Because smartphones and tablets are often used to store and access financial data, personal communications, and enterprise documents, they are prime targets for cybercriminals. The number of attacks on mobile devices has experienced exponential growth. In 2023, 33,790,599 attacks were reported, a 52% increase over 2022 figures.1 The widespread adoption of cloud technologies, the Internet of Things (IoT), and bring-your-own-device (BYOD) policies have also contributed to an increased potential for cyberattacks, including malware, phishing attacks, and data breaches.
The widespread adoption of cloud technologies, the Internet of Things (IoT), and bring-your-own-device (BYOD) policies have also contributed to an increased potential for cyberattacks, including malware, phishing attacks, and data breaches.Given the sensitive nature of information stored on mobile devices, the consequences of a breach can be severe. To prevent data leakages, a robust, multilayered mobile security strategy, encompassing both the security of the physical device itself and the security of its applications, is necessary. Strong passwords, multifactor authentication (MFA), data encryption, and regular software patches are all important contributors to mobile security. Equally vital is educating users about safe browsing habits and the importance of application permissions. By prioritizing mobile security, individuals and organizations can safeguard their digital assets and maintain the confidentiality, integrity, and availability of data on mobile platforms.
Technological Shifts and Increased Security Vulnerabilities
In the past decade, computing has consistently moved toward increased mobility and flexibility. As of 2024, 59% of all web traffic came from mobile devices.2 Device traffic is not limited to personal use, with mobile applications becoming an increasingly vital part of workplace operations. The adoption of mobile devices is a significant factor in many enterprises’ decisions to adopt cloud computing solutions.3 Cloud computing offers enterprises scalability and convenience but increases security concerns such as data leakage, loss, and privacy issues.4 Additionally, mobile devices typically connect to many different Wi-Fi networks, leaving them vulnerable to fraudulent or compromised connections.
Many organizations in myriad sectors utilize the same open-source or commercially available libraries and software. As a result, a cybersecurity vulnerability has the potential to affect hundreds of thousands of enterprises simultaneously. For example, when Log4j, a popular open-source logging framework, was found to have a zero-day vulnerability, tens of thousands of systems across enterprises were at risk.5 Meanwhile, IoT has grown in scope. Between 2014 and 2019, the number of enterprises using IoT increased from 13% to 25%, and adoption continues to grow.6 These trends add up to a massive attack surface for cybercriminals.
At the same time, organizations are implementing BYOD policies, in which employees are permitted to use their own devices at work. This increases the possible consequences of a mobile security breach; if the device is lost or stolen, both professional and personal data is compromised. The BYOD paradigm also introduces new security vulnerabilities, as it is more difficult to secure devices that are stored in a variety of locations and connect to multiple different networks than those that remain in the office and are protected by internal firewalls.
Cybercriminal Attack Techniques
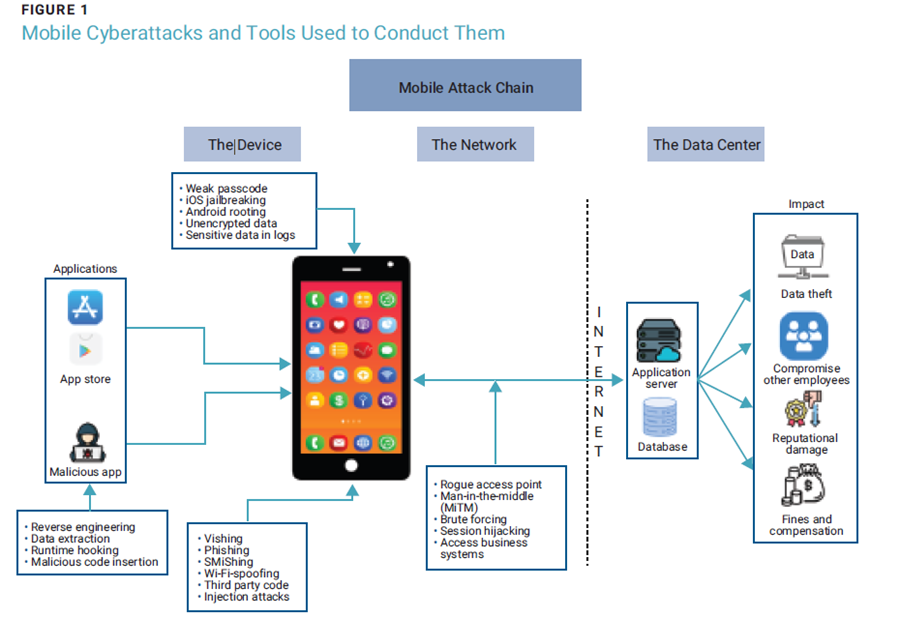
Cyberattacks on mobile devices often involve a degree of social engineering. In addition to common attack methods such as phishing, cybercriminals often employ (figure 1):
- Vishing—Also known as “voice fishing,” vishing involves an attacker impersonating another entity, usually a government or law enforcement organization, and calling targets to defraud them of money. Increasingly advanced vishing apps such as SecretCalls and SIM Box which allow attackers to impersonate other numbers, are enabling a rise in sophisticated, costly vishing attacks worldwide.7
- Trojan horse attacks—These attacks use seemingly innocuous email attachments, files, or programs to spread malware.
