In a world filled with emerging tensions and accelerating digital transformation, organizations must confront the challenge of generating value and responding to the concerns of their shareholders and different stakeholders. Rogue waves–radical changes that challenge the current state of being—are ushering in surprising shifts and impacts for enterprises and their strategic business plans, and they must learn to navigate the uncertain waters accordingly.1
Organizations that wish to reach a privileged strategic position amid market volatility must be smart about the risk they are willing to accept. This means that they will need to recognize what level of risk they are prepared to shoulder and discuss how to equip themselves to manage it. The challenge organizations face lies in balancing their operating thresholds when things do not go as planned (e.g., a successful cyberattack), understanding the maximum risk capacity they can withstand, and implementing the proposed initiatives.2
In guiding organizations towards these decisions, the board of directors (BoD) assumes a pivotal role in the orientation and direction of organizations to select the best business strategies that not only allow them to challenge current business plans, but also inspire the necessary transformations in the executive teams. The organization must proactively address the opportunities and challenges presented by its environment. To achieve this, it must embrace a business plan that leads to the strengthening of its competitive advantages and consolidates a portfolio of key capabilities to evolve with the asymmetric trends it is facing.3
Currently, BoDs are exposed to the systemic challenges of cyberrisk in the face of an accelerated increase in digital density (greater connectivity and information flows over physical objects), which can lead to cascading cyberfailures (the result of one cyberincident propagating outward and causing many disruptions), common-cause cyberfailures (the result of one cyberexploit triggered at many enterprises causing many cyberincidents), or independent cyberfailures (the result of cyberincidents exploiting independent vulnerabilities at individual firms and organizations).4 These failures often end up affecting not only economic and reputational indicators, but also the trustworthiness of the organization itself, and result in a loss of credibility on the part of investors who see their interests threatened by these types of events.
Thus, it is crucial to determine the maturity level of BoDs in terms of their governance and management of cybersecurity risk. This is conducted to establish the level of commitment, understanding, and relevance that the board possesses when dealing with risk. Suitable monitoring and safeguarding allow the organization to deal with an adverse cyberevent and enable a resilient response, thus reducing the impact on both the organization and its stakeholders.
A study was conducted to examine the proficiency of BoDs in governance and cyberrisk management. This study could be considered the first to be conducted in Colombia to establish the level of maturity of boards of directors in the governance and management of cyberrisk. In this sense, its results reveal the challenges that some boards must address and improve in the understanding and supervision of cyberrisk as a fundamental element of business strategy and the promise of value for their clients—particularly issues related to the ability to develop cybercrisis scenarios and exercises.
Enterprise Governance, BoDs, and Cyberrisk
Research conducted in Latin America has found that “All companies, regardless of their size and ownership structure, should adopt a corporate governance model that appropriately balances the proper exercise of the rights of shareholders and the preservation of the company’s purpose, in order to generate value and growth that also takes into consideration diverse stakeholders.”5 In this context, the BoD plays a crucial role in ensuring the successful development of the enterprise and safeguarding shareholder investments.
In an increasingly technologically modified landscape, organizations are exposed to the reality of cyberrisk, a systemic risk that generates contagious, domino–like effects that may start with known adverse cyberevents and can rapidly evolve to permeate an entire organization. Events such as these can quickly compromise sensitive or legally protected data and business operations altogether, inevitably harming and impacting the value outlook for various stakeholders.6
BoDs must fulfill their role in challenging enterprise practices, particularly as they relate to cyberrisk. This means that they must take on increasing responsibilities and expectations in shorter periods and more trying situations.7 Oversight of cyberrisk concerning the interests of shareholders implies not simply knowing that the risk exists and ensuring that it is monitored by the audit committee. It also requires an understanding of its dynamics and impacts resulting from emerging risk that can create unexpected and uncertain situations that compromise the process of the enterprise, its value outlook, and therefore, the trust of investors.
BoDs must fulfill their role in challenging enterprise practices, particularly as they relate to cyberrisk. This means that they must take on increasing responsibilities and expectations in shorter periods and more trying situations.Recent studies conducted by EY published in their global board risk survey8 confirm that only 40% of boards are confident that they understand the cyberrisk facing their organization. Additionally, only one-third of board members feel confident about the amount of time they dedicate to discussing risk. This means that boards spend little time and effort on understanding the inherent challenges of cyberrisk, leaving it in the hands of specialized departments such as technology or cybersecurity, creating a gap not only in knowledge but also in exposure. This results in silos of responsibility that ultimately benefit attackers when they are successful in their cyberaggressions. These statistics highlight the potential harm and risk that can be generated in terms of stakeholder trust and financial results.
