Third-party risk is an evolving problem characterized by steadily increasing complexities. In recent years, there has been a tectonic shift in how enterprises operate. Remote working has forced organizations to extend their physical and logical boundaries, while geopolitical developments have forced them to examine supply chain resilience.
Threat actors are hunting for the wea kest supply chain links to exploit an organization. Disruptions—geopolitical developments, natural disasters, pandemics, cyberattacks—and risk factors that impact a supply chain ecosystem can have catastrophic consequences, creating a domino effect that extends to society at large.1
For example, a ransomware attack on a key supplier of automobile parts can result in a production shutdown that has consequences for many of its clients (i.e., car manufacturers), including production delays that ultimately impact potential car buyers. An even more serious scenario would be a ransomware attack on critical infrastructure—such as an energy supplier or a healthcare system—which might result in the loss of essential services or the development of conditions hazardous to public safety.
There are four steps that can help organizations develop a mature and fit-for-purpose third-party risk management program to mitigate emerging threats and build a resilient supply chain:
- Extend coverage of the third-party ecosystemwithin the risk management framework.
- Expand the risk horizon.
- Improve and contextualize risk assessments.
- Enhance strategic and operational reporting.
Extending Third-Party Ecosystem Coverage
Many organizations have made great strides in developing a robust risk management program covering their supply chain ecosystem. As the popular information security saying goes, “If you do not identify assets, you cannot secure them.” Similarly, if one does not know their third parties, they do not know what risk they are exposed to and, therefore, cannot determine what needs to be done.
Most mature third-party risk management programs focus on third parties that supply technology services or products crucial to the IT operations of an organization. Some examples in this category are vendors, IT product suppliers, outsourced technology providers, and helpdesk support staff.
The other category getting a lot of attention consists of third parties that access or process data to provide services to an organization or its customers. Because these third parties often deal with high volumes of critical information, they are lucrative from an attacker’s perspective.
However, only the most mature third-party risk management programs include supply chain third parties, even though an organization’s core business function depends on supply chain functionality and availability (e.g., for receipt of goods or services). This category is slowly gaining traction, and organizations are starting to consider their supply chain in the scope of third-party risk management.
Disruption to third parties in the supply chain can result in core business operations being affected and have a financial or reputational impact. Operational resilience and cyberincident response are the core expectations set for these third parties. Similarly, organizations should consider building their own resilience and continuity plans to mitigate the risk of supply chain third-party disruptions.
Figure 1 illustrates an example of third parties in technology services, data access, and supply chain categories for a health services provider.
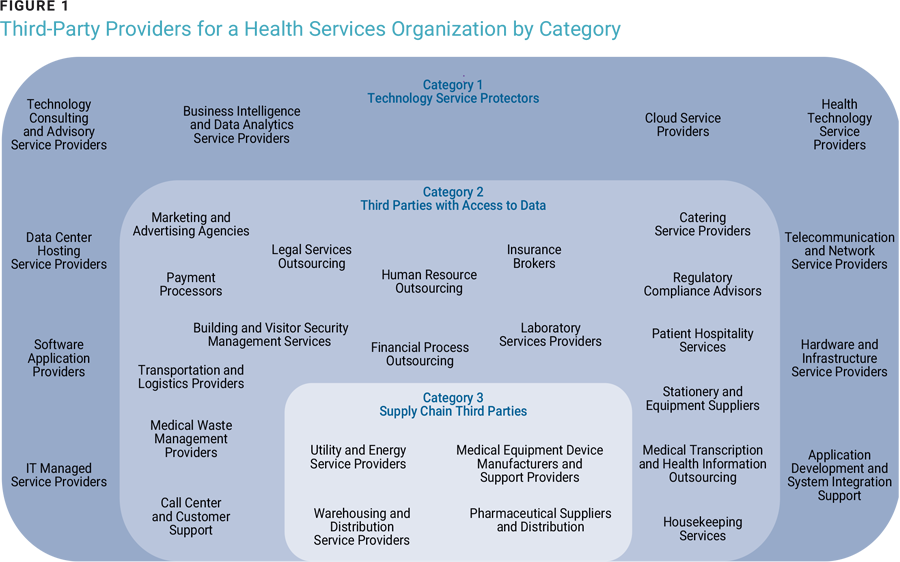
Identifying and tracking third parties within an organization is a critical activity that can be carried out effectively through policy enforcement and socialization. Technology tools can also be used to discover third parties. For example, cloud access security broker (CASB) solutions can help identify access to software as a service (SaaS) solutions an organization uses, and a simple reconciliation with the third-party inventory can help identify non-managed SaaS providers.2
Expanding the Risk Horizon
While the provision of critical products and services depends on key suppliers, it falls under the purview of the acquirer to assess and manage risk arising from the services delivered. Cybersecurity and data privacy are the more mature categories typically addressed in an organization’s third-party risk management program. While many organizations have mature processes to assess and mitigate these risk categories, a recent study3 found a 49% year-over-year increase in third-party data breaches or security incidents. There are quite a few risk domains an organization should consider evaluating as part of a third-party risk management program, as shown in figure 2.
