In today’s digital era, compliance with the International Organization for Standardization/ International Electrotechnical Commission (ISO/IEC) standard 27001 acts as an enterprise’s security guard. Compliance provides a robust shield for digital assets, ensuring a proactive and comprehensive approach to cybersecurity. Embracing the standards contained in ISO/IEC 27001 not only safeguards sensitive information, but also establishes trust with clients and stakeholders in an increasingly interconnected world.
The ISO/IEC 27001 standard provides enterprises of any size and from all sectors with guidance for establishing, implementing, maintaining, and continually improving an information security management system (ISMS).1 Conformity with ISO/IEC 27001 means that an enterprise has adopted a system to manage risk related to the security of the data it owns or handles and that the system respects all the best practices and principles enshrined in this international standard.
The revised standard, ISO/IEC 27001:2022, was published on 25 October 2022 and includes a number of technical corrections and a fully revised Annex A with control measures. Certifications based on the previous version, ISO/IEC 27001:2013, will expire or be withdrawn after the three-year transition period, which ends on 31 October 2025. Therefore, transitioning to the new standard must begin soon if it has not already begun. The transition is a strategic process that requires careful planning and execution.
Although the transition process is termed a 90- day challenge here, there is no strict time limit for a full transition. The duration may vary based on elements such as management commitment, scope, organizational size, number of locations, budget considerations, and other relevant factors.
Before undertaking this transition, it is important to understand the standard. There are three main parts of the ISO/IEC 27001 framework:
- Clauses 4 through 10 (Context, Leadership, Planning, Support, Operation, Performance, and Improvement) lay out the elements of an information security management system (ISMS) manual. Excluding any of these requirements is unacceptable if an enterprise wishes to claim conformity with ISO/IEC 27001. The ISMS aligns with the plan, do, check, act (PDCA) model: planning and establishment (plan), implementation and operation (do), monitoring and review (check), and maintenance and improvement (act).2 It encompasses aspects such as organizational context, leadership, support, operation, performance evaluation, and continual enhancement.
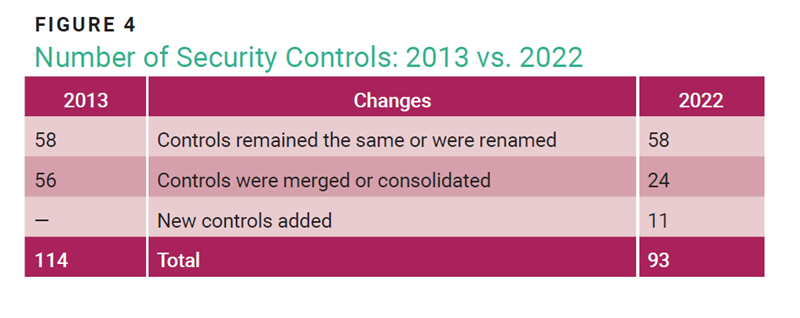
- Annex A, now renamed Information Security Controls, is divided into four sections: Organizational, People, Physical, and Technological controls. The 2022 version has fewer controls (93) than the 2013 version (114).
- The statement of applicability (SOA) is a valuable tool that allows the adaptation and customization of security controls based on the specific needs, risk factors, and circumstances of the enterprise. The SOA ensures a tailored and effective ISMS.
Figure 1 provides a detailed 90-day (or 18-workweek) timeline and action plan for an ISO/IEC 27001 transition.
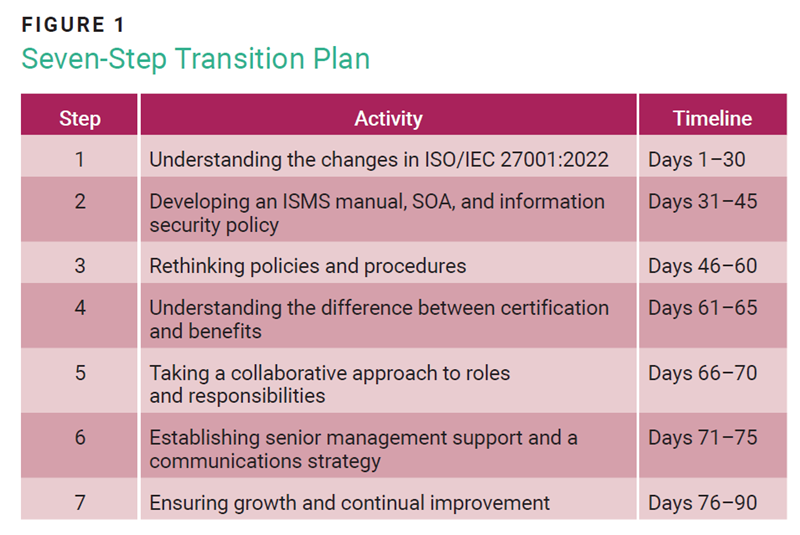
The time allocated for each activity is dependent on factors such as the size and complexity of the enterprise, the current state of its ISMS, and the level of familiarity with ISO/IEC 27001 requirements.
