In this digital age of interconnectedness, cybersecurity serves as a shield to protect the online world. Yet organizations continue to face cyberattacks, despite forming dedicated security functions. This raises questions about what might be lacking in current strategies. Although cybersecurity is a topic of discussion in many boardrooms, achieving complete security remains elusive.
Historically, the sentiment has been that cybersecurity cannot function in isolation; it needs to be integrated with overall business and technology strategies. To that end, chief information security officers (CISOs) and business units have developed specialized functions such as identity and access management (IAM), threat intelligence, security monitoring, data protection/privacy, application security, third-party risk management, and more. Employees within these functions excel in their specific areas but often operate with a "not-my-job" mentality when it comes to addressing issues outside of their defined roles. This situation circles back to the original problem: Functions within cybersecurity cannot afford to operate in silos.1
The complexity of cyberthreats often mirrors the fragmentation within a cybersecurity function. As threats evolve and diversify, cybersecurity functions cannot operate effectively in silos.To effectively protect an organization, all cybersecurity functions must work together in a unified and collaborative manner. A siloed approach can result in undetected cyberthreats, thus increasing the number of successful cyberattacks.2 Cybersecurity teams must bridge these divides and adopt more holistic approaches to safeguard their organizations. Yet, the complexity of cyberthreats often mirrors the fragmentation within a cybersecurity function. As threats evolve and diversify, cybersecurity functions cannot operate effectively in silos. The need for a unified and cohesive approach across various cybersecurity functions has become increasingly apparent.
The Current Landscape: Functions in Isolation
Typically, a standard organization adopts one of several CISO operating models, with its choice influenced by factors such as organizational size, industry, risk tolerance, regulatory obligations, and existing organizational structure. The primary objectives are to secure effective governance and proficient risk management and to establish a resilient cybersecurity framework that aligns with the organization's objectives.
Types of CISO operating models include:
- Centralized—A single CISO authority oversees the entire organization’s cybersecurity.
- Decentralized—Multiple CISOs serve individual business units, tailoring cybersecurity strategies to unit-specific needs.
- Hybrid—A combination of centralized and decentralized structures adapts to diverse organizational needs.
- Matrix—CISOs with reporting lines across departments align security initiatives with departmental goals.
- Outsourced/third-party—External CISO services provide flexibility and specialized expertise.
- Virtual or part-time CISO—A CISO as a service offers strategic guidance without a full-time commitment.
Each model presents distinct benefits, but all share two common drawbacks:
- The potential for fragmented operations
- A deficiency in unified functions for ensuring a secure future
Challenges Due to Cybersecurity’s Siloed Functions
It is surprisingly common for cybersecurity team members outside the vulnerability management/application security team(s) to lack awareness of the full array of applications within the organization and their risk profiles.
This includes not being privy to the startling number of laptops that go missing, remaining uninformed about the alarming rate of detected malware attacks, and being oblivious to the critical interventions executed by the data loss prevention team to thwart looming threats of data exfiltration.
This includes not being privy to the startling number of laptops that go missing, remaining uninformed about the alarming rate of detected malware attacks, and being oblivious to the critical interventions executed by the data loss prevention team to thwart looming threats of data exfiltration.
Oftentimes not all members of the cybersecurity unit are familiar with or have even seen the organization's comprehensive risk framework. This lack of universal understanding within the team highlights a significant gap in grasping the full spectrum of the organization's risk strategy.
In many organizations, there is a surprising disconnect wherein the security information and event management (SIEM) system does not relay information about security incidents (e.g., potential password attempts, malware, malicious connections, phishing attacks, etc.) across other cybersecurity teams. If communicated widely with other security functions, they can help thwart attacks at the people, process, and technology levels, which benefits the SIEM team by reducing time and effort.
Compliance teams working in silos may not fully understand the operational challenges faced by security teams. This can lead to compliance requirements that are either too stringent or not stringent enough, potentially leading to security gaps or inefficient use of resources.
When key security technologies such as firewalls, intrusion detection systems, and antivirus programs are managed in silos, it creates a significant risk: the inability to perform a unified analysis of critical security data. This segmented management approach hampers the ability to identify complex threats, which often require the aggregation and correlation of data from various security systems. A lack of integration can leave gaps in an organization's defense against advanced cybersecurity threats.
Siloed data security practices can result in varying levels of protection for sensitive information, potentially leading to data breaches and noncompliance with privacy regulations.
If threat intelligence is not shared across teams, each team is restricted to a partial view of the threat landscape. This can hinder the organization’s ability to effectively prepare for and respond to emerging threats.
When security policies are developed in isolation by different departments or teams, inconsistent or conflicting policies and controls can result. These inconsistencies can create loopholes that are exploitable by attackers.
The Power of Collaboration
Imagine a landscape where cybersecurity functions converge, share insights, and form a cohesive united front against threats. Collaborative cybersecurity is more than breaking down silos; it is about creating a symphony of interconnected expertise. When these separate domains align and pool their insights, they build a formidable and agile defense.