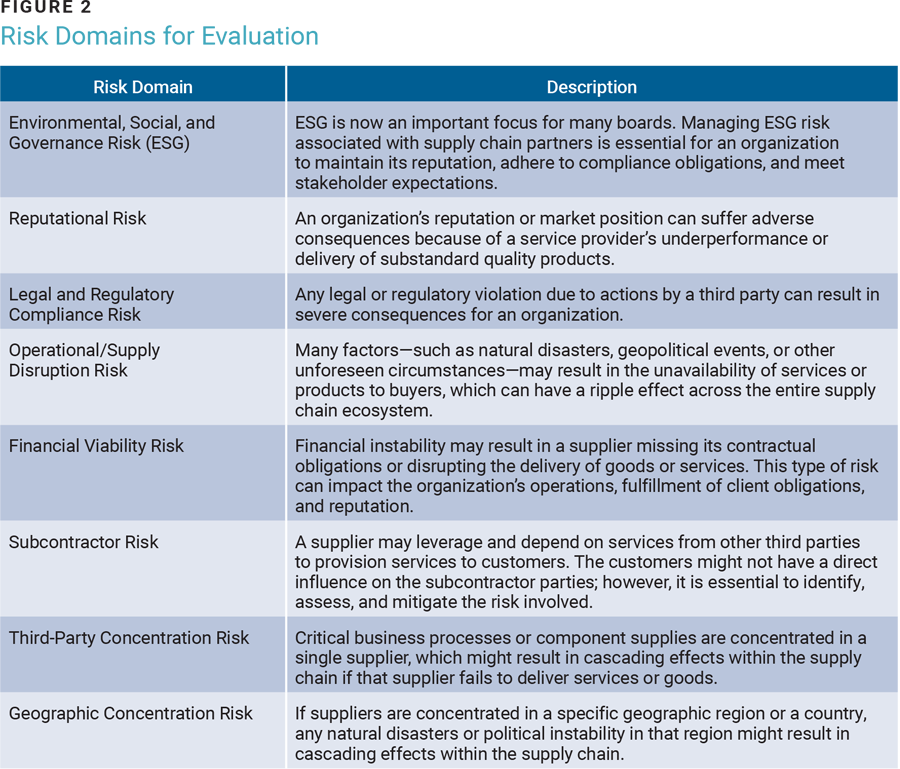
Not all third parties are going to expose an organization to the same risk, and risk factors are not equally applicable to the diverse services acquired. It is therefore critical to conduct a thorough analysis of the exposure covering the risk domains for each third-party relationship (figure 3). Organizations should also identify and implement contextualized controls commensurate with the risk exposure to ensure a sustainable relationship with the third party.