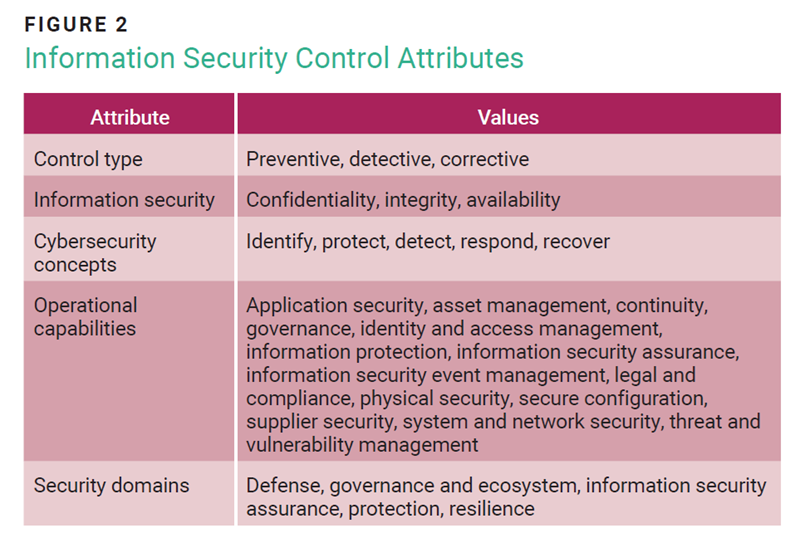
ISO/IEC standard 270023 outlines the standard’s purpose, control definitions, and detailed guidance steps. The revised standard elaborates on each information security control, based on five attributes: control type, information security, cybersecurity concepts, operational capabilities, and security domains (figure 2).
Step 1: Understanding the Changes (Days 1–30)
It is critical to understand the key changes in the new standard and how they can benefit an enterprise. Awareness and understanding of the modifications in the latest version lay a solid foundation for subsequent steps.
Step 1.1: Conduct a Kickoff and Awareness Session (Week 1)
The lead implementation team must have a copy of the official ISO/IEC 27001:2022 standard. To make awareness sessions interesting and interactive, it is helpful to use everyday scenarios to explain important points. For example, when discussing data classification, one might say:
Think of digital assets like precious personal belongings. One would not casually display credentials or financial documents on the living room table. In the cyberworld, data classification is like putting these valuables in a secure vault. It involves identifying and safeguarding the enterprise’s crown jewels, ensuring that sensitive information is not left exposed. Treat digital assets with the same care as physical ones—classify and protect them wisely.
Enterprises commonly emphasize the following directives to their staff:
- Exercise caution when clicking on links in external emails.
- Do not leave confidential documents unattended on desktops.
- Lock the computer screen when stepping away from workstations.
- Properly dispose of confidential documents by shredding.
These simple yet crucial practices contribute significantly to fostering a secure and vigilant workplace.
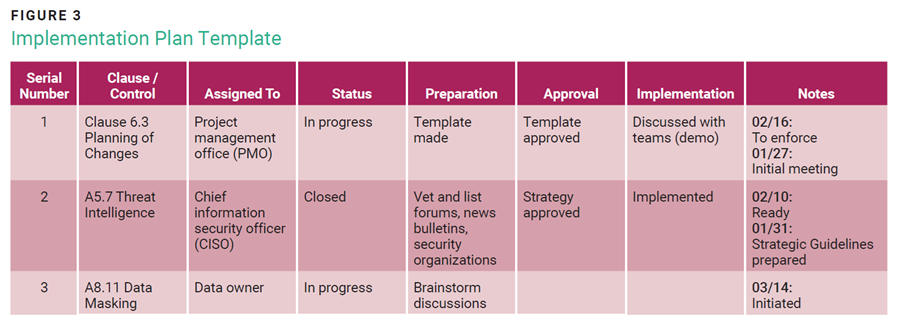
The implementation plan template in figure 3 can be used to coordinate and track activities assigned to stakeholders.
