Clear modeling of a system is a fundamental step in its successful implementation. The same concept is also applicable to an enterprise risk management system (ERMS).
Risk is not a cyclical phenomenon. Over time, an organization’s risk profile evolves due to shifting threats, vulnerabilities, and objectives. Whether risk presents in a new form or one that has already been observed, a precise formula for predicting it has not yet been discovered.
Risk management, however, is a cyclical process. On a periodic basis, one must form an understanding of risk, i.e., sequentially identify it and evaluate its level, decide how to address it, implement the chosen option(s), monitor the progress of treatment, present the new risk state to management, and then do it all again.
Risk management tactics derive from the risk methodology1 adopted and adapted to an enterprise's ability to implement it effectively. No single methodology surpasses the others, yet a specific approach may prove most suitable depending on the organization’s circumstances and context. The sequence of phases to follow for each methodology is not always the same, even if it is merely a matter of taxonomy (i.e., different words are used to express the same meaning. For example, acceptance vs. retention, mitigation vs. reduction, or treatment vs. prevention could all be used to represent the same idea).
Risk management is first a system, and therefore is composed of a series of processes that interact with each other, either in sequence by using the output of a completed phase as input for the following phase, or in a transversal manner by affecting multiple phases together. To guarantee coherence to the sequence, it is necessary to define the tasks of each individual phase simply and precisely. Furthermore, the term "system" implies the definition of specific organizational roles and responsibilities to support and control the identified tasks.
Risk Definition
To understand a system, start with its components, which in the case of risk are obtained from its definition. Among the various definitions of risk, some simply provide the basic concepts of what it is, how it is formed, and what metrics should be considered. The International Organization for Standardization (ISO) and US National Institute of Standards and Technology (NIST) definitions of a risk event may be used to frame the discussion of risk management:
- Effect of uncertainty on objectives2
- Combination of the probability of an event and its consequence3
- Threats, vulnerabilities, likelihoods, and impacts are used to determine risk4
The first definition is the most widespread currently. It considers business objectives as the compass of the risk management system. From this principle, it follows that safeguarding critical assets—while managing uncertainty—is essential for achieving the objectives. In other words, the objectives identify the set of organizational assets, the value of which will be the point of reference in the impact assessment.
The second definition focuses on the elements that constitute risk. The method for defining the level of risk must at least consider the possibility that the risk event will occur and that there will be measurable consequences on the achievement of the objectives. The consequences being measured are those referring to organizational assets, as established by the first definition of risk.
The third definition is not as straightforward but is derived from the first two and highlights the critical factors of the risk event. It focuses on the threats that cause the risk, the vulnerabilities that highlight control weaknesses, the probabilities that measure the possibility of the event occurring, and the impact that represents the extent of the consequences.
The set of critical risk factors together with the organizational assets define which elements are to be considered in terms of measurement or evaluation to determine the risk level of an event.
Enterprise Risk Management System Depiction
By analyzing various risk methodologies, selecting the most characteristic phases of each methodology, and eliminating redundancies and inconsistencies, a linear sequence of activities can be obtained. These activities should be listed clearly and without ambiguity to facilitate enforcement. By arranging them in an orderly manner through a graphical representation, an overall view is formed that depicts the scheme of the enterprise risk management system, including its phases and main relationships. Figure 1 depicts the sequence of phases and highlights the operational tasks in risk management. The innermost cycle of the ERMS representation is the sequence of operational phases while the outermost cycle, composed of macro phases, is of an organizational nature to ensure the right result of the decision making, evaluation, and operational flows. The figure also illustrates the essential processes that span the entire risk management system, such as communication, culture, and monitoring.