Consider this example. In August 2023, Clorox, a global manufacturing company, was targeted in a cyberattack that disrupted operations and caused damage to IT systems. The BoD failed to provide effective oversight of cyberrisk, resulting in severe consequences for the company. Instead, the board blamed hostile external agents and held technological personnel responsible. The board’s actions led to a loss of trust among various stakeholders, in addition to a drop in revenue of nearly $500 million and a loss of more than $3 billion in stock value.9
In the 2023 proxy statement,10 it was revealed that:11
- Initial statements by the outgoing president and the new CEO made no mention of cybersecurity.
- Eight directors were appointed to oversee cybersecurity. However, not one of the appointees has professional experience in IT or cybersecurity.
- Despite the swift pace of evolution in the digital era, Clorox opted to not establish a technology or cybersecurity committee.
- The statement on cyberreadiness was given by the director of information and data, acting as chief exercises that are coordinated and developed information security officer (CISO), who had no with the different participants of the organization, experience in the field.
Maturity Model for the Governance Management of Cyberrisk
In today's digitally focused society, the increased use of technology has led to emerging digital threats that BoDs must address. The Maturity Model for the Governance and Management of Cyberrisk12 (figure 1) encompasses five basic elements that seek to create develop capabilities that did not exist previously in management. These elements help update the doctrine of enterprise risk management and encourage a more vigilant enterprise perspective regarding emerging instability and challenges. Current cybersecurity models emphasize the treatment of known risk, which can create a false sense of security based on compliance with standards and best practices.
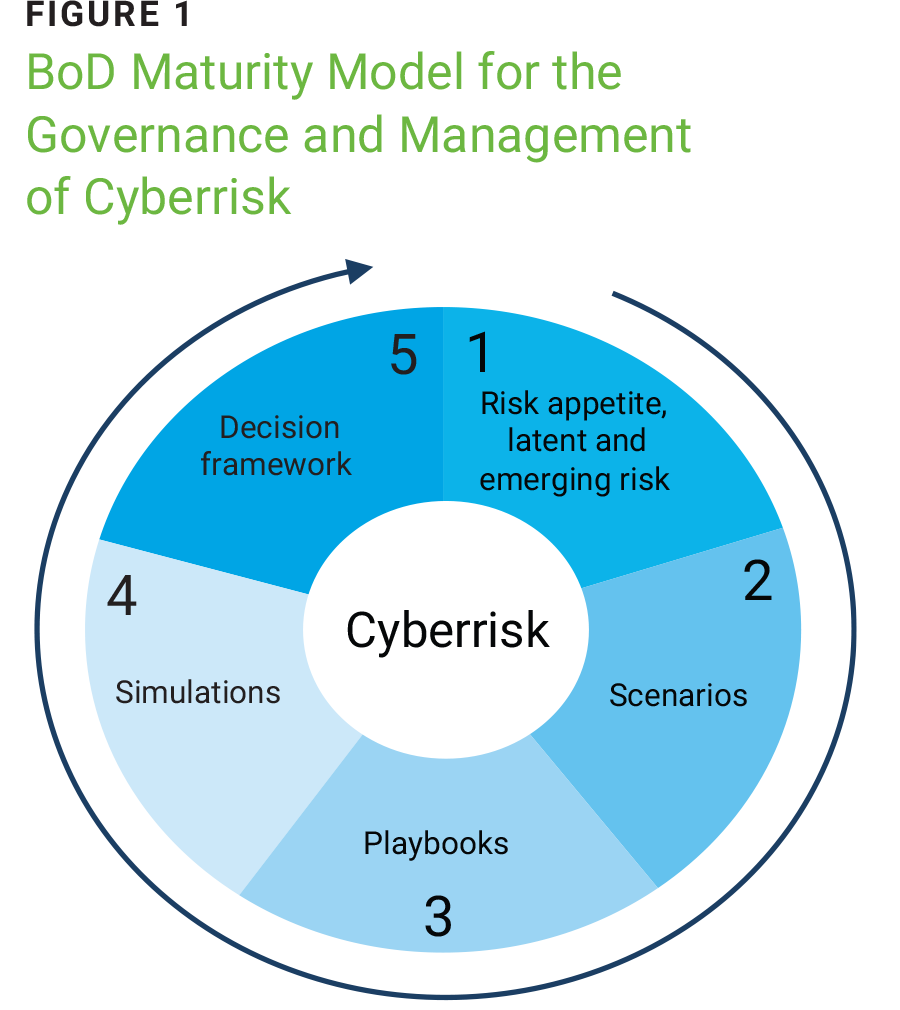
Source: Cano, J.; “Maturity Model for Boards of Directors in Cyber Risk Governance. A Conceptual and Practical Proposal,” Developments and Advances in Defense and Security, 2023, https://link.springer.com/chapter/10.1007/978-981-19-7689-6_4. Reprinted with author's permission.
