The intersection of cybersecurity with environmental, social, and governance (ESG) criteria is crucial, with governance playing a vital role in mitigating risk within the ambit of the Fourth Industrial Revolution (4IR). As stakeholder capitalism gains prominence, ESG considerations increasingly influence enterprise strategies, emphasizing governance and encompassing cybersecurity and risk management. ESG scoring has evolved to incorporate aspects of cybersecurity, offering a framework for organizations to integrate their internal risk management with broader ESG efforts.
4IR technology convergence has implications for cybersecurity and ESG, and a holistic approach can be useful for managing cyberrisk in the context of ESG obligations.There is value in exploring the nuances of stakeholder vs. shareholder capitalism, the impact of ESG on corporate creditworthiness, and the specific methodologies used by rating agencies to assess ESG criteria, with a focus on governance. 4IR technology convergence has implications for cybersecurity and ESG, and a holistic approach can be useful for managing cyberrisk in the context of ESG obligations. It is also worth reviewing cyber-related credit actions by Moody's Investors Service and considering a cyberrisk breakdown structure as a tool for aligning cyberrisk assessments with ESG categories.
The growth in the market for cyberinformation is expanding, as is the importance of adopting sophisticated risk management practices to safeguard against increasing cyberthreats in the era of 4IR. This contributes to the sustainability and resilience of enterprises in alignment with ESG goals.
ESG and 4IR
There is a strong desire on the part of investors to favor enterprises that align with their values. This relatively new aspect of investing has driven many enterprises to shift their strategies and adopt changes in their governance practices. Much of this is encapsulated in the ESG movement, which focuses on the enterprise contribution to environmental, social, and governance aims. While much has been said and written about the environmental and social aspects of this movement, less attention has been paid to the strong cybersecurity and risk management ties in the governance component. It is important to understand recent developments in the cybersecurity industry, focusing on how ESG scoring has kept pace. Organizations that want to connect their internal risk management efforts to a broader effort may consider using the framework described herein to adopt a holistic approach to managing cyberrisk and security in the context of their ESG obligations.
ESG concerns have arisen in large part due to the rise in stakeholder capitalism, which emerged in opposition to the generally accepted model of shareholder capitalism promulgated by Milton Friedman (also known as the Friedman Doctrine), which holds that the social responsibility of the enterprise is to increase its profits.1 In contrast, stakeholder capitalism in the modern era, espoused by Klaus Schwab (of World Economic Forum fame), makes room in the ethics of profits for an impact on the broader world in which the enterprise operates.2 The reasoning is similar to economic discussions about externalities or unintended side effects of economic activities that affect parties who did not choose to incur those effects.
As the acronym implies, ESG can be broken down into three general areas of interest. The environmental concerns involve, for example, the way an enterprise’s operations contribute to the climate crisis. This area includes a view into third party activities and the influence an enterprise has over them. The environmental realm is also concerned with environmental sustainability—for example, whether the products and services offered can be responsibly sourced. Generally, the environmental category focuses on an enterprise’s negative economic externalities so as to avoid a tragedy of the commons with humanity’s shared environment. There are not any direct connections to cybersecurity to be found here.
The social aspects of ESG scoring concern the ways in which an enterprise considers how its activities impact human and animal welfare. Critically, this means complying with laws and regulations about hiring practices, at a minimum, and reporting on employment as it pertains to traditionally marginalized communities. Broader impacts on human rights across the globe are of concern in the social area (including in supply chains). The organization's policies on consumer protection also apply. And finally, how the organization impacts domestic animals, livestock, and wild animals is relevant. Once again, there are no direct connections to cybersecurity to be found here.
Last is the focus on governance. Governance reflects the way an organization structures its board and enterprise management hierarchy. Internal employee relations practices are subject to scrutiny and measurement as is the board’s position on executive compensation. There is a strong focus on how the organization manages audit, risk, and compliance. Within this final section, a strong focus on cybersecurity is evident.
