In an era when digital transformation is at the forefront of organizational strategies, the importance of incorporating cybersecurity into project management processes cannot be overstated. Project managers play a crucial role in ensuring that cybersecurity measures are seamlessly integrated into every phase of the system development life cycle (SDLC). There is value in exploring the significance of cybersecurity and offering insights and recommendations for project managers to fortify their projects against evolving cyberthreats.
Understanding SDLC Phases
The SDLC is a cost-effective and time-efficient process that development teams use to design and build high-quality software. The goal of the SDLC is to minimize project risk through forward planning so that software meets customer expectations during production and beyond (figure 1).
The SDLC consists of several interconnected phases, each contributing to the overall success of the project. These phases typically include planning, analysis, design, implementation, testing, deployment, and maintenance. To effectively incorporate cybersecurity, project managers must consider cybersecurity principles at every stage:
- Planning—In the planning phase, project managers define the scope, objectives, and deliverables of the project. Cybersecurity considerations at this stage involve identifying potential risk factors and establishing a robust risk management plan. This plan should include a comprehensive analysis of potential cyberthreats, vulnerabilities, and the impact of a security breach.
Additionally, project managers should allocate resources for cybersecurity measures, ensuring that the necessary tools, technologies, and expertise are integrated into the project budget. Stakeholder communication and awareness programs can also be initiated during this phase to promote a cybersecurity-conscious culture within the project team. - Analysis—During the analysis phase, requirements are identified and the project team conducts a detailed analysis of the system's desired functionalities. Cybersecurity should be addressed in this phase by incorporating security requirements into the overall system requirements. Threat modeling can be employed to reveal potential security flaws and weaknesses in the system's architecture.
Project managers should collaborate with cybersecurity experts to ensure that security controls are aligned with identified risk. This phase is also a good time to define access controls, authentication mechanisms, and data encryption requirements, laying the foundation for a secure system. - Design—In the design phase, the system architecture is planned based on the requirements identified in the previous phases. Cybersecurity considerations in this phase involve implementing security controls such as firewalls, intrusion detection systems, and secure coding practices into the overall system design.
Collaboration among project managers, developers, and cybersecurity experts is crucial to ensure that the design effectively mitigates any potential security risk. Design reviews1 should specifically address secure coding principles, secure data storage, and security frameworks. - Implementation—The implementation phase involves coding, unit testing, and integrating various components. Cybersecurity measures during this phase include secure coding2 practices (e.g., input validation and output encoding,3 cryptographic practices,4 error handling and logging5), regular code reviews, and the use of automated tools to identify and address vulnerabilities.
Project managers should ensure that the development team adheres to established security guidelines and standards. Continuous monitoring and testing should be conducted to identify and remediate any security issues promptly. Additionally, this is an opportune time to implement secure deployment practices, including secure configuration settings for servers and network devices. - Testing—The testing phase is critical for identifying and rectifying potential security vulnerabilities before deployment. Security testing, including penetration testing and vulnerability assessments, should be an integral part of the testing strategy. This phase provides an opportunity to evaluate the effectiveness of the implemented security controls and address any issues identified during testing.
Project managers should collaborate with cybersecurity experts to define comprehensive test scenarios that simulate real-world cyberthreats.6 Automated testing tools can be employed to ensure thorough and consistent security testing. The testing phase is also an ideal time to conduct training sessions for the project team on security incident response procedures. - Deployment—The deployment phase involves the release of software to end users. Cybersecurity considerations in this phase include implementing secure deployment practices, conducting a final security assessment, and ensuring that the deployment environment adheres to security standards.
Project managers should coordinate with system administrators to implement security patches promptly and monitor the system7 for any anomalies or security incidents. User training on security best practices can be conducted during this phase to enhance the overall security posture of the system. - Maintenance—The maintenance phase involves ongoing support, updates, and enhancements to the software. Cybersecurity measures in this phase include monitoring for new vulnerabilities, applying security patches, and conducting periodic security audits.
Project managers should establish a robust incident response plan and communicate it to the project team. Regular security awareness training for all stakeholders, including end users, is essential to maintain a proactive security culture throughout the system's life cycle (figure 2).
