It is not uncommon for enterprises to struggle with effectively managing their data and cybersecurity risk. These enterprises typically use manual processes and non-scalable tools that fail to provide holistic risk reporting and efficient workflow automation and notification functions. Choosing instead to manage cybersecurity risk using governance, risk, and compliance (GRC) technologies can help enterprises align IT activities with business goals, manage risk effectively, and comply with regulations.
Cybersecurity risk management has emerged as a critical facet of business operations in today’s digital landscape. With the continuous evolution of cyberthreats, enterprises must proactively fortify their defenses to safeguard sensitive data and infrastructure. 2024 has been particularly challenging for cybersecurity, with numerous entities falling victim to hacks and data breaches. As technology advances and next-generation artificial intelligence (AI) becomes more prevalent, the importance of prioritizing cybersecurity risk and compliance management cannot be overstated. Given recent cybersecurity trends, a focus on GRC can provide effective risk management with the use of industry-leading GRC technologies and an agile approach to implementing them.
Cybersecurity Trends
Based on recent key cybersecurity trends observed, it is possible to anticipate what lies ahead:
- Data breaches—Cybercriminals gain unauthorized access to organizational databases and exploit confidential client data for purposes of identity fraud or corporate espionage. According to an IBM survey,1 the average cost of a data breach exceeds US$4 million per incident, with ransomware being a primary culprit.
- MFA—A positive shift was noted in 2023, as many enterprises adopted multifactor authentication (MFA) as a more secure alternative to traditional single-step logins. MFA, incorporating elements such as passwords, biometrics, and hardware tokens, enhances security by requiring multiple forms of verification.
- Internet of Things (IoT)—With the proliferation of IoT devices, each connected device becomes a potential target for cyberattacks. Botnet attacks and distributed denial of service (DDoS) attacks are common threats in this domain, highlighting the importance of securing IoT ecosystems.
- AI and machine learning (ML)—Both defenders and attackers are using AI and ML technologies to analyze vast data sets. Although AI-driven defenses offer enhanced threat detection capabilities, malicious actors can exploit AI to execute sophisticated, tailored attacks.
- Deepfake technology—The rise of deepfake technology poses new challenges, as manipulated audio, video, and images can deceive individuals or facilitate identity theft. Bad actors may exploit to spread misinformation or extract sensitive information.
To effectively manage threats, enterprises must develop a strategy and leverage GRC tools.
Breaking Down Governance, Risk, and Compliance
For more than a decade, organizations have grappled with the formidable task of managing compliance and security challenges. Enterprises often find that just as they address one challenge, another promptly emerges. GRC is the perfect solution to break the silo of risk, compliance, and security management, and effectively handle these programs in a single enterprisewide tool. It provides a unique combination of governance (policies and procedures), risk management (all kinds of risk), and compliance management (adherence to standards and regulations) within one technology. This results in a risk management and reporting approach that enables senior leadership to make risk-based decisions.
Forming a GRC Program Strategy
To ensure the successful setup of a GRC program, there are several steps an enterprise can follow:
- Leadership buy-in—Before embarking on a GRC strategy, it is paramount to secure buy-in from organizational leadership. Establishing a core governance body dedicated to GRC initiatives ensures alignment with business objectives and facilitates roadmap development.
- Process streamlining—Enterprises should streamline risk, compliance, and cybersecurity processes to enhance efficiency and effectiveness. Aligning risk taxonomy and standardizing processes across business units can foster consistency and improve risk mitigation and reporting capabilities. Most enterprises emphasize the selection of a technology product without streamlining their complicated processes.
- Vendor selection—When selecting GRC vendors, enterprises should seek solutions that align with their unique requirements. However, it is equally important to evaluate and refine existing processes before implementing new tools to maximize their effectiveness. With the rapid growth of the risk and compliance landscape, many vendors have either established themselves or are gaining popularity. Archer Technologies, ServiceNow GRC, SAP GRC, IBM OpenPages, LogicGate, MetricStream, and Audit Board are well-known GRC vendors.
- Technology implementation—When a GRC vendor has been selected and set up within the enterprise, it is time to implement the compliance management and security modules of the GRC program:
- Compliance management module—This includes control assurance (documentation of controls and test procedures, design testing, operating effectiveness testing, control certification, and continuous monitoring). It also includes compliance with certain regulations and standards such as the Payment Card Industry Data Security Standard (PCI DSS), the US Health Insurance Portability and Accountability Act (HIPAA), US National Institute of Standards and Technology (NIST) requirements, International Organization for Standardization (ISO) standards, and various others. Additionally, it provides an ability to create ad hoc compliance-related assessments triggered at a set frequency (e.g., annually, semiannually, monthly).