The 4IR is the generally accepted collective term for the world’s current technology inflection point.3 It involves the convergence of cyber-physical systems, the Internet of Things (IoT)—especially regarding operational technology (OT), artificial intelligence (AI) and machine learning (ML), and various other biological and manufacturing advancements. Put simply, it is the “Internetization” of every aspect of the modern working world. Since much of the peril associated with these advancements has to do with broader existential concerns (e.g., negative economic externalities), it is fitting that many view the application of ESG to this problem space as a natural control solution.4
Overall, the concerns raised in ESG are in reverse order of immediacy. For instance, environmental concerns are often measured in decades. Social concerns are much more immediate, but not so much as governance problems, which can wreck an enterprise in relatively short order. Much of the popular media focus has been on the E and S aspects of ESG, but the G has strong relevance today, and its importance will only rise over time, irrespective of the other two.
ESG Assessment Examples
Several enterprises are providing ESG scoring for their clientele. Among the credit rating agencies, there is a strong belief that adherence to some sort of ESG program has a credit-positive effect5 In other words, not considering negative externalities has been shown to have a causal link to creditworthiness as expressed by one's credit default probability.6 This has undoubtedly brought the argument for ESG concerns to the board of directors and senior leadership teams. This is true despite some shifts away from ESG-based investing.7
An example ESG scoring rubric can be found in the Moody’s ESG Assessment Principles Methodology.8 This document outlines the procedures and scoring for the three primary ESG categories and their subdomains. In general, credit analysts must focus on a specific methodology for rating an enterprise but are allowed some latitude in adjusting scores based on ancillary scoring assessments. This process allows them to focus on the core enterprise financials while taking a position on other events that may impact the enterprise.
Filtering for the elements that have a direct impact on cyber, this methodology includes the following categories under governance:
- Financial strategy and risk management
- Management credibility and track record
- Compliance and reporting
- Board structure and policies
- Health and safety (under social)
Starting with the non-governance scoring area, health and safety has a critical connection to the 4IR. If the entity under evaluation creates hardware or software with the explicit or implicit ability to affect an individual’s health and safety, that must be considered. For example, cyber-physical systems involved in healthcare have a clear connection here, as do newer technologies such as self-driving cars.
The remaining governance items have an obvious cyber nexus. Take, for example, the focus on risk management, compliance, and reporting. The ability of an entity to consider cyber in its risk portfolio, ensure compliance, and accurately report on its cyberrisk has clear implications for an enterprise’s understanding of its own risk, as well as its maturity in managing such concerns (e.g., see the latest US Securities and Exchange Commission [SEC] rule on cybermateriality).9
Having cyber knowledge on the board means that there is a greater likelihood that such questions and concerns will be raised and discussed in board meetings and that funds will be allocated to address them. Management track records on such matters can be scrutinized. For example, a repeat offender variable is often used in the calculation of loss damages from cyberincidents.10
That is the framework for cyber evaluations in ESG. However, cyber-specific questions that Moody’s has posed to debt issuers only cover a minimal number of items:11
- Does the enterprise disclose a discussion of cybersecurity risk in the annual report or notice of the annual meeting?
- Does the enterprise disclose a requirement for the chief security officer (CSO) to report to the board of directors?
- Does the board identify any board member with cybersecurity experience?
There are only three yes/no questions valued at one point each. There is a very minimal impact on the overall ESG score. Yet there is a growing interest in getting deeper connectivity to organizational variables that could yield better intelligence for investors. Namely, if an investor were considering two enterprises and one had a worse security posture than the other, all other things being equal, the cyber evaluation would suggest a preferred investment strategy. So, leveraging information about an organization’s security profile has grown in recent years.