- WiFi spoofing attacks—Hackers impersonate known Wi-Fi networks during these attacks. If a user connects to the compromised network, attackers can collect information sent over the network without the user’s knowledge.
- Malicious apps—Mobile applications can be designed by hackers to collect and transmit data. Often, they are designed to look like legitimate apps in Google Play or Apple’s App Store but are hosted in third-party stores that do not verify app offerings.
- MFA bombing attacks—Sometimes referred to as MFA fatigue attacks, the attacker utilizes stolen user credentials to inundate victims with MFA push notifications until they become fatigued and press “yes,” allowing the attacker access to their account.
- Injection attacks—These consist of a cybercriminal exploiting the vulnerabilities in mobile applications and injecting untrusted data into an application that is then processed as commands or queries, altering the application’s functioning to serve the hacker’s bidding instead of the victim’s interests.
- Supply chain attacks—Hackers manipulate application functionality by exploiting vulnerabilities in the mobile app supply chain and embedding malicious code into the mobile application codebase during the development phase.
Mobile Security in the News
In recent years, numerous high-profile data breaches have affected millions of users globally, as depicted in figure 2.
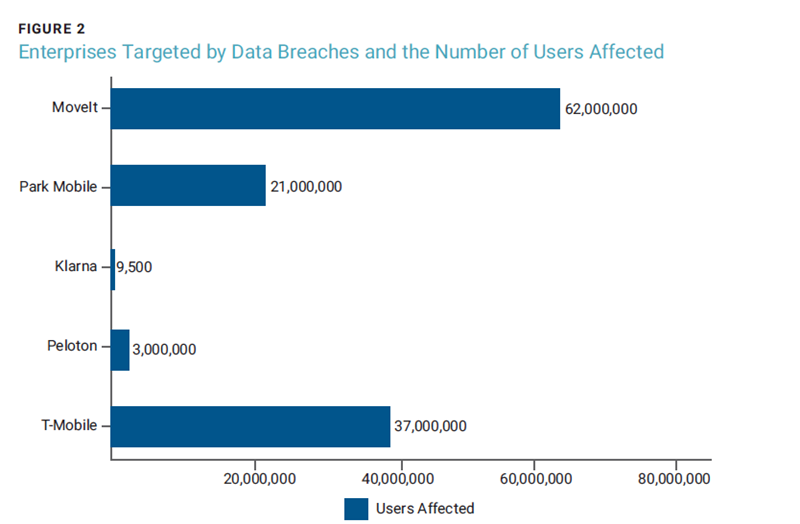
The MoveIt App is a file transfer service used by thousands of public and private organizations worldwide, from British Airways to Louisiana’s Office of Motor Vehicles. In May 2023, hackers exploited a vulnerability in the application and injected structured query language (SQL) commands to retrieve sensitive user data.8 Because of MoveIt’s massive reach, the attack affected more than 60,000,000 individuals and resulted in an estimated financial loss of nearly US$10 million.9
In early 2024, MFA bombing attacks were used to target Apple device users. Users were spammed by many password reset requests and then contacted by a scammer spoofing a legitimate Apple customer support number. Unlike many MFA bombing attacks, the perpetrators did not appear to have access to the victims’ credentials, leading experts to believe that they were instead taking advantage of the weaknesses in Apple’s MFA framework. This attack draws attention to the need to increase the strength of MFA authentication systems by limiting the number of MFA notifications sent within a certain time period, providing context to users for MFA notifications, and implementing methods such as risk-based authentication.10
Security researchers discovered that popular apps, including Android’s ShareIt app, have potentially exploitable security vulnerabilities, many of which remain unaddressed.11 In 2021, ParkMobile, a parking app, suffered a data breach that exposed the account information of 21 million users, which was later found for sale on the dark web. The same year, Klarna, an electronic payment app, unintentionally displayed user balances to other users. The issue resulted from erroneous caching due to human error.12 Exercise company Peloton had a leaky application programming interface (API) that could potentially expose sensitive user data. The underlying issue was insufficient user authentication for requests.13 A 2023 T-Mobile data breach, in which hackers accessed the personal data of 37 million customers, can also be traced back to a flawed API.14 These breaches, many of which would have been preventable with stronger security strategies, highlight the importance of dynamic security testing and proper developer training. They also emphasize the potentially disastrous effects of design vulnerabilities in mobile applications.