The five elements of the model include:
- Risk appetite and the latent and emerging risk framework—The organization identifies the risk that it is not willing to accept in terms of its values, those that it is willing to accept in terms of its digital strategy, the impacts and effects (should the risk materialize) on stakeholders, and the actions required to combat future risk.
- Scenarios—The second element aims to introduce scenarios for study and analysis to challenge the existing knowledge of the participants (board members, executives, employees). This is done in order to lead them to possible, probable, and challenging moments and situations that allow for the emergence of analysis and solutions that may be unorthodox.
- Playbooks—The third element is the creation of playbooks, which are activated in the event of an adverse cyberevent. Their purpose is to bring forward the required coordination and communication needed to appropriately mobilize the organization amid instability and uncertainty in order to follow an action protocol that permits an orderly response. This element features set roles and managed communications, which reflect the reliability and commitment of the enterprise in the face of the event that has occurred.
- Simulations—The fourth element features including top-tier executives, in order to have a practice field where predetermined scenarios unfold and planned playbooks are activated. In this context, executives need to follow the guidelines and strategies that have been established for the adverse events selected. Their actions and decisions should respond to the tensions and instabilities that present themselves with regard to the protection of the organization’s reputation.
- Decision framework—The fifth element focuses on maintaining an operating threshold structure that allows executives to discuss and determine the best options for assisting and mobilizing the organization amid tensions and instabilities produced by the materialization of cyberrisk. That is, defining levels of alert and activation, which are translated into specific situations and activities that must be confirmed based on the information received and consolidated by the support team related to dealing with and managing risk.
These five elements move the organization from its comfort zone of standards and best practices centered on certainties to a context based on uncertainties and instabilities. This tests the resilience of the organization and the commitment of board members to the inevitability of failure in the cyberlandscape.
Assessing the Maturity of BoDs in Managing Cyberrisk
It must be understood that maturity is a sustained effort that becomes a habit, not a target to be achieved.13 In order to understand this concept more thoroughly, a cyberrisk assessment was conducted by taking a sample of 56 members of BoDs from companies in Bogota, Colombia. The purpose of the exercise was to identify relevant insights, acknowledge progress and limitations in how organizations in Bogota treat risk, and determine whether the organizations address risk in a manner that goes beyond the measures considered standard practice.
The tool used to conduct this diagnostic was a survey based on a descending Likert scale (5–totally agree, 4–agree, 3–neutral, 2–disagree, 1–totally disagree) used to respond to three statements related to each of the components of the maturity model displayed in figure 1.
The numerical ratings on the scale indicate the following:
- 1 and 2: Low level of maturity—Reactive and oriented toward dealing with cyberrisk events as they arise
- 3: Medium level of maturity—No real commitment on the part of the board, leading to instability in cyberrisk governance
- 4: High level of maturity—A specific commitment on the part of the board that leads to a proactive position regarding the governance of cyberrisk in the organization
- 5: Very high level of maturity—The BoD assumes responsibility for the cyberrisk, making its governance efforts sustainable over time.
The survey results are illustrated in figure 2.