Interest in cybersecurity vendors that operate in the “security ratings” category is growing in the financial ratings community.12 These firms generally leverage data gathered externally to build a score correlated to the enterprise’s propensity to experience a cyberevent. There is a combination of offerings from pure cybersecurity vendors (primarily for third-party risk management use cases), as well as those originating from the credit rating agencies themselves.13
This interest in ratings has manifested in some organizations building digital trust and reputation management teams or allocating such responsibilities largely to their cyberrisk management teams. This practice has enabled some teams to connect their scores on one or more platforms to their internal issue-tracking system for remediation and prioritization. Although some argue that this practice amounts to “rate hacking,” the credit ratings agencies have accounted for this for decades, and the ever-evolving nature of cybersecurity underscores the need for security ratings to adjust their scoring algorithms to keep pace.14
Cyber Credit Actions
Credit rating organizations have already accounted for cyberevents over the past several years. By way of example, figure 1 identifies some of the actions taken by Moody's Investors Service based on a cyber cause.15
Figure 1: List of Cyber-Induced Credit Rating Actions by Moody’s
Investors Services16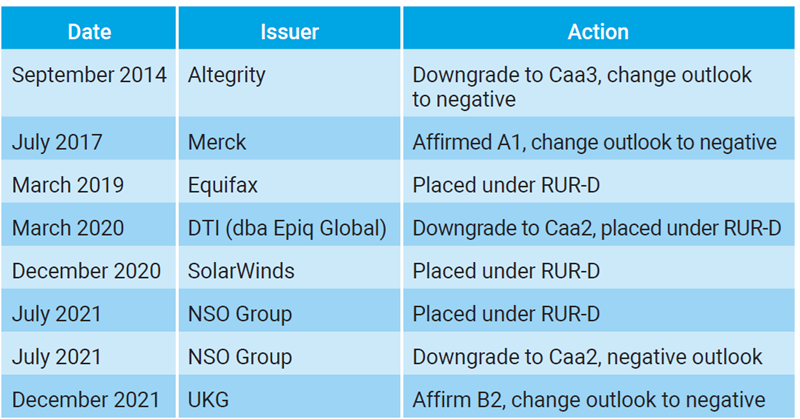
Some of these enterprise names will be familiar to cybersecurity professionals as the events they experienced have become widely popularized stories. Such is the case of Equifax’s notorious breach resulting in the exposure of information on 147 million people. The SolarWinds event is ongoing as of this writing, with US SEC charges against its chief information security officer (CISO), Tim Brown, still pending.17 The NSO Group was in the news for the use of its Pegasus monitoring software by nation-states across the world.18 For 2022, 2023, and the first quarter of 2024, Moody’s has taken no explicit credit rating actions against issuers due to cyberevents.
Incorporating ESG-Styled Ratings in Cyberrisk Assessments
A risk breakdown structure is a valuable tool that enterprise risk management departments frequently use to compartmentalize their risk universe.19 Its use in cyberrisk is somewhat limited but no less useful.20 If the previously referenced ESG categories are viewed as containers for operational risk, it is possible to layer them appropriately.
The operational risk categories enumerated in the Basel II standard are useful for decomposing risk into subsequent layers. Cyberrisk can be measured directly and then aggregated, as in this example risk breakdown structure based on two sets of categories:
1.0 —Financial Strategy and Risk Management
1.2 —Internal Fraud
1.2.1 —Insider Data Theft
1.3 —External Fraud
1.3.1 —Data Theft by Hackers
1.3.2 —Data Theft by Customers
1.4 —Damage to Physical Assets
1.4.1 — Natural Disasters Impacting Data Centers
1.4.2 —Man-Made Disasters Impacting Data Centers
1.5 —Business Disruption and System Failures
1.5.1 —Ransomware
1.5.2 —Distributed Denial of Service (DDoS)
1.5.3 —Website Vandalism
1.5.4 —Cloud Service Provider Outages
1.6 — Execution, Delivery, and Process Management
1.6.1 - Errors and Omissions
2.0 —(Product) Health and Safety
2.1 —Damage to Physical Assets
2.1.1 —Hardware Hacking and Manipulation
2.2 —Business Disruption and System Failures
2.2.1 —Ransomware
2.2.2 —Distributed Denial of Service (DDoS)
2.2.3 —Website Vandalism
2.2.4 —Cloud Service Provider Outages
2.3 — Execution, Delivery, and Process Management
2.5.1— Product Integrity Failures
The remaining ESG scoring categories are based on these decompositions and can be managed through metrics. For example, a management track record is a good key performance indicator for cyberevents (e.g., how many events necessitated disclosure in the past 18 months?). Board structure and policies are metrics that can be tracked: Ensure that board members have cyber knowledge and that the CISO reports to them regularly. Finally, compliance requirements should be incorporated into the risk breakdown (compliance controls should be aligned to these risk categories), and reporting from this process should be regular (including in annual reports).