The Importance of Organizational Strategy and DevSecOps
Strong mobile security begins with a robust organizational strategy. To ensure the security of mobile applications, it is vital to have secure coding practices, vulnerability assessments, and penetration testing in place. A solid threat intelligence strategy is also essential to ensuring that organizations are informed about the rapidly evolving threat environment they face. Development security operations (DevSecOps), an approach that integrates security considerations and testing into every step of the software development process, utilizes automation to streamline and enhance security testing. Implementing a DevSecOps approach ensures that security concerns are considered during development, which is more effective and efficient than addressing security concerns after the software has already been developed. Developer training in standardized security best practices is a vital part of DevSecOps. It is also essential for users to know how to identify phishing, vishing, and similar attacks, as well as methods to secure their mobile devices.
Software Solutions to Improve Mobile Security
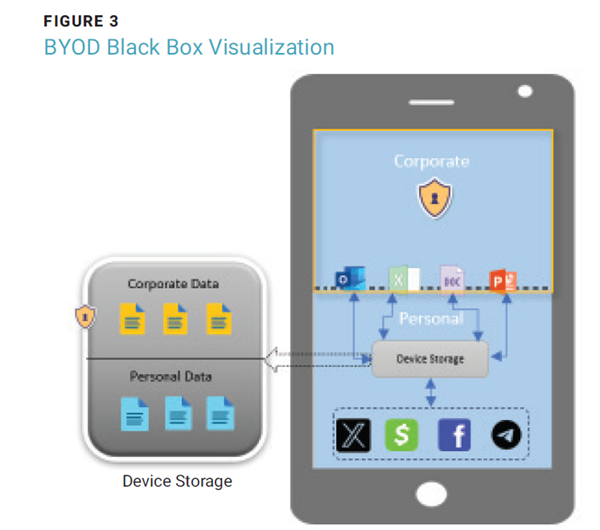
Mobile device management (MDM) software, which allows centralized device management, is critical in helping enforce security policies on devices across an organization. Additionally, if enterprises choose to allow staff to use personal devices for work purposes, it is vital for them to implement a BYOD black box to containerize organizational data and applications by implementing MDM solutions (figure 3). This can prevent organizational data from being corrupted if the device is compromised or stolen.
Protecting Applications from Malware and Proxy Attacks
Rooting and jailbreaking can make mobile devices more vulnerable to malware. Therefore, it is critical for organizational applications to include root and jailbreak detection capabilities. This prevents applications that use sensitive data from running on potentially compromised devices and putting that data at risk. Applications can also incorporate checks on data and Wi-Fi connections to ensure that a potentially malicious proxy is not present. Validating secure socket layer (SSL) certificates by implementing SSL pinning can further reduce the likelihood of man-in-the-middle attacks. Furthermore, strong user authentication controls and checks, along with input validation, are vital to ensure that organizational applications are only accessed by legitimate users and that the data entered into them is not malformed or harmful.
AI/ML Enhanced Cybersecurity
New technologies such as artificial intelligence (AI) and machine learning (ML) offer the potential to counter cyberattacks with a new level of sophistication and accuracy. ML-enabled behavior analytics can identify patterns in user behavior, creating a profile of typical activity and flagging anomalies. Regression models can be used to process information about previous cyberattacks and use this knowledge to predict future incidents and their impact. Furthermore, AI and ML enable the automation of routine security tasks, including log analysis, user authentication, and vulnerability assessments, enhancing the capability of security teams.15 By utilizing the analytical and predictive capabilities of AI and ML, enterprises can potentially prevent breaches before they occur.
How Enterprises Are Prioritizing Mobile Security
Multiple banks in Singapore have switched from sending their users one-time passcodes to having them authenticate their accounts with digital tokens on their mobile devices, adding a layer of protection against phishing attacks and showcasing the evolution of MFA.16 Meanwhile, the United States government has utilized an endpoint management software to safeguard employee devices while mandating MFA and zero-trust security models.17 In the healthcare sector, hospitals such as Boston Medical Center and Beebe Healthcare are using centralized device management, network monitoring, and employee training to head off potential breaches.18 These examples show that, around the world and across industries, enterprises are recognizing the need to evolve their cybersecurity strategies to maintain security as the computing environment shifts.