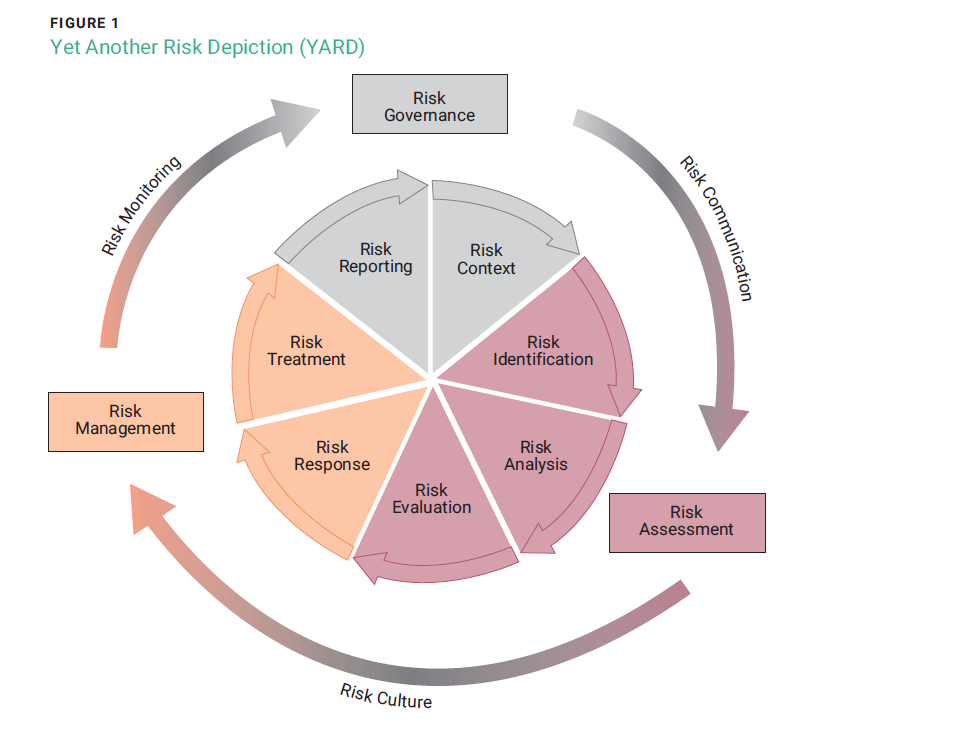
Risk Governance
Risk governance represents a structured process for defining and controlling the entire set of activities relating to the risk management system in order to ensure the achievement of results senior management desires. The main tasks of this process are to supervise each activity to guarantee the operational effectiveness of the system and to assist the risk owner in making methodological or operational decisions. Risk governance must demonstrate leadership and a commitment to maintaining an effective risk management system because this also influences the risk culture in the organization.
Risk Context
The risk context phase is the logical starting point of the cycle sequence and consists of senior management defining all the elements necessary to govern the risk management cycle. As a consequence of the results of the risk reporting phase, senior management may make decisions about whether to review business objectives, make policy changes, vary risk tolerance/appetite, review risk methodology, or make organizational changes to the ERMS. At the same time, the risk scope could also be reconsidered based on any changes to the mission or vision of the enterprise. Not only that, but any change in the business objectives could also lead to a change in the set of organizational assets to be considered when identifying risk.
Risk Communication
Risk communication is a process that cuts across all phases by definition. Risk communication carries out two primary actions: the dissemination of the organizational rules established to inform the ERMS operating model and the distribution of the results of monitoring and assessments to all stakeholders. The process must be adequately structured to ensure the flow of information with continuity and timeliness, including by describing it in the operating procedures. Particular attention is paid to the effectiveness of communicating business objectives and risk appetite from the risk context phase to the following phase of identification of the risk event.
Risk Assessment
The risk assessment is a macro phase that takes place under the authority of the risk practitioner. It consists of three phases and begins with an analysis of the risk context to understand and define the risk scenario. The risk assessment continues with the measurement of the two parameters of probability and impact, necessary for the third phase of assessing the risk level for the organization.
Risk Identification
Risk identification is the first phase of the risk assessment process and involves the creation of risk scenarios. It requires accuracy in data collection, but also an effort of imagination to identify all the elements of the scenario. The fundamental elements for describing risk are the organization’s assets, threats, vulnerabilities, and controls. The organizational structure (i.e., roles and responsibilities) is also useful for reconstructing interactions between various elements. Every relationship between an asset and the threat or vulnerability by which it is targeted forms a risk scenario.
Creating a list of organizational assets consists of two steps. First, the most critical assets are identified during the risk context phase as a direct derivation from the business objectives. Next, any additional assets that are critical to the functionality of the assets selected during the risk context phase are identified.
To assess threats and vulnerabilities, a Strengths, Weaknesses, Opportunities, and Threats (SWOT) analysis5 can be performed. This technique is useful for assessing these four aspects of the enterprise. Vulnerabilities are control weaknesses and are always an internal factor. Threats are often derived from existing taxonomies in publicly available libraries and then evaluated in the specific risk context.
After all the elements useful for identifying risk are collected, it is necessary to understand how to arrange the elements together according to their potential impact on business objectives. To represent the risk scenario, it is appropriate to use standard methods such as the unified modeling language (UML)6, a general-purpose visual modeling language intended to provide an easy way to visualize the design of a system. The use of standards greatly facilitates communication between teams, particularly when they are external to the organization.