- Security management module—This provides an ability to document and manage cybersecurity events and incidents and breach responses. Most of the leading GRC vendors have robust solutions for incident management, threat management, IT security and vulnerabilities management, and advanced reporting functions.
Foundational Elements of GRC
A GRC program cannot be successful without setting up the platform’s core foundational components.
These elements or applications play a crucial role in realizing the true power of the GRC platform. They facilitate holistic risk reporting and provide clear accountability for risk and issue remediation. The following components should be part of any GRC program, and they should be addressed prior to implementing risk, compliance, and security management use cases:
- Organizational hierarchy—Many GRC tools can either be integrated with the existing organizational hierarchy or create a hierarchy from scratch that includes operating company, divisions, subdivisions, business units, cost centers, and so on. This is essential to ensure accountability for risk, issues, action plans, and leadership reporting.
- Business and IT asset catalog—This includes linking existing applications, assets, devices, and facilities information with the GRC platform so that they can be used as metadata for risk and compliance reporting.
- Unified compliance library (optional)—This ensures that the enterprise’s business processes, risk factors, controls, and policies are documented, imported into the GRC platform, and updated regularly. This assists in performing risk and control assessments.
- Cybersecurity frameworks—Certain industry-leading cybersecurity frameworks can serve as guiding principles for enterprises seeking to strengthen their digital defenses. Enabling or integrating the following frameworks within the GRC program is recommended:
- ISO 27001—ISO 27001 delineates the criteria for establishing, executing, sustaining, and continually enhancing an information security management system and offers a structured method for overseeing confidential corporate data.
- NIST Cybersecurity Framework—The NIST Cybersecurity Framework (CSF) presents a risk-centric strategy for cybersecurity management by providing standards, recommendations, and optimal methodologies for addressing cybersecurity risk. This framework consists of five primary functions: identification, detection, protection, response, and recovery.
- PCI DSS—Targeted primarily at businesses handling cardholder data, PCI DSS provides a comprehensive framework to ensure the secure handling of payment card information. It delineates requirements for security management, policies, procedures, network architecture, software design, and additional protective measures.
- Risk methodology—A standard enterprisewide risk methodology should be adopted for consistent risk assessment and reporting. Establish consistent risk rating values across different business groups.
- Issues management—Establishing an enterprisewide issues management program helps document different types of issues (e.g., audit findings, security findings, assessment findings) and develop appropriate remediation or risk acceptance processes.
Figure 1 illustrates common GRC capabilities.
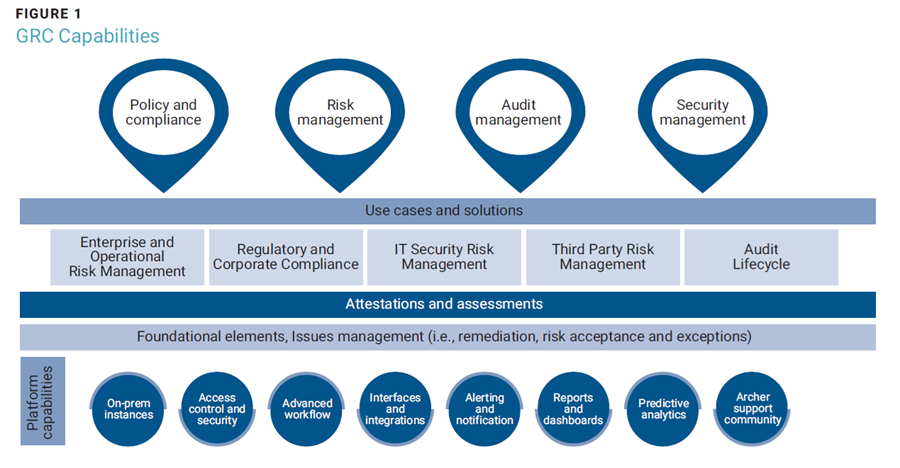
Cybersecurity Risk Management
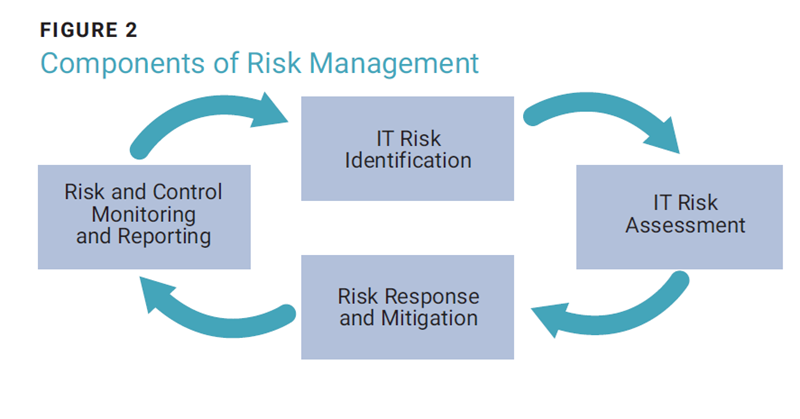
Once the prerequisite functions are in place, the subsequent step involves implementing the risk management module. Always review the risk management process and strive to enhance the process based on new trends and new threats. Innovation is key in managing cyberrisk. A typical risk management process comprises several steps (figure 2):
- Risk identification—The first step is to identify all cyberrisk impacting the enterprise. These threats will be assessed throughout the risk management life cycle. Failure to identify critical risk in a timely manner can lead to significant costs. The identified risk factors make their way into the risk register.