Conclusion
With the shift toward mobile, decentralized computing has increased the risk of infiltration for organizations in many sectors. Attacks on servers can cause significant financial and service losses and compromise consumer privacy. High-profile data breaches have resulted in millions of dollars in damages. Yet, organizations, users, and employees are not helpless against these attacks. It is the enterprise’s responsibility to ensure the security of the applications that run on mobile devices through technological solutions and strong DevSecOps practices. Equally vital is maintaining the device’s security, which is the obligation of the device’s owner. Regular security training ensures that employees take the necessary steps to secure their devices and identify phishing and Trojan horse attacks. By prioritizing security at all organizational levels, enterprises can ensure the safekeeping of sensitive data even as cyberthreats increase in number and sophistication.
Endnotes
1 Kaspersky, “Attacks on Mobile Devices Significantly Increase in 2023,” 26 February 2024, https://www.kaspersky.com/about/press-releases/attacks-on-mobile-devices-significantly-increase-in-2023
2 Pelchen, ; “Internet Usage Statistics in 2024,” Forbes, https://www.forbes.com/home-improvement/internet/internet-statistics/
3 Mckendrick, ; “Mobile Devices, More Than Cost Savings, Drive Cloud Computing: Survey,” Forbes, https://www.forbes.com/sites/joemckendrick/2011/12/07/mobile-devices-more-than-cost-savings-drive-cloud-computing-survey/
4 Dark Reading, “Data Loss, Leakage Top Cloud Security Concerns,” 17 July 2019, https://www.darkreading.com/cloud-security/data-loss-leakage-top-cloud-security-concerns
5 Gallo, K.; “Log4J Vulnerability Explained: What It Is and How to Fix It,” Built In, https://builtin.com/articles/log4j-vulerability-explained
6 Dahlqvist, ; Patel, M.; Rajko, A.; et al.; “Growing Opportunities in the Internet of Things,” McKinsey & Company, https://www.mckinsey.com/industries/private-capital/our-insights/growing-opportunities-in-the-internet-of-things
7 Montalbano, E.; “Sophisticated Vishing Campaigns Take World by Storm,” Dark Reading, 11 March 2024, https://www.darkreading.com/endpoint-security/sophisticated-vishing-campaigns-take-world-by-storm
8 Page, ; “The MOVEit Mass Hacks Hold a Valuable Lesson for the Software Industry,” TechCrunch, 11 August 2023, https://techcrunch.com/2023/08/11/moveit-mass-hacks-lessons/
9 Page, ; “MOVEit, the Biggest Hack of the Year, by the Numbers,” TechCrunch, 25 August 2023, https://techcrunch.com/2023/08/25/moveit-mass-hack-by-the-numbers/
10 Vijayan, ; Montalbano, E.; “Suspected MFA Bombing Attacks Target Apple iPhone Users,” Dark Reading, 28 March 2024, https://www.darkreading.com/cloud-security/mfa-bombing-attacks-target-apple-iphone-users
11 Khandelwal, S.; “Severe Flaws in SHAREit Android App Let Hackers Steal Your Files,” The Hacker News, 27 February 2019, https://thehackernews.com/2019/02/shareit-android-hacking.html
12 Reed, B.; “Mobile Application Security: 2021’s Breaches,” Dark Reading, 4 January 2022, https://www.darkreading.com/application-security/mobile-application-security-2021-s-breaches
13 “Peloton’s API Exposes Riders’ Private Data,” Security Magazine, 7 May 2021, https://www.securitymagazine.com/articles/95146-pelotons-api-exposes-riders-private-data
14 Franceschi-Bicchierai, ; “T-Mobile Says Hacker Accessed Personal Data of 37 Million Customers,” Tech Crunch, 19 January 2023, https://techcrunch.com/2023/01/19/t-mobile-data-breach/
15 Sarker, I.H.; “Machine Learning for Intelligent Data Analysis and Automation in Cybersecurity: Current and Future Prospects,” Annals of Data Science, 10, 2023, https://link.springer.com/article/10.1007/s40745-022-00444-2
16 Dark Reading, “Singapore Banks Ditch One-Time Passwords,” 15 July 2024, https://www.darkreading.com/endpoint-security/singapore-banks-ditch-one-time-passwords
17 Nichols, S.; “CISA Taps CrowdStrike for Endpoint Security,” 1 December 2021, https://www.techtarget.com/searchsecurity/news/252510346/CISA-taps-CrowdStrike-for-endpoint-security
18 Peterson, ; “How Healthcare Organizations Handle Endpoint Management,” HealthTech Magazine, 21 October 2019, https://healthtechmagazine.net/article/2019/10/how-healthcare-organizations-handle-endpoint-management
RACHIT GUPTA
Is a cybersecurity professional with more than 14 years of extensive experience in information security. Specializing in mobile and cloud security, he has adeptly safeguarded organizations against evolving digital threats. He can be reached at rachit28@gmail.com.