Risk Analysis
Risk analysis is the second phase of the risk assessment process. The input is the risk scenario which must be interpreted and evaluated according to two directions, namely, the estimate of the possibility of occurrence of the risk event and the determination of the impact on business objectives.
To evaluate the probability of risk occurrence, if reliable numerical sequences are not available, qualitative assessments can be used. This can be achieved by simulating realistic scenarios consisting of the interaction of assets, threats, and maturity of the related controls in the scenario, and then requesting a context assessment from a control owner. For the impact assessment, in the absence of more reliable assessments, it is possible to map the asset/threat/maturity control combinations and search for them in the business impact analysis (BIA).7 This document is drawn up by the managers of the business functions, who often coincide with the risk owners. The output of the BIA is the estimated expected impact.
Risk Evaluation
Risk evaluation is the third phase of the risk assessment process and is typically the least demanding phase in terms of effort. Generally, it consists of a formula or matrix for calculating the risk level, which is illustrated by the second definition of risk. All options for how to mitigate the risk derive from this risk assessment, and this makes two factors particularly critical:
- Choice of risk methodology, because it must be adequately matched to the actual ability of the enterprise to collect and interpret data
- Adjustment of risk appetite, which should be the driving force behind the calculation used during risk evaluation, so that it is always aligned with the severity of the risk to the organization
The numerical precision of the risk calculation method is not guaranteed because the risk level is an estimate of a future event based on an already approximated scenario. Rather, there is more value in viewing the results of the cyclical sequence of assessments because it is useful for understanding the variation in the effectiveness of controls over time. The last step of this phase is the arrangement of risk events based on intervention priority.
Risk Culture
Risk culture is the set of shared values and beliefs that govern attitudes toward risk taking and ethics. It determines how risk or losses are reported and openly discussed. Improving risk culture is a process that cuts across all organizational functions and is crucial to the success of the risk management system. Training is a useful tool for spreading culture, but this action is only as effective as management is aware of its importance.
Although risk culture concerns every business activity, its influence is most evident in the risk assessment phase and the consequent decision-making phase, wherein the corrective actions to be undertaken are determined. Risk culture derives from management's sensitivity to and conviction on the topic of risk, with a theoretical imprint perceivable in internal control policies and an operational one made evident by the risk assessment process and consequent responses.
Risk Management
Risk management is a macro phase that represents the domain of operations that are the responsibility of the risk owners as decision makers and the control owners as implementers of risk containment actions. This process encompasses choosing the response(s), the design phase of the risk treatment plan, its complete implementation, and the control of achievement of the planned residual risk level. Its input is risk assessment and its output is control monitoring data.
Risk Response
In this phase, the risk owner is responsible for transforming the risk assessment(s) into an action plan that reduces risk to a level deemed acceptable by the organization. The document that constitutes the outcome of this phase is the risk treatment plan (RTP), which is created by choosing one of four possible options to respond to the risk:
- Risk acceptance means assuming the risk entirely without any further action. The risk owner knowingly assumes the risk in the case of an acceptable level or when no other alternative is possible.
- Risk mitigation involves acting to reduce the level of risk. The risk owner must define actions (called controls) to reduce the risk’s probability, impact, or both.
- Risk transfer/sharing requires totally or partially transferring (sharing) the impact of the risk to a third party. The responsibility remains with the risk owner.
- Risk avoidance means changing the conditions that lead to the risk itself, i.e., acting on the risk scenario; for example, by changing the time base for achieving objectives or defining a different target.
Risk owners' decisions are justified by a cost/benefit analysis and conclude with the issuing of the RTP, which contains two risk assessments: the current risk and the residual risk (i.e., the level that is expected to be obtained after all mitigation controls have been implemented). The cost/benefit analysis could be conducted by a control owner in the case of mitigation, by a senior manager for the transfer, or by a risk practitioner to review the risk scenario.
Risk Treatment
In this phase, the control owner is responsible for implementing all the controls envisaged by the RTP and evaluating their effectiveness with respect to the planned risk level. The design/development phase extends beyond guaranteeing performance; it also involves defining monitoring methods to continuously verify that controls align with the plan’s requirements.
The implementation phase must take place by adopting design and development standards appropriate for the criticality of the control. The monitoring phase and the consequent delivery of the results must respect the expectations and understanding of the appropriate stakeholders (e.g., definition of the frequency of the control, visual representation of the indicators, depth of the control, etc.).