Disruption to third parties in the supply chain can result in core business operations being affected and have a financial or reputational impact. Operational resilience and cyberincident response are the core expectations set for these third parties.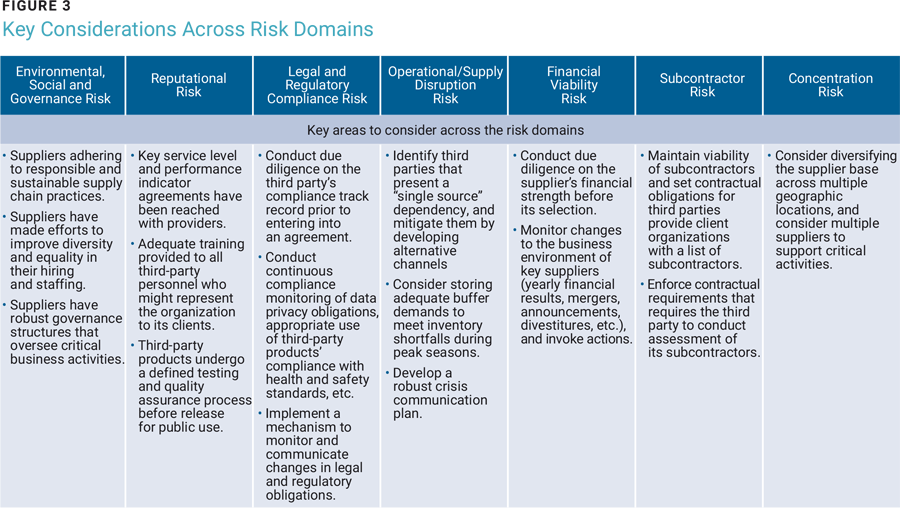
Improving Risk Assessment
Conducting risk assessments of third parties requires effort and should be commensurate with risk exposure. Assessment fatigue sets in when third parties are required to complete customized assessments at varying scales and levels of complexity for multiple clients. On the other hand, organizations are required to spend considerable staff hours engaging with third parties to review findings across the entire life cycle of assessments.
Assessments are resource-intensive processes. They cannot be eliminated, but the process can be made more efficient through the adoption of an approach that is fit-for-purpose and contextualized.
A hybrid assessment approach, which encompasses risk monitoring and control evaluation across various domains, offers increased assurance to an organization. Tailored to the service in question, this approach ensures a better return on investment for the effort required to assess third parties.Figure 4 shows assessment approaches with varying levels of effort required from the organization and the level of assurance each provides.
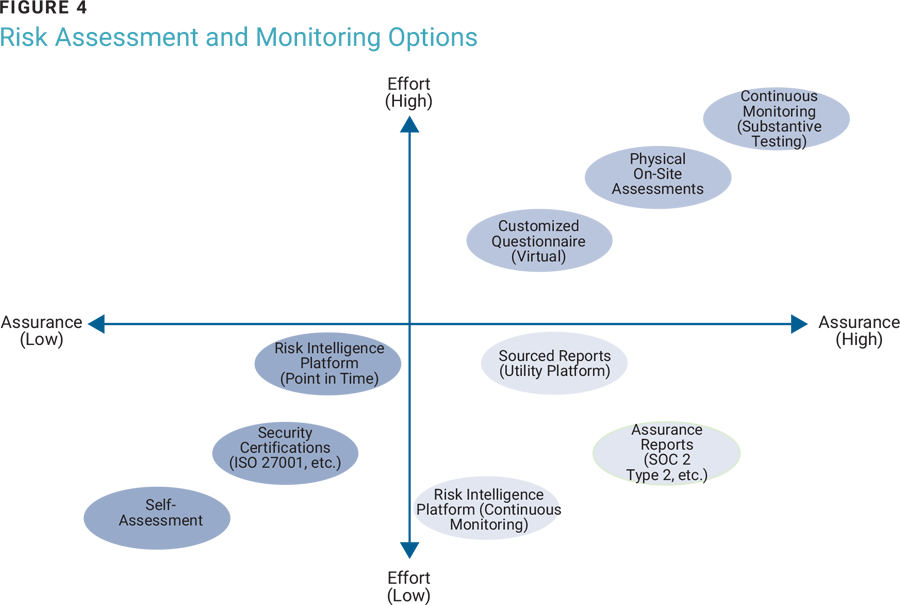
Broadly, third-party risk assessment approaches can be classified in two ways:
- Risk monitoring—Organizations can use information on the Internet to monitor a third party’s risk exposure. Open-source intelligence (OSINT)4 tools help organizations analyze publicly available data about third parties and take action if there is risk exposure. The reports are refreshed on a near real-time basis. Information such as adverse media reports, sanctions, and data leaks can be obtained by risk monitoring.