The referenced categories could include more specific cyberevents, such as external theft of data from critical application X, internal data theft by privileged insiders, and so on. The outline shows three risk strata, with the first stratum being the ESG categories, the second stratum being the Basel II categories, and the third stratum being the cyber categories.
Enumerating further would require more tailored information about an organization's business model and technology profile, such as details about specific applications or groups of applications and enterprise products and services. A delineation between various threat actor groups that may perpetrate these activities would be evident.
Conclusion
The commercial marketplace for cyber information is growing. As the 4IR continues and technology permeates more of the products and services in the marketplace, the threat to core business models will grow. The investor community is actively seeking additional signals to explain how cybersecurity departments manage and govern their exposures in this area. Organizations are actively being rated this way, either voluntarily or involuntarily. This trajectory is similar to that of the credit rating products, which were actively resisted in the early days and were later embraced with the voluntary provisioning of more data.
For security ratings, this marks the difference between externally collected scan data and data collected through application programming interfaces (APIs) and empirical testing behind firewalls. All of this gathered data is being used to build profiles of security performance so that investors can understand the likelihood of an organization having an incident and the degree to which it conforms to the cyber governance aspects of its ESG rating methodologies.
Using a cyberrisk breakdown structure in the fashion outlined herein is a mature way to help ensure the responsible management of an organization’s cyberrisk exposure. Enterprises can begin by evaluating their risk governance framework. The aggregation of their cyberrisk should be built into risk assessment processes to help prepare for the inevitable cyber scoring that debt issuers will have to face in the future. The aggregation of cybersecurity control areas is going to form the foundation of scoring by third parties. Establishing a digital trust team or improving its capabilities will help manage perceptions of the organization’s security profile. This effort will be critical in building the necessary relationships with third parties.
Endnotes
1 CFI Team, “Friedman Doctrine,” CFI, https://corporatefinanceinstitute.com/resources/equities/friedman-doctrine/
2 Schwab, K.; Vanham, P.; “What Is Stakeholder Capitalism?,” 22 January 2021, World Economic Forum, https://www.weforum.org/agenda/2021/01/klaus-schwab-on-what-is-stakeholder-capitalism-history-relevance/
3 World Economic Forum, “Fourth Industrial Revolution,” https://www.weforum.org/focus/fourth-industrial-revolution/; Schwab, K.; “The Fourth Industrial Revolution: What It Means, How to Respond,” World Economic Forum, 14 January 2016, https://www.weforum.org/agenda/2016/01/the-fourth-industrial-revolution-what-it-means-and-how-to-respond/
4 Falconi, S.; King, R.; “How 4IR Is Enabling Policy-Making for a More Sustainable and Agile Future,” World Economic Forum, 15 September 2021, https://www.weforum.org/agenda/2021/09/4ir-tech-policy-making-challenges-future-governance/
5 Kanno, M.; “Does ESG Performance Improve Firm Creditworthiness?,” Finance Research Letters, vol. 55, part A, 2023, https://www.sciencedirect.com/science/article/abs/pii/S1544612323002660