Risk Monitoring
Risk monitoring involves all processes within the organization as it affects every control defined in the RTP and is the responsibility of the control owner. It is designed with the control to which it refers during the risk treatment phase. Risk monitoring occurs continuously throughout the life cycle of the control itself to signal alignment with the specifications of the risk treatment plan over time. Monitoring outcomes are mainly aimed at the risk reporting phase but they also feed the assessment of vulnerabilities within the risk scenario.
The collection of data on the control activity provides information about how well the control is performing, which may be broken down into several categories of indicators:
- A key control indicator (KCI) provides a measure of control effectiveness from a risk perspective
- A key risk indicator (KRI) provides an early signal of the increased level of exposure to risk.
- A key performance indicator (KPI) provides a quantifiable measure of performance over time for a specific objective.
Different stakeholders should receive different indicators. For example, the risk professional must understand the effectiveness of the risk control; the control owner should be aware of the control performance; and the user should be informed of both the performance of the control and the occurrence of a risk factor.
Risk Reporting
The risk reporting phase is not a mere presentation of data. First, it is a matter of interpreting the results gathered from monitoring to highlight all the situations where there is a risk of misalignment with respect to risk appetite. Then, the risk professional aggregates the risk factors that have greater exposure to organizational objectives. Next, the best form of data representation is selected to get the attention of senior management. Finally, suggestions for adapting the risk treatment plan are clarified.
The quality of the presentation to senior management must be high because it is the moment of synthesis of all the work done and is what prompts a reaction to the risk. No less important is equipping operational staff with the necessary details about the status of risk containment actions to help them understand vulnerabilities and take appropriate improvement actions.
Conclusion
Addressing the representation of the ERMS with clarity and simplicity means obtaining easy-to-use modeling that encourages less complexity and more effective processes. It is not necessary to wait until all processes are well-defined to start acting. The cyclical nature of the risk management system allows solutions to be refined at each cycle, improving and enabling the operational process to be activated quickly and effectively.
Risk is the measure of the uncertainty of obtaining the planned result—and this measure is never zero. Lacking absolute certainty of the final result of any process, we must place our trust in risk management systems. A method that can be managed competently, quickly, and with attention paid to costs must be adopted to govern risk effectively. The expected benefit can be obtained only with a systematic application of the risk guidelines established here (benefit, in terms of business, means value creation).
Endnotes
1 ISACA®, Certified in Risk and Information Systems Control® (CRISC®) Official Review Manual, 7th Edition Revised, 2021, https://www.isaca.org/resources; International Organization for Standardization (ISO), ISO 31000 Risk Management, 2018, https://www.iso.org/standard/65694.html; National Institute of Standards and Technology, SP800-37r2 Risk Management Framework for Information Systems and Organizations, USA, 2018, https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-37r2.pdf; National Institute of Standards and Technology, SP800-30r1 Guide for Conducting Risk Assessments, USA, 2012, https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-30r1.pdf
2 ISO, ISO 31073 Risk Management — Vocabulary, 2022, https://www.iso.org/standard/79637.html
3 ISO, ISO/IEC Guide 73:2002 Risk Management— Vocabulary, 2002, https://www.iso.org/standard/44651.html
4 National Institute of Standards and Technology, Cybersecurity Framework CSF 2.0 Reference Tool, Subcategory ID.RA-05, USA, https://csrc.nist.gov/Projects/cybersecurity-framework/Filters#/csf/filters
5 Friend, G.; Guide to Business Planning, Bloomberg Press, USA, 2009
6 Object Management Group, Unified Modeling Language, UML2, https://www.uml.org
7 ISO, ISO/TS 22317:2021 Security and Resilience— Business Continuity Management Systems — Guidelines for Business Impact Analysis, 2021, https://www.iso.org/standard/79000.html
Luigi Sbriz | CISM, CRISC, CDPSE, ISO/IEC 27001:2022 LA, ITIL V4, NIST CSF, UNI 11697:2017 DPO
Is a lead auditor, trainer, and senior consultant on risk management, cybersecurity, and privacy issues and has been the risk monitoring manager at a multinational automotive company for more than seven years. Previously, he was head of ICT’s operations and resources in the APAC Region (China, Japan, and Malaysia) and, before that, was the worldwide information security officer for more than seven years. He developed an original methodology for internal risk monitoring, merging an operational risk analysis with a consequent risk assessment driven by the maturity level of the controls. He also designed a cyber monitoring tool based on OSINT and an integrated system involving risk monitoring, maturity model, and internal audit. He was a consultant for business intelligence systems for several years. He can be contacted on LinkedIn (https://www.linkedin.com/in/luigisbriz) or http://sbriz.tel.