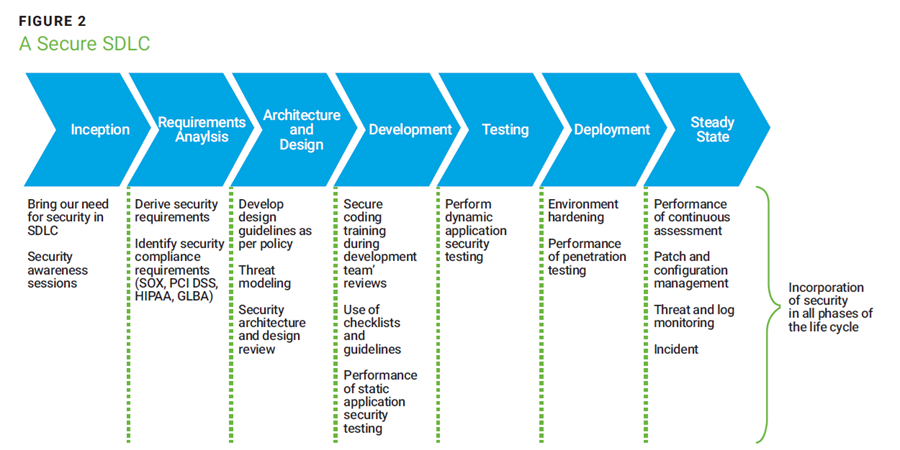
Source: Subramanian, S.; Swaminathan, B.; “Security Assurance in the SDLC for the Internet of Things,” ISACA® Journal, vol. 3, 2017, https://www.isaca.org/archives
While incorporating cybersecurity into every phase of the SDLC is crucial, several challenges and considerations must be addressed by project managers:
- Resource constraints—Limited budgets and resources may pose challenges for the implementation of comprehensive cybersecurity measures. Project managers must prioritize cybersecurity initiatives based on risk assessments and allocate resources effectively.
- Skills gap—Cybersecurity expertise may not be readily available within the project team. Collaborating with external cybersecurity specialists or providing training for existing team members can help address this skills gap.
- Changing threat landscape—The dynamic nature of cyberthreats requires constant vigilance and adaptation. Project managers should stay informed of emerging threats and technologies and adjust their cybersecurity strategies accordingly.
- User awareness—Users play a significant role in cybersecurity. Project managers should invest in user training programs to enhance awareness and promote responsible cybersecurity behavior among end users.
Conclusion
The integration of cybersecurity into every phase of the SDLC is imperative for building resilient and secure software systems. Project managers are responsible for fostering a cybersecurity-conscious culture within their teams and collaborating with cybersecurity experts to address the evolving threat landscape. By incorporating cybersecurity principles from the project's inception, enterprises can significantly reduce the risk of security breaches and safeguard sensitive data. In an era when cyberthreats are prevalent, a proactive and holistic approach to cybersecurity by project managers is not merely a best practice but a necessity for the sustained success of software development projects.
Endnotes
1 OWASP, “Secure Product Design Cheat Sheet,” https://cheatsheetseries.owasp.org/cheatsheets/Secure_Product_Design_Cheat_Sheet.html
2 OWASP, “OWASP Top Ten,” https://owasp.org/www-project-top-ten/
3 Identifying all data inputs and sources is crucial, followed by validating those marked as untrusted. Employing a standardized process for output encoding and input validation is imperative.
4 Utilizing contemporary cryptographic algorithms to encrypt data, alongside adhering to best practices in secure key management, enhances the security of code, especially in the event of a breach.
5 Logging errors in documentation enables developers to diagnose and address their underlying causes effectively. Documentation and logging of all failures, exceptions, and errors should be implemented on a trusted system to comply with secure coding standards.
6 Jones, C.; “The Top 10 Threat Simulation Platforms,” Expert Insights, 30 April 2024, https://expertinsights.com/insights/the-top-10-threat-simulation-platforms/
7 Kushchi, S.; “Top 10 Continuous Security Monitoring (CSM) Tools for 2024,” Jit, 5 June 2024, https://www.jit.io/blog/continuous-security-monitoring-csm-tools
RAJANIKANTH POTTURI | CISM, CISSP, PMP
Is an ISS-GRC lead with Meta Platforms Inc. He is a seasoned infra and information security professional with more than 20 years of expertise in the IT industry specializing in social media, property and casualty insurance, healthcare, and cybersecurity. Throughout his career, he has held leadership positions in renowned IT consulting firms, leading the development of innovative solutions and spearheading major initiatives in application modernization and automation with respect to information security, infrastructure scalability, and governance, risk, and compliance (GRC). With a profound understanding of the industry, Potturi has successfully served many Fortune 500 clients by delivering innovative solutions. His passion lies in harnessing disruptive cloud and security technologies, particularly in the social media cybersecurity domain, to create robust and efficient systems.