Step 1.2: Identify Major Changes (Week 2)
The 2022 revision made the following major changes to the 2013 version of ISO/IEC 27001:
- The standard is now titled Information Security, Cybersecurity and Privacy Protection, changed from Information Technology—Security Techniques.
- Clauses 4 to 10 underwent major updates encompassing information security objectives, planning of changes, and operational planning and control.
- The number of controls in Annex A decreased from 114 to 93 (figure 4). The 93 controls were reorganized into four sections: organizational (37), people (8), physical (14), and technological (34). The 11 new controls cover the following:
- Organizational controls—Threat intelligence, information security for cloud services, information and communication technology (ICT) readiness for business continuity4
- People controls – Emphasize the human factor in information security (the controls in this section remain unchanged from the previous version)
- Physical controls—Physical security monitoring
- Technological controls—Configuration management, information deletion, data masking, data leakage prevention, monitoring activities, web filtering, secure coding5
Leaders must identify the key changes relevant to their enterprise and align organizational activities with the revised requirements.
Step 1.3: Conduct a Gap Assessment (Weeks 3–4)
There are two major steps in a gap assessment:
- Assess current practices—Become familiar with ISO/IEC 27001 requirements. Involve key personnel in the assessment.
- Identify gaps and misalignments—Categorize gaps by effort, impact, and cost.
The possibilities include policy gaps (lack of a formal information security policy), access control gaps (inconsistent user access controls and permissions), risk assessment gaps (irregular or incomplete risk assessments), documentation gaps (inadequate documentation of security procedures), incident response gaps (lack of a formal incident response plan), and training gaps (insufficient information security training for employees). Prioritize the gaps based on severity and risk and determine dependencies and critical areas for immediate attention.
A phased approach is recommended, breaking the process into manageable phases for clarity:
- Clearly outline milestones for each phase to track progress.
- Communicate urgency and consequences; clarify open questions.
- Emphasize holistic and interconnected steps; stress ongoing commitment and adaptation.
An action plan should define tasks, responsibilities, and timelines and ensure accessibility for all stakeholders. This may include:
- Clearly defining the specific tasks required for each phase
- Ensuring that tasks are granular enough for easy execution and monitoring
- Assigning responsibilities to individuals or teams
- Clarifying roles and expectations for accountability
- Setting realistic timelines for task completion
- Considering dependencies and resource availability
- Building flexibility into the plan for unforeseen challenges
- Regularly reassessing and adapting the plan based on progress and changing circumstances
To monitor progress, a tracking mechanism can be implemented, and objective key performance indicators (KPIs) established. The following KPIs provide a snapshot of critical areas, allowing enterprises to track their progress:
- Percentage of employees who have acknowledged the information security policy
- Number of unauthorized access attempts detected and mitigated using Annex A controls or safeguards from another security framework
- Percentage reduction in high-risk vulnerabilities identified through risk assessments
- Average time to detect and respond to security incidents
- Percentage increase in the completion of security awareness training
Step 2: Developing an ISMS Manual, SOA, and Information Security Policy (Days 31–45)
Developing the ISMS manual and SOA early in the process provides a foundation for subsequent steps. This ensures that the enterprise has a clear understanding of its information security context and a documented system in place to manage it.
Step 2.1: Create an ISMS Manual (Week 5)
The ISMS manual provides a comprehensive view of the ISMS structure and processes (i.e., governance). It focuses on management and elaborates on the requirements covered by clauses 4 to 10 of ISO/IEC 27001:2022. The table of contents of an ISMS manual may look something like this:
- Introduction
- Context of the organization (internal and external issues, interested parties, ISMS scope, ISMS objectives)
- Leadership (information security policy, roles, and responsibilities)
- Planning (information security objectives, risk factors and opportunities, risk management processes, SOA, planning for changes)
- Support (resources, competence, awareness, communication, documentation)
- Operations (planning and control, risk assessment and risk treatment results)
- Performance evaluation (monitor and control, internal audit, management reviews, measures, and metrics)
- Improvements (continual improvement, nonconformance, corrective action)
Alignment with ISO/IEC 27001 requires implementing clauses 4 through 10, including the various processes outlined above.