- Risk assessment—The next step is to assess the risk factors in the risk register and their potential effects. Several risk assessment techniques can be used, and most GRC tools support multiple risk assessment methodologies.
- Risk response and mitigation—This is the most critical phase of the risk management life cycle. Once the risk factors are identified and assessed, a response decision must be made, based on business objectives. Risk response options are risk acceptance, mitigation, transfer, and avoidance.
- Risk and control monitoring and reporting—Risk monitoring can provide a reasonable view of the risk environment. Key risk indicators (KRIs) and key performance indicators (KPIs) can be used to improve the process of continuous monitoring. Reporting is essential because it helps senior leadership pick the right approach to risk response.
When the cyberrisk management process has been established and defined, several corresponding actions can be taken to support the GRC application.
Risk Hierarchy and Risk Register
In the Risk Identification stage, risk identified from various sources is stored in a centralized system, forming a visual hierarchy. Risk hierarchy in GRC is utilized to capture enterprise risk and intermediate risk. Enterprise risk can vary, depending on the industry sector. The most common enterprise risk categories are cybersecurity, financial, operational, strategic, regulatory compliance, and reputational.
The risk register in a GRC tool is used to centrally document and manage actual risk that poses a threat to data or underlying processes. This risk is subjected to the risk assessment and mitigation process.
Risk Assessment
In the Risk Assessment phase, a risk assessment strategy and taxonomy are defined. When this is completed, risk assessment applications in the GRC system should be implemented. The selection of assessment techniques is based on business objectives and goals, choosing the assessment technique that best suits organizational needs. Based on enterprise goals and the risk landscape, either a top-down risk assessment or a bottom-up risk assessment can be conducted. Analyzing risk is an important part of the process. All modern GRC technologies can perform qualitative, quantitative, or semiquantitative risk assessment analysis.
Risk Quantification
Based on emerging cybertrends, many enterprises are moving away from qualitative risk assessment, which categorizes risk as low, medium, high, or critical. Instead, they are adopting quantitative methods that assign a dollar value to risk, which is more precise. Numerous risk quantification products in the market yield more tangible results by leveraging mathematical measurements and employing either Monte Carlo simulation methods or Bayesian approaches. RiskLens, Archer Insight, Ostrich Cyber Risk, Cybersaint, Kovrr, and MetricStream are risk quantification tools that integrate well with most GRC products.
The benefits of using risk quantification tools include long-term cost reduction. Quantifying risk enhances its reportability to leadership, facilitating more actionable insights and ultimately preventing long-term losses.
Action Plans or Risk Acceptance
In the Risk Response and Mitigation phase, the most common functionalities enabled in the GRC tool are the ability to create action plans (or risk mitigation plans) and risk acceptance. An action plan describes the mitigating steps to be taken to reduce risk. The plan should always be assigned an owner and a due date.
Risk acceptance is determined by senior leadership depending on the risk appetite of the organization.
Continuous Monitoring
As part of the last component of the risk management process, Risk and Control Monitoring and Reporting, enterprises can respond quickly to threats, incidents, and issues by continuously monitoring and assessing security risk and by testing controls at regular intervals. Periodic risk and control assessment helps the enterprise identify vulnerabilities and ensure compliance with various regulations.
GRC Implementation Methodology
GRC implementation can take a waterfall, agile, or hybrid approach (the latter has recently become popular). Before implementing any GRC module, it is important to prioritize business functions that are “must have” on day 1 to address critical business problems. The methodology illustrated in figure 3 can be used as a reference for GRC implementations that adopt the best of both waterfall and agile methodologies.