A collaborative approach dissolves barriers and cultivates a culture of shared knowledge and swift responses, empowering organizations to proactively tackle emerging threats and fortify their digital fortresses.
When teams work together, it is a win for everyone. They can prevent problems, save time and money, and enable everyone to learn from each other.
The Pillars of Collaborative Cybersecurity
The concept of collaborative cybersecurity is anchored on several key pillars, each vital to creating a unified and effective security posture. These pillars include:
- Information sharing and fusion—One of the most crucial aspects of collaborative cybersecurity is the free flow of information across various functions. By removing barriers to information sharing, organizations can ensure a seamless exchange of intelligence. This shared channel of communication enhances visibility and awareness of threats and vulnerabilities, facilitating the fusion of data for a more comprehensive understanding and insight into security challenges.
- Cross-domain teams and expertise—The creation of interdisciplinary teams comprising experts from different cybersecurity functions is essential. This approach ensures a well-rounded strategy for addressing security challenges. Such teams bring diverse perspectives and specialized knowledge that enable a deeper understanding of threats, vulnerabilities, and appropriate responses. The collaborative efforts of these cross-functional teams contribute significantly to developing robust security solutions.
- Integrated tools and technologies—The implementation of integrated cybersecurity tools is fundamental. These tools, which support effective communication and data sharing across different cybersecurity functions, are crucial in strengthening the overall security infrastructure. By using integrated technologies, cybersecurity teams can work more efficiently and effectively, as they have access to unified platforms that facilitate coordinated responses to security incidents.
These pillars form the foundation of a robust collaborative cybersecurity strategy in which information flow, team expertise, and technology integration work together to enhance an organization's ability to protect against cyberthreats and respond to cyberattacks. Collaboration among different cybersecurity functions can be enhanced by instituting a series of actions that make up the roadmap to collaboration (figure 1).
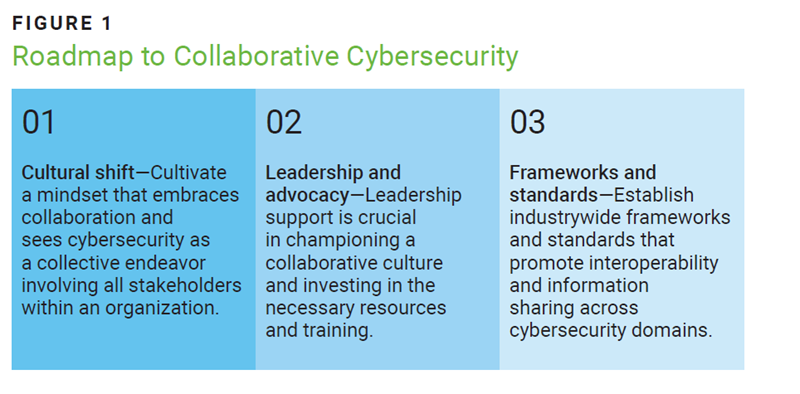
Conclusion
In an age when digital threats loom in every corner of the interconnected world, cybersecurity is on the vanguard against potential breaches and cyberattacks. Despite having sophisticated security functions in place, organizations continue to grapple with the elusive goal of achieving impenetrable security. Conversations around cybersecurity permeate boardrooms, but if a system of absolute safeguards is possible at all, it is still on a distant horizon.
It has become a truism that cybersecurity cannot thrive in isolation; it must be a thread woven integrally through the fabric of business and technology strategies. The silo mentality that eschews responsibilities beyond its scope reverberates to the core issue: Cybersecurity's essence defies isolation.
For an organization to fortify its defenses effectively, the imperative is clear: Cybersecurity functions must unite under a banner of collaboration. Isolated operations risk overlooking critical threats or exacerbating cyberattacks. Bridging internal divides is not just beneficial; it is imperative for a holistic defense strategy.
Endnotes
1 National Cyber Security Centre, “Cybersecurity Risk Management Framework,” Risk Management, United Kingdom, 23 June 2023, https://www.ncsc.gov.uk/collection/risk-management/cyber-security-risk-management-framework
2 Ratiu, R.; “Strengthening Collaboration for Cyberesilience: The Key to a Secure and Resilient Organization,” ISACA®, 17 July 2023, https://www.isaca.org/resources/news-and-trends/isaca-now-blog/2023/strengthening-collaboration-for-cyber-resilience-the-key-to-a-secure-and-resilient-organization
VISHAL SHARMA | M.SC, CISM, CEH, CIAM, CISMP, ITIL FOUNDATION, MCIIS, PRINCE2
Is a distinguished cybersecurity leader with more than 13 years of experience enhancing organizational security across various sectors including financial services, aerospace and defense, and oil and gas. He currently serves as the business information security officer at Santander Bank (United Kingdom). Sharma holds UK security clearance and has worked with renowned Big 4 consulting firms, demonstrating a profound ability to manage cyberrisk and design innovative security strategies. His expertise spans across cybersecurity governance, risk management, strategic planning, and operational technologies.