6 Ibid.; Citi Global Insights, “The Impact of ESG on EM Credit,” Global Insights, 11 May 2021, https://www.citigroup.com/global/insights/global-insights/the-impact-of-esg-on-em-credit
7 Hartzmark, S.; Shue, K.; “Counterproductive Sustainable Investing: The Impact Elasticity of Brown and Green Firms,” SSRN, 4 December 2023, https://papers.ssrn.com/sol3/papers. cfm?abstract_id=4359282; Mirchandani, B.; “As Some Investors Walk Away From ESG, What Comes Next?,” Forbes, 22 January 2024, https://www.forbes.com/sites/bhaktimirchandani/2024/01/22/as-some-investors-walk-away-from-esg-what-comes-next/
8 Moody’s, General Principles for Assessing Environmental, Social and Governance Risks Methodology, https://www.moodys.com/research/doc--PBC_1355824
9 Freund, J.; Jorion, N.; “Determining Cyber Materiality in a Post-SEC Cyber Rule World,” ISSA Journal, vol. 21, iss. 9, 2023, https://cdn.ymaws.com/www.members.issa.org/resource/resmgr/journalpdfs2/feature0923.pdf
10 Jorion, N.; Freund, J.; “The True Cost of a Data Breach,” ISACA® Journal, vol. 1, 2023, https://www.isaca.org/archives
11 Pospisil, L.; Levy, A.; et al.; “Credit Risks in the Face of Cyber and Other Emerging Threats,” Virtual Spring Conference, June 2021, https://ma.moodys.com/rs/961-KCJ-308/images/06-21-2021%20Webinar%20on%20Cyber%20and%20Emerging%20Risks.pdf
12 Moody’s, “Moody’s and BitSight Partner to Create Integrated Cybersecurity Risk Platform,” 13 September 2021, https://ir.moodys.com/press-releases/news-details/2021/Moodys-and-BitSight-Partner-to-Create-Integrated-Cybersecurity-Risk-Platform/default.aspx
13 S&P Global, “Cyber Risk Solutions,” https://www.spglobal.com/ratings/en/products-benefits/products/cyber-risk-solutions
14 HIS Markit, “Cybersecurity Factors Powered by BitSight,” February 2018, https://cdn.ihsmarkit.com/www/pdf/Cybersecurity_factors_powered_by_BitSight.pdf
15 Compiled from public ratings notifications published in Moody’s “Reports Directory,” https://www.moodys.com/reports/ratings-assessments-reports
16 Moody’s nomenclature for ratings can be cryptic. RUR-D means “rating under review” with the expectation that it will be downgraded. Ratings span from AAA (best) to C (worst). Complete information about the ratings can be found at https://www.moodys.com/sites/products/productattachments/ap075378_1_1408_ki.pdf
17 US Securities and Exchange Commission (SEC), “SEC Charges SolarWinds and Chief Information Security Officer With Fraud, Internal Control Failures,” USA, 30 October 2023, https://www.sec.gov/news/press-release/2023-227
18 Shankland, S.; “Pegasus Spyware and Citizen Surveillance: Here’s What You Should Know,” CNET, 19 July 2022, https://www.cnet.com/tech/mobile/pegasus-spyware-and-citizen-surveillance-what-you-need-to-know/
19 Freund, J.; “Cybersecurity and Technology Risk,” Operational Risk Perspectives: Cyber, Big Data, and Emerging Risks, Risk Books, United Kingdom, 2016
20 Freund, J.; “Communicating Technology Risk to Nontechnical People: Helping Enterprises Understand Bad Outcomes,” ISACA Journal, vol. 3, 2020, https://www.isaca.org/archives
JACK FREUND | PH.D., CISA, CISM, CRISC, CGEIT, CDPSE
Is the chief risk officer for Kovrr, where he oversees corporate risk and compliance, along with strategy and governance of the firm’s cyberrisk products. He is also the coauthor of the foundational cyberrisk quantification (CRQ) book using the FAIR standard, which was inducted into the Cybersecurity Canon in 2016. Freund was named an ISSA Distinguished Fellow, a FAIR Institute Fellow, an IAPP Fellow of Information Privacy, and an ISC2 2020 Global Achievement Awardee. He was also a recipient of ISACA’s 2018 John W. Lainhart IV Common Body of Knowledge Award. He currently serves on the board of the ISSA Education Foundation.