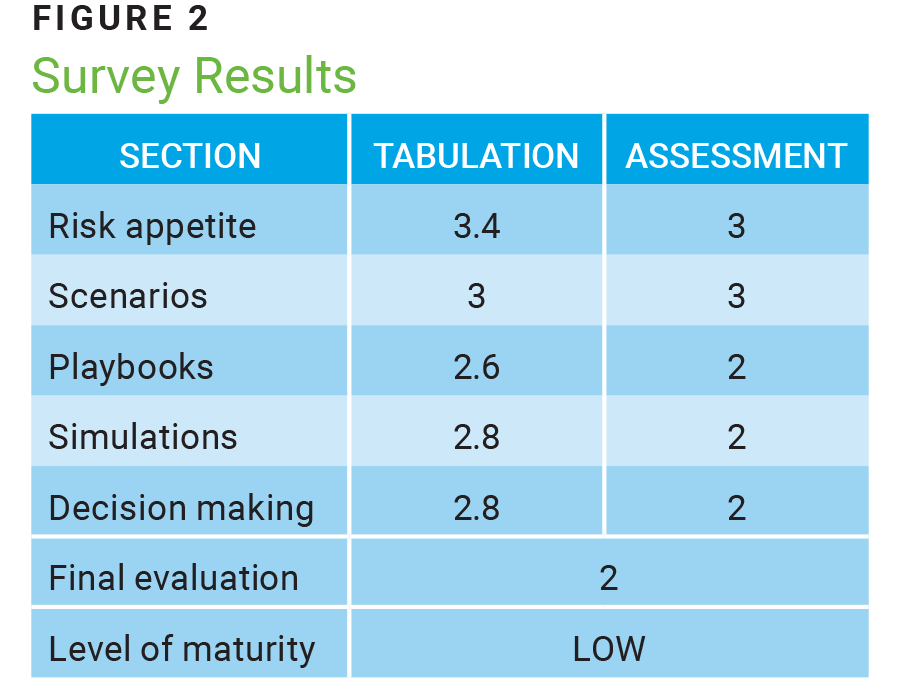
It is important to note that both the evaluation of the components and the final evaluation are based on the consideration of the laws of physics that indicate that the system always tends toward the area of least stress. For this reason, the decimals in the tabulation are eliminated, leaving the integer value in the assessment cell, suggesting that the organization must maintain a sustained effort to maintain and improve its subsequent assessments.
Recommendations for Improving the Maturity Assessment Level
The findings underscore the need for BoDs to update their strategies to effectively tackle the cyberrisk confronting their organizations. Accordingly, the recommendations for each of the sections of the model are discussed in detail in figure 3.

These recommendations take into account the current challenges BoDs face regarding enterprise cybersecurity. They are an essential element of the practice of building competitive advantages and specifying new experiences for customers, which translates into:
- Recognizing emerging risk and developing smart capabilities
- Responding to predictable surprises14 and developing resilient capabilities
- Reflecting on successful cyberattacks and developing learning/unlearning capabilities
Conclusion
An organization’s BoD is necessary to challenge enterprise strategy and inspire medium and long-term planning.15 Directors or board members play a crucial role in:16
- Defining the strategic guidelines for the long-term sustainable growth of the organization
- Providing expert and objective knowledge regarding environmental and business conditions
- Overseeing the accomplishment of the enterprise's purpose
- Monitoring the performance of the enterprise and the top management team
- Ensuring the effectiveness of the organization’s monitoring and risk management system
- Acting as a link to shareholders
Accordingly, the cyberrisk that is characterized by being uncertain, unstable, and nonlinear demands special attention on the part of enterprise directors, who must keep in mind increasing enterprise digital transformation and individual connectivity and mobility. A digital ecosystem of interactivity and the pairing of its different components creates new areas of attack that can and will be taken advantage of by adversaries.
Cyberrisk is a newly arrived responsibility for BoDs, who may go through the grieving process of denial, anger, bargaining, depression, and acceptance as a natural part of grasping and taking on a new challenge.17 Cybersecurity leaders and external consultants can help advance the digital literacy of board members in the face of such risk. This ultimately aids in the development and strengthening of a vigilant and resilient organizational posture.
As the executive team matures in cyberrisk governance, the organization will be able to:
- Defend and protect its value proposition in a context of evolving cyberthreats.
- Optimize cyberdefense, radar, crisis, and monitoringcapabilities.18
- Enable digital initiatives that create new experiences for its clients/customers.
- Ensure digital trust in the technological ecosystem in which it operates.
The results of the application of the maturity model depicted here are a starting point for advancing along a maturity roadmap for BoDs in the face of cyberrisk. The maturity model should not be seen as a normative obligation with which boards must comply, but rather, as an exercise in ongoing learning in order for the board to develop safe psychological spaces19 where the questions and the challenges are a natural part of the ongoing challenge of the capabilities available to the enterprise.
Acknowledgments
The author is grateful for the willingness, trust, and support of the board of directors of the ISACA Bogota Chapter 2022-2023 for making this study possible and to the members of the boards of directors of the Bogota companies who kindly participated in this research on a voluntary basis and with informed consent.