Step 2.2: Draft a Statement of Applicability (Weeks 6–7)
An external consultant should never be the one to formalize the enterprise’s SOA. It is unlikely that they will fully understand the organization’s internal context, nuances, and security requirements. There is also a risk of lack of ownership. Each security control should be discussed internally to create the SOA charter.6 The SOA is the main link between risk assessment and risk treatment.
An SOA template should be created that accounts for all Annex A controls (figure 5). Columns E–H must be filled in by representatives of the enterprise.
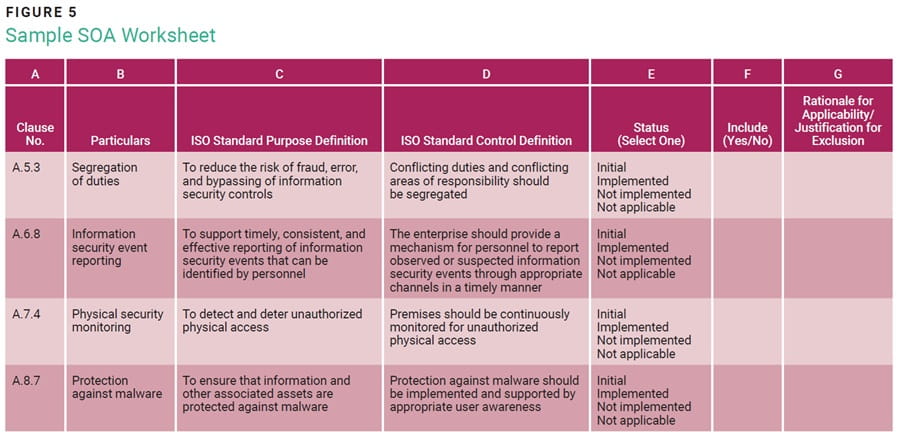
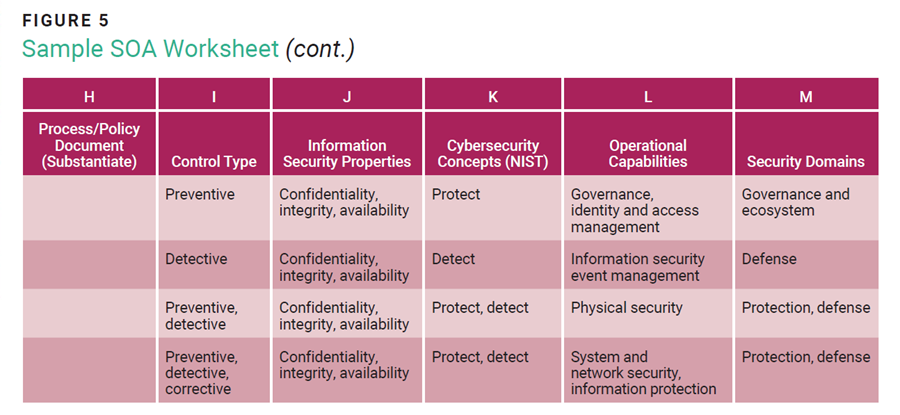
The purpose and control definitions contained in the SOA must be understood by all stakeholders. Each entry in the SOA determines the current status of the control (column E: initial or discussion stage, implemented, not implemented, not applicable), whether it should be included (column F: yes or no), and the rationale for inclusion or justification for exclusion (column G). For example:
- Justification for the exclusion of remote work (clause A.6.7)—To maintain a secure financial environment, remote work is prohibited. This decision, aligned with industry best practices and regulations, enhances the enterprise’s cybersecurity stance, ensuring data security, compliance, and risk mitigation. Limiting operations to controlled environments strengthens the defense against cyberthreats, safeguarding customer information and financial transactions.
- Rationale for the inclusion of data masking (clause A.8.11)—Data masking reinforces the enterprise’s dedication to customer data confidentiality by enhancing cybersecurity measures. It plays a crucial role in fortifying data security by preventing unauthorized access to sensitive information.
Inclusion of a security control should lead to a risk assessment process that provides risk treatment measures and documentation by way of policies, procedures, checklists, or guidelines.
The SOA is used to identify and implement relevant controls effectively. It should be reviewed by management, security experts, and relevant stakeholders to ensure accuracy. The SOA requires ongoing review and updates to reflect changes in the enterprise’s security posture and to address evolving threats.
