquired entity into the buyer’s enterprise environment, enhancing business continuity, avoiding technology debt, and minimizing disruptions or the risk of buying a so-called pig in a poke16—something whose true worth is obscured.
Thorough due diligence on technology, processes, and human capabilities is instrumental in building trust and maintaining a good reputation. An acquisition involves assets, operations, and large quantities of customer and employee data. By identifying potential security risk factors and regulatory violations in advance, reputational damage can be prevented. This also includes the evaluation of vendor relationships, as these third-party connections can be the weak link in the supply chain.
Value drivers are largely dependent on the software technology in use, so it is important to assess secure software by design principles, or the use of good practices such as a software bill of materials (SBOM). The software should be diligently checked to avoid buying technical debt or an inferior software technology stack. Digital due diligence also encompasses technological aspects and includes evaluating the enterprise’s cybersecurity culture, processes, and awareness level among employees. This proved to be true in the case of the Marriott International acquisition, in which attackers likely gained unauthorized access to the Starwood guest reservation database via a phishing email.17 The breach took place in 2014, two years before the acquisition, but it was not discovered until after the deal was completed.
Digital due diligence is also pivotal in safeguarding intellectual property, particularly in acquisitions designed to acquire specific technologies. A notable cautionary tale is the case of DigiNotar. Its main assets—its certificates—were illicitly replicated, eventually leading to bankruptcy, leaving the acquiring party, Vasco, empty-handed. Comprehensive digital due diligence is crucial in establishing that intellectual property is legally and technically protected and retains substantial value. Awareness and deep knowledge of the technological and security status of the enterprise, its major suppliers, and the value-driving assets to be acquired can significantly improve the transition period.
How to Conduct Digital Due Diligence
Both the selling and the buying parties can smooth and accelerate the acquisition process. The selling enterprise can reveal its security status based on any framework (e.g., CIS 8, ISO 27001, ISO 27701) in the form of periodic statements indicating its control of digital security, risk, privacy, and audits via a structured method of testing and following up on audit findings. This is good practice in general, not only before an acquisition. This also allows the buyer and seller to monitor and track follow-up capabilities when specific vulnerabilities are detected, helping identify material risk that could threaten the investment.
The buying party should conduct digital due diligence to assess the enterprise’s in-control statements. The first step in this process is establishing the goal behind the acquisition. Does the buyer want to increase its market share, eliminate the competition, or acquire a specific technology? The next step is determining which systems, software, data, and other technological assets are needed to achieve its objectives. Then the buying party can log all highly valuable assets and their owners in a central repository, similar to what is done with financial assets.
Next, it is time to collectively assess the risk factors to which the assets are vulnerable. The final step is to evaluate the controls implemented in the enterprise based on a framework such as PCI DSS, ISO 27001, or NIST SP 800-53.
Financiers may require this thorough assessment to determine the value and potential technology debt of an enterprise. If investors wish to conduct a more high-level assessment of their own, however, they can seek to confirm that the following are true of the enterprise being acquired:
- Enterprise policies and technical procedures are in place, implemented, and maintained via testing
- An external security vulnerability assessment has been performed in the last 12 months.
- Strong user account and access management, measures are in place, including for high-privilege system
- Asset identification and classification are performed.
- Software security-by-design practices are in
- Segmentation of assets is performed and
- Audit findings are known and tracked for resolution via a structured process.
- Important third parties are known, assessed, and periodically evaluated in terms of risk and periodically evaluated in terms of risk and security.
In-Control Statements: A Solution for Both Regulators and Financiers
To perform digital due diligence, the use of in-control statements is recommended. These statements provide a quick overview of the status of controls in a privacy and security management system. In highly regulated environments such as finance, in-control statements are already common. They can verify and demonstrate to a supervisory authority that an enterprise’s accounting has been conducted truthfully and lawfully. In-control statements are useful tools because they save supervisory authorities time, resources, and money. These statements can be checked automatically, similar to the procedure for tax reports. Periodically, an audit is conducted to assess whether an enterprise has indeed provided truthful information, and the accountable persons must sign off on the findings.
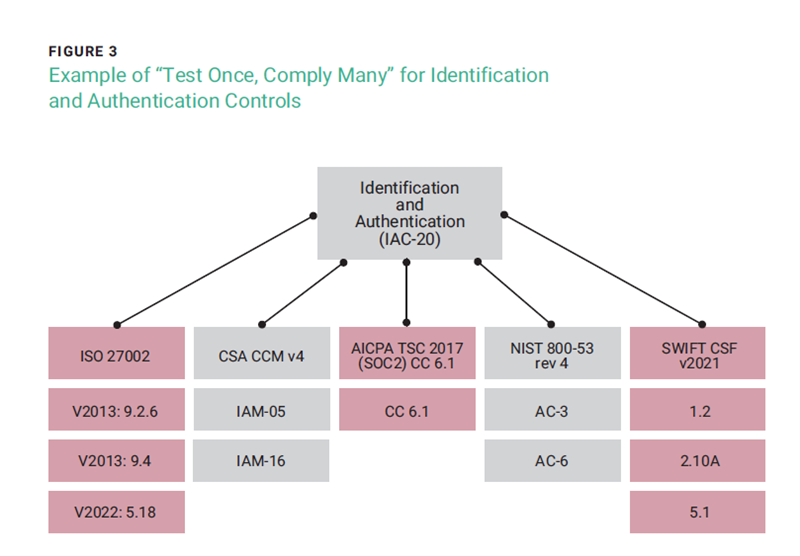
Every framework does not need to have its own in- control statement. There is often a certain amount of overlap in the controls they propose. This overlap can be mapped to understand where the frameworks coincide. For example, there may be one parent framework that corresponds with multiple child frameworks and their controls. Testing for a control in the parent framework ensures compliance with multiple other underlying controls—the “test once, comply many” principle (figure 3). This mapping can be integrated into technology and updated every time there is a change in the framework. This allows enterprises to submit just one in-control statement that attests to their adherence to a multitude of frameworks.