Endnotes
1 Brill, J.; Rogue Waves: Future-Proof Your Business to Survive & Profit From Radical Change, McGraw Hill, USA, 2021
2 Lam, J.; Implementing Enterprise Risk Management: From Methods to Applications, Wiley, USA, 2017
3 Hamel, G.; Prahalad, C. K.; Competing for the Future, Harvard Business Review Press, USA, 1996; Pederson, K.; “How to Achieve Enduring Board Effectiveness,” EY, 13 September 2022, https://www.ey.com/en_us/board-matters/how-to-achieve-enduring-board-effectiveness
4 Welburn, J.; Strong, A.; “Systemic Cyber Risk and Aggregate Impacts,” Risk Analysis, vol. 42, iss. 8, 2022, p. 1606-1622, https://onlinelibrary.wiley.com/doi/10.1111/risa.13715
5 Oneto, A.; Rojas, C.; “Guidelines for a Latin American Corporate Governance Code,” Development Bank of Latin America and the Caribbean, 2023, https://scioteca.caf.com/handle/123456789/2165
6 Op cit Welburn
7 Mayor, J.; Defining a Method to Evaluate Boards of Directors Effectiveness, International University of Catalonia, Spain, 2017, https://www.tdx.cat/bitstream/handle/10803/580598/Tesi_Jaime_Grego_Mayor.pdf; Organization for Economic Co-operation and Development, Board Evaluation: Overview of International Practices, 2018, https://web-archive.oecd.org/2018-10-02/494906.Evaluating-Boards-of-Directors-2018.pdf; Asahak, S.; Albrecht, S.; et al.; .Boards of Directors: AssessingTheir Functioning and Validation of a Multi-Dimensional Measure,” Frontiers in Psychology, vol. 9, 2018, https://www.frontiersin.org/journals/psychology/articles/10.3389/fpsyg.2018.02425/full
8 EY, How Can Boards Prioritize Resilience to Build Trust and Create Value? Global Board Risk Survey 2023, 2023, https://assets.ey.com/content/dam/ey-sites/ey-com/en_gl/topics/global-board-risk.survey/ey-global-board-risk-survey-2023.pdf
9 Barsky, N.; “Clorox Scapegoats Cyber Chief, Rewards Board After Crisis,” Forbes, 20 November 2023, https://www.forbes.com/sites/noahbarsky/2023/11/20/clorox-scapegoats-cyber-chief.rewards-board-after-crisis/?sh=1baf9b6540ed
10 A proxy statement is a document that contains the information that the US Securities Exchange Commission (SEC) requires companies to provide to shareholders so that they can make informed decisions regarding matters that will be brought up at an annual or extraordinary shareholder meeting.
11 United States Securities and Exchange Commission, Schedule 14A Proxy Statement Pursuant to Section 14(a) of the Securities Exchange Act of 1934, USA, 2023, https://www.sec.gov/ix?doc=/Archives/edgar/data/0000021076/000120677423001183/clx4223771-defr14a.htm
12 Cano, J.; “Maturity Model for Boards of Directors in Cyber Risk Governance. A Conceptual and Practical Proposal,” Developments and Advances in Defense and Security, 2023, https://link.springer.com/chapter/10.1007/978-981-19-7689-6_4
13 Pernet, E., Cano, J.; “A Systemic GRC Maturity Model,” Proceedings of the 58thAnnual Meeting of the ISSS—2014, 2015, https://journals.isss.org/index.php/proceedings58th/article/view/2232
14 Watkins, M.; Bazerman, M.; “Predictable Surprises: The Disasters You Should Have Seen Coming,” Harvard Business Review, April 2003, https://hbr.org/2003/04/predictable-surprises-the-disasters-you-should-have-seen-coming
15 Nordberg, D.; Booth, R.; “Evaluating the Effectiveness of Corporate Boards,” Corporate Governance, vol. 19, 2019, p. 372-387, https://www.emerald.com/insight/content/doi/10.1108/CG-08-2018-0275/full/html
16 Op cit Oneto
17 Gorge, M.; The Cyber-Elephant in the Boardroom: Cyber-Accountability With the Five Pillars of Security Framework, ForbesBooks, USA, 2021
18 Cano, J.; “Modes of Operation of Enterprise Cybersecurity. Basic Capabilities for Navigating the Digital Context,” Global Strategy, Global Strategy Report No. 44, 27 October 2021, https://global-strategy.org/modos-de-operacion.de-la-ciberseguridad-empresarial-capacidades.basicas-para-navegar-en-el-contexto-digital/
19 Edmondson, A.; The Fearless Organization: Creating Psychological Safety in the Workplace for Learning, Innovation, and Growth, Wiley, USA, 2018
JEIMY J. CANO M. | PH.D, ED.D, CFE, CICA
Has more than 28 years of experience as an executive, academic, and professional in information security, cybersecurity, forensic computing, digital crime, and IT auditing. He received the ISACA® Educational Excellence Award in 2023 and in 2016 was named Cybersecurity Educator of the Year for Latin America by the Cybersecurity Excellence Awards. He has published more than 250 articles in a range of journals and has given talks at industry events worldwide.