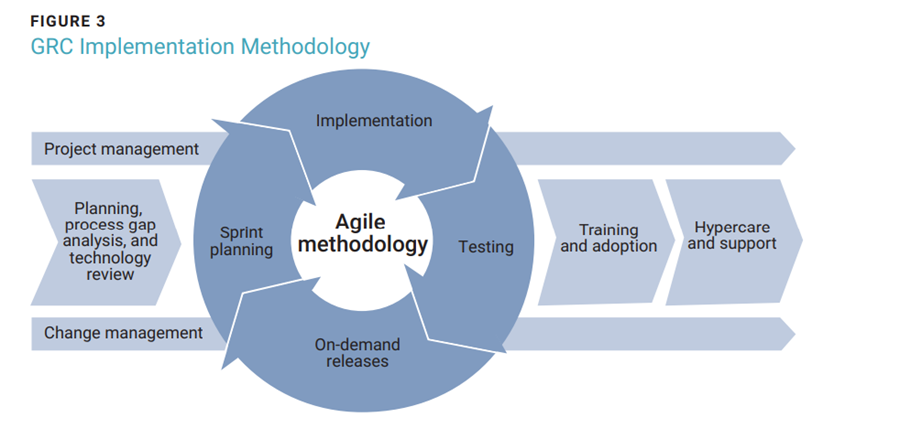
Several actions can be taken to successfully implement business functionality within a GRC tool:
- Planning and assessment of current circumstances
- Understand current in-scope processes and tools.
- Perform process gap analysis and provide recommendations.
- Understand data structures and confirm data to be imported into the GRC tool.
- Sprint planning
- Identify requirement-gathering, development, testing, deployment, and change management tasks.
- Conduct backlog refinement based on data availability and process priority.
- Implementation
- Organize tasks and teams per the sprint plan.
- Implement use cases per requirements and user stories.
- Prepare data import templates and conduct unit testing of the code.
- Testing
- Execute unit testing and functional testing for the configured use case.
- Execute integration and regression testing.
- Facilitate user acceptance testing and data validation.
- Perform defect resolution and data migration tasks.
- On-demand releases
- Release the configured use case module in production.
- Training and adoption
- Create training materials and job aids to facilitate effective training.
- Conduct train-the-trainer sessions and provide periodic refreshers.
- Hypercare support
- Perform post–go-live defect resolution for better adoption of the tool. This can facilitate the implementation of multiple modules simultaneously and get GRC functions and use cases up and running faster.
- Program and change management
- Dedicated program and project management provides clear visibility and accountability at every step of the implementation process.
- Clear communication, an effective change management strategy, and adequate training result in better adoption of the tool.
Conclusion
Cyberthreats are constantly evolving. As such, enterprises must adopt a proactive risk management mindset and a flexible approach. Through proactive risk management, organizations will be better prepared to prevent and mitigate potential threats and secure their data. The implementation of effective risk management can result in time, money, and resources being saved and reduce disruptions in day-to-day operations.
Proactive risk management requires organizations to define their risk management strategies, accounting for upside risk, outside risk, and downside risk. They must identify control gaps to drive control remediation and improvements. Collaboration among various departments also is essential to align strategies and business objectives and share information. It is critical to remember:
- Security should be everyone’s responsibility, and a risk management mindset should be ingrained in the culture.
- Always think of people, processes, technology, and data. Implementing a tool with complicated processes will result in less user adoption.
- Enhance the enterprise’s cybersecurity posture and mitigate emerging threats by adhering to these principles and leveraging GRC tools effectively.
- Ultimately, proactive risk management is essential to safeguard sensitive data and maintain business resilience in an increasingly interconnected world.
- Be innovative in managing cyberrisk. Cross-team communication is critical for effectively managing risk and compliance programs.
Endnotes
1 IBM, Cost of a Data Breach Report 2023, 2023
Hemang Mehta, CIPA
Is a governance, risk management, compliance management, and cybersecurity professional with more than 11 years of experience. He has helped Fortune 500 companies draft security risk management frameworks and transform their risk, compliance, and cybersecurity management programs. Currently, at Fidelity, he manages the risk portfolio for enterprise risk, cyberrisk, vendor risk, and audit issues, which allows the personal investing, financial institutional, and workspace investing groups at Fidelity to manage and report on risk more efficiently. His goal is to educate business groups about effective risk management processes and help them implement state-of-the-art GRC tools.