Conclusion
Due diligence and the delivery of in-control statements are conducted in part by monitoring and reporting the status of the entire technology stack. This is crucial for any enterprise and its stakeholders, including investors, shareholders, supervisory bodies, and potential buyers. Hence, digital security is a matter of decision making at the highest executive level.
The question remains: will anyone take the lead in implementing a top-down approach to direct a foundational framework, or will an incident such as the ransomware attack on the Colonial Pipeline have to happen before any action is taken?
The author anticipates a transformative shift toward stringent regulations mandating enterprises to disclose their cybersecurity, privacy, and data security efforts with unprecedented transparency in their annual or quarterly reports, mirroring the post-Enron and MCI WorldCom era's regulatory overhaul. Without the proactive approach of “test once, comply many”, and the use of in-control statements, enterprises and their regulatory bodies risk being overwhelmed by a deluge of rules and red tape, jeopardizing the global economic landscape.
Endnotes
1 Gdpr-info.eu, General Data Protection Regulation, European Union, https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=CELEX:32016R0679
2 European Commission, "Directive on Security of Network and Information Systems (NIS 2 Directive)," European Union, https://www.nis-2-directive.com/
3 European Commission, "The Digital Operational Resilience Act (DORA)," European Union, https://www.digital-operational-resilience-act.com/
4 Publications Office of the European Union, Regulation (EU) 2022/2554 of the European Parliament and of the Council, Official Journal of the European Union, European Union, 14 December 2022, https://eur-lex.europa.eu/eli/reg/2022/2554/oj
5 International Organization for Standardization/ International Electrotechnical Commission (ISO/IEC), ISO/IEC 27001:2022 Information security, cybersecurity and privacy protection, https://www.iso.org/standard/27001
6 Payment Card Industry Security Standards Council, "Payment Card Industry Data Security Standards," https://www.pcisecuritystandards.org/document_library/?document=pci_dss
7 BBP Media, “NIS2 Is Coming—And the Retail Industry Is Not Prepared,” 26 October 2022, https://www.bbpmedia.co.uk/business-insights/retail/nis2-is-coming-and-the-retail-industry-is-not-prepared.html CBS, "Businesses; Company Size and Legal Form," 2023, https://opendata.cbs.nl/#/CBS/nl/dataset/81588NED/table; Eurostat, "Sectoral Overview," 2021, https://ec.europa.eu/eurostat/cache/htmlpub/key_figures_on_european_business_2021/sectoral_overview.html; Kors, S.; “What Does NIS2 Mean for Dutch Organizations?," 7 December 2022, https://www.computable.nl/artikel/blogs/security/7444125/5260624/wat-betekent-nis2-voor-nederlandse-organisaties.html; PricewaterhouseCoopers, "DORA: Why Is It Relevant to You," https://www.pwc.com/gr/en/advisory/technology/dora-why-it-is-relevant-to-you.html
8 Easterly, ; Fanning, T.; “The Attack on Colonial Pipeline: What We’ve Learned & What We’ve Done Over the Past Two Years,” Cybersecurity and Infrastructure Security Agency, 7 May 2023, USA, https://www.cisa.gov/news-events/news/attack-colonial-pipeline-what-weve-learned-what-weve-done-over-past-two-years
9 NIST, NIST SP 800-207 Zero Trust Architecture, USA, 2020, https://csrc.nist.gov/pubs/sp/800/207/final
10 George, B.; “Fraudulent Accounting and the Downfall of WorldCom,” University of South Carolina (South Carolina, USA), 11 August 2021, https://sc.edu/about/offices_and_divisions/audit_and_advisory_services/about/news/2021/worldcom_scandal.php
11 Team, ; “Enron Scandal,” Corporate Finance Institute, https://corporatefinanceinstitute.com/resources/esg/enron-scandal/
12 107th US Congress, H. R. 3763 Sarbanes-Oxley Act of 2002, USA, 30 July 2002, https://www.congress.gov/bill/107th-congress/house-bill/3763/text.
13 Ibid.
14 Athavaley, ; Shepardson, D.; "Verizon, Yahoo Agree to Lowered $4.48 Billion Deal Following Cyber-Attacks," Reuters, 2017, https://www.reuters.com/article/us-yahoo-m-a-verizon-idUSKBN1601EK/
15 Ibid.
16 Holtaway, ; Rebibo, J.; “Pig in a Poke,” Ategra Capital Management, https://www.ategracapital.com/pig-in-a-poke/#:~:text=%E2%80%9CPig%20in%20a%20Poke%E2%80%9D%20dates,bag%20is%20%20the%20accompanying%20clich%C3%A9.
17 Fruhlinger, ; "Marriott Data Breach FAQ: How Did It Happen and What Was the Impact?," CSO Online, 12 February 2020, https://www.csoonline.com/article/567795/marriott-data-breach-faq-how-did-it-happen-and-what-was-the-impact.html
Yuri Bobbert
Is a professor at Antwerp Management School (Antwerp, Belgium) and chief executive officer (CEO) at Anove International. He is the former global head of IT security, risk, and compliance at NN Group NV, where he led the digital due diligence and integration process for the acquisition of DeltaLloyd, a €2.5 billion deal that created the largest life insurance company in the Netherlands.