Step 2.3: Establish or Review the Information Security Policy (Weeks 7–10)
The information security policy, which is part of the ISMS, specifies the enterprise’s commitment to information security principles and compliance. It may serve as the overarching document for various policies, procedures, guidelines, and checklists, including but not limited to the following:
- Access control
- Acceptable use
- Asset management
- Backup and recovery
- Clear desk and clear screen
- Cryptography and key management
- Email and communications security
- Information classification and handling
- Information security incident management
- Information transfer or data exchange
- Malware protection
- Management of technical vulnerabilities
- Mobile devices and bring-your-own-device (BYOD)
- Network security
- Privacy protection
- Risk management strategy
- Secure configuration and handling of user endpoint devices
- Secure development
- Supplier relationships
These information security policies serve as the cornerstone of information security governance and compliance, articulating the enterprise’s unwavering commitment to information security principles and compliance.
Step 3: Rethinking Policies and Procedures (Days 46–60)
This step lays the groundwork for a successful transition in the process from understanding to planning by revisiting existing policies and procedures.
Establishing effective security measures begins with developing policies aligned with the organization’s nature, business context, and cultural nuances. The policies should be relevant to the majority of employees, directly mirroring operational activities. The implementation of corresponding processes and procedures ensures the effective execution of these policies, disseminating them across the organization.
A thoughtful review and adaptation of existing documentation may take the following approach.
Step 3.1: Align Policies with the New Requirements (Week 11)
- Review and adapt—Take a close look at what requirements are already in place. Are existing policies and procedures up to the tasks of addressing new challenges, complying with regulations, and supporting Agile development?
- Identify gaps—No system is perfect. Identify areas for improvement and gather everyone’s input.
- Involve stakeholders—Collaboration is key. Everyone’s perspective matters.
- Have an exceptions process—Sometimes, flexibility is required. Consider adding a process for making exceptions to policies.
- Connect policies to standards—Each policy should have a clear link to the standards it addresses.
The information security policy cannot stand alone. It should be part of the enterprise’s risk management process and approved by the board of directors.
Step 3.2: Adjust the Risk Analysis and Treatment Plan (Week 12)
Modifying the risk analysis and treatment plan to align with the new requirements of ISO/IEC 27001:2022 will help identify and prioritize the threats to information security and lead to the development of appropriate controls.
Relevant actions may include:
- Determine asset value—A straightforward method of determining asset value is to assign values (1 through 5) for confidentiality, integrity, and availability. To do this, it is crucial to understand the risk landscape. A simplified overview is as follows:
- Identify threats—Think of threats as potential events or circumstances that could harm assets. They are the dangers lurking in the enterprise’s digital space.
- Assess vulnerabilities—Vulnerabilities are weaknesses or gaps in the system that could be exploited. Identifying these vulnerabilities is akin to finding the weak links in the enterprise’s digital armor.
- Calculate risk value—The risk value is a numeric representation of the potential impact of a threat that exploits a vulnerability. It is a way of quantifying the level of risk facing an enterprise.
- Take advantage of Annex A controls—ISO/IEC 27001 provides a treasure trove of controls that can be used to counteract threats and vulnerabilities. They are specific measures designed to reduce the risk value.
- Leverage other standards—ISO/IEC 27001 does not operate in isolation. It complements other standards and frameworks. For instance, if a control in ISO/IEC 27001 is not specific enough, another framework or standard can be referenced to help fill in the gaps, such as the US National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF), Center for Internet Security (CIS) Controls, or NIST Special Publication (SP) 800-53.
- Use compensating controls—Sometimes, a direct solution is not feasible. This is where compensating controls come into play. They are alternative measures that address a risk when the primary control is not applicable.
This step is about strengthening defenses by identifying potential threats, shoring up vulnerabilities, and deploying the right controls from Annex A and beyond. It is a strategic move in the digital chess game—anticipating moves, fortifying positions, and ensuring the digital kingdom’s security.
Step 4: Understanding the Difference Between Certification and Benefits (Days 61–65; Week 13)
This phase is short but thought-provoking. ISO/IEC 27001 certification is not merely a badge. Obtaining it is a strategic move that highlights strategic advantages and instills a broader perspective into the organization’s leadership, employees, and stakeholders.