- Control evaluation—Questionnaire-driven control evaluation of third parties helps provide details about the design of internal controls and how effectively they operate. Questionnaire-driven assessments can be customized or aligned with industry standards such as the International Organization for Standardization (ISO) standard 27001, the US Payment Card Industry Data Security Standard (PCI DSS), etc.
A hybrid assessment approach, which encompasses risk monitoring and control evaluation across various domains, offers increased assurance to an organization. Tailored to the service in question, this approach ensures a better return on investment for the effort required to assess third parties.
Enhancing Strategic and Operational Reporting
As part of a third-party risk management program, enormous amounts of data are generated. What does an organization do with that data? Are required insights provided to key stakeholders?
Organizations are moving more toward data-driven insights. A mature third-party risk management program identifies what needs to be reported, at what intervals, and to whom (i.e., stakeholders). Effective insight-driven reporting can help an organization measure the success of its program, identify areas to focus on, and provide timely warning signs when action is required.
Some critical points related to data reporting are:
- Risk aggregation—A third party’s risk exposure can be obtained from multiple sources. Can all the information be aggregated and help present a holistic view of the third party’s risk exposure? Risk aggregation can take place across numerous risk domains. This includes information obtained from control assessments, risk monitoring platforms, inputs from service level agreement (SLA) measurements, and internal SOC teams. This information can be aggregated and made available to present a holistic view of a third party’s risk exposure.
- Operational insights—Risk assessments are resource-intensive and require planning. Key operational metrics—such as the number of risk assessments triggered over a period, assessment forecasts (i.e., number of assessments due over the next quarter), assessments completed on time versus those delayed or canceled, average response time from third parties—can provide insights to help plan and execute the assessments efficiently.
- Complete view of the supply chain ecosystem—Over time, organizations collect and store data about third parties, the services they provide, locations where they provide services, and their connections (i.e., subcontractors). This data can help the organization visualize the wider supply chain ecosystem, including its nth party relationships. Organizations can help map their critical business processes and suppliers. Similarly, concentration risk can be identified (both geographic concentration and concentration of services from a particular supplier).
Conclusion
The third-party ecosystem is becoming more complex and interconnected. While organizations continue to reap strategic advantages by utilizing third-party services, risk exposure increases concurrently. There is a growing emphasis on managing risk in the supply chain, and it is a strategic priority discussed at executive levels.
While overall maturity has increased in terms of managing cybersecurity risk, there is a growing need to manage other risk posed by third parties. Organizations must be agile and evolve their risk management programs quickly. A nimble and evolving third-party risk management program that matures and adapts to the changing risk landscape is the need of the hour.
Endnotes
1 Salgado, A.; “Top Disruptions That Shook Supply Chains in 2022,” SupplyChainDive, 21 December 2022, https://www.supplychaindive.com/news/top-supply-chain-disruptions-2022/639088/
2 Kirvan, P.; “How to Use a CASB to Manage Shadow IT,” TechTarget, 12 April 2023, https://www.techtarget.com/searchsecurity/tip/How-to-use-a-CASB-to-manage-shadow-IT
3 Prevalent, “Prevalent’s 2024 Third-Party Risk Management Study,” 8 May 2024, https://www.prevalent.net/news/prevalents-2024-third-party-risk-management-study/
4 OSINT Framework, https://osintframework.com/
VISVESHWAR RAMASUBRAMANIAM | CISA, CISM, CISSP, CCSP
Is a specialist in third-party risk management with more than 16 years of experience in information security consulting and management. He has more than a decade of global experience developing third-party risk management programs and conducting third-party risk assessments for organizations across the banking, financial services, insurance, technology, and oil and gas industries.