Large or small, enterprises seeking ISO/IEC 27001 certification are intentional about taking the time to fully audit their security postures and showing internal and external stakeholders that physical and digital security are priorities.7
Step 5: Taking a Collaborative Approach to Roles and Responsibilities (Days 66–70; Week 14)
Establishing clear roles and responsibilities is essential and contributes to a collaborative approach. To ensure ongoing collaboration and compliance, the following steps can be taken:
- Perform internal audits—Internal audits are essential for transitioning from existing processes to new ones. Perform audits in alignment with the updated ISO/IEC 27001 standard. Emphasize that it goes beyond mere compliance; It involves actively monitoring and enhancing the ISMS.
- Form a steering committee—This committee should have representatives from each part of the enterprise. This is not only a group—it is a team with clear roles and responsibilities.
- Institute management review—Management review can identify areas for improvement and ensure that information security controls are aligned with business objectives.
- Apply corrective actions from internal audits and reviews to ensure ISO/IEC 27001:2022 compliance and enhance the effectiveness of information security controls.
Step 6: Establishing Senior Management Support and a Communications Strategy (Days 71–75; Week 15)
When presenting changes to senior management, it is critical to emphasize the benefits to the enterprise and the importance of their support in the process. Actively seek commitment and support from leaders to secure their endorsement of proposed changes. Then develop a comprehensive plan for effectively communicating these changes throughout the various organizational levels.
Step 7: Ensuring Growth and Continual Improvement (Days 76–90; Weeks 16–18)
In the pursuit of continual improvement, it is imperative to have an unwavering commitment to ISO/IEC 27001:2022 during the growth phase. This not only ensures the establishment of a robust security program, but also fosters effective risk management and sustained compliance over time.
When venturing into the realm of strategic planning, it is important to look beyond the immediate transition. Strategically chart a long-term course that can withstand the test of time and evolving challenges.
Conclusion
Embedded in this journey is the crucial step of regular reviews and updates. Compliance is not a one-time endeavor; it is an ongoing expedition. The pursuit of efficiency through synergies requires flexibility and periodic reassessment to adapt to the changing landscape, reinforcing the idea that compliance is an ongoing and dynamic process. But this transformative journey goes beyond mere compliance; It is dedicated to forging a resilient and secure digital future.
Endnotes
1 International Organization for Standardization, “ISO 27001:2022—Information Security, Cybersecurity and Privacy Protection: Information Security Management Systems,” 2022, https://www.iso.org/standard/27001
2 Global Compliance Certification, “ISO 27001 and the PDCA Cycle: A Roadmap to Information Security,” https://gccertification.com/iso-27001-and-the-pdca-cycle-a-roadmap-to-information-security/
3 International Organization for Standardization, “ISO/IEC 27002:2022—Information Security, Cybersecurity and Privacy Protection: Information Security Controls,” https://www.iso.org/standard/75652.html
4 Ahmed, H.S.A; “A Guide to the Updated ISO/IEC 27002:2022 Standard, Part 1,” ISACA®, 15 February 2023, https://www.isaca.org/resources/news-and-trends/newsletters/atisaca/2023/volume-7/a-guide-to-the-updated-iso-iec-27002-2022-standard-part-1
5 Ahmed, H.S.A.; “A Guide to the Updated ISO/IEC 27002:2022 Standard, Part 2,” ISACA, 2023, https://www.isaca.org/resources/news-and-trends/newsletters/atisaca/2023/volume-12/a-guide-to-the-updated-iso-iec-27002-2022-standard-part-2
6 Sundaram, J.; “The Benefits of the Statement of Applicability in ISMS Projects,” ISACA Journal, volume 3, 2017, https://www.isaca.org/archives
7 Huntington, C.; “What Do the ISO 27001 Updates Mean for Your Business,” ISACA, 23 November 2022, https://www.isaca.org/resources/news-and-trends/isaca-now-blog/2022/what-do-the-iso-27001-updates-mean-for-your-business
Jayakumar Sundaram | CISA, ISO 27001:2013 LA/LI, CC
Is a principal cybersecurity consultant at SVAM International Inc. He has been working in the fields of information security, cybersecurity Before undertaking this transition, it is important to understand the standard. There are three main parts of the ISO/IEC 27001 framework: and governance, and risk and compliance practices for more than 12 years and has three decades of experience in information systems and IT delivery management. Sundaram can be contacted on LinkedIn at https://www.linkedin.com/in/jaysundaram.


