The song “Any Road” by George Harrison is a good reminder of why a strategy is important. He sings “If you don’t know where you’re going, any road will take you there.”1 The lyrics serve as a stark reminder-perhaps even a warning-that if an organization does not establish a defined strategy, purpose, and objective, it will run into challenges down the line.
Emerging technologies such as artificial intelligence (AI), quantum computing, blockchain, Internet of Things (IoT), and 5G are changing the cybersecurity landscape, presenting both opportunities and challenges. For example, quantum computing has the potential to render traditional cryptographic standards obsolete. IoT and 5G expand attack surfaces and increase the complexity of securing interconnected devices. These advancements warrant a new approach to defining a cyberstrategy that is both comprehensive and flexible enough to remain relevant.
Defining a cybersecurity strategy requires knowledge and skill. Defining a cybersecurity strategy that is concise, clear, and aligned to business objectives requires cybersecurity expertise, accurate information about the organization’s risk profile, a solid understanding of the threat landscape, and awareness of the business context. These can be gained by examining the seven pillars of cyberresilience.
A cybersecurity strategy must first consider various strategic inputs (figure 1).
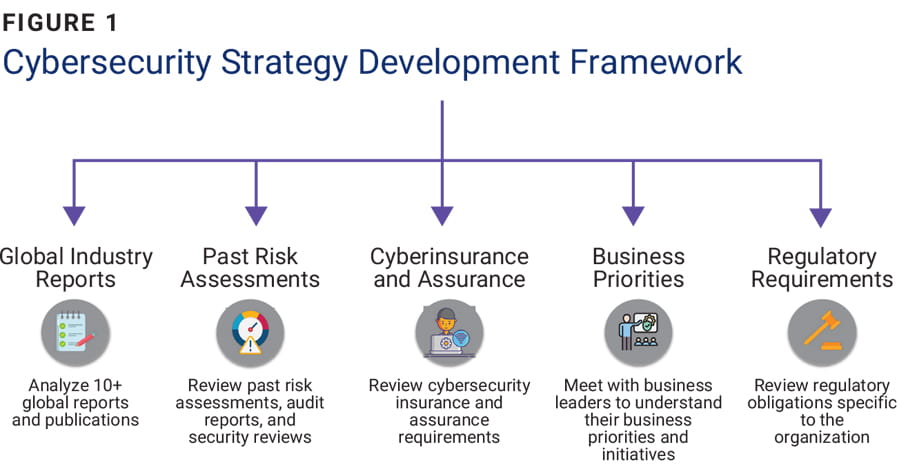
These inputs can help ensure that a cybersecurity strategy is aligned with the evolving threat landscape, unique business context, and regulatory obligations:
- Global industry reports—This includes research reports, vendor white papers, and academic research papers. A selection of relevant and reputable industry insights should be reviewed and analyzed. This will provide insights and an understanding of the global threat landscape.
- Past risk assessments—The current cybersecurity posture of the organization must drive the cybersecurity strategy. This insight can be gained by reviewing audit reports, penetration testing reports, security reviews, and vulnerability management reports from approximately the past eighteen months. Any past assessment that provides insight into the risk posture of the organization should be analyzed.
- Cyberinsurance and assurance requirements—Understanding the organization’s cyberinsurance requirements is important, as they may highlight gaps or areas of weakness based on what cyberinsurance providers are requesting. The output of this analysis should influence the cybersecurity strategy, as this has the potential to reduce risk and decrease the cyberinsurance premium.
- Business priorities—This is arguably the most important consideration when developing a cybersecurity strategy. An understanding of the organization’s priorities allows cybersecurity leaders to future-proof the cybersecurity strategy. For example, a municipality planning a smart city initiative will likely introduce operational technology (OT) and IoT devices, both of which will have cybersecurity implications that must be planned for. The main purpose of cybersecurity is to support business objectives, and therefore this input into the cybersecurity strategy is vital.
- Regulatory requirements—It is imperative to understand the regulatory obligations of the organization and translate that into cybersecurity requirements and ultimately initiatives or projects. For example, if the EU General Data Protection Regulation (GDPR),2 International Organization for Standardization/International Electrotechnical Commission (IEC) standard ISO/IEC 27001,3 Swift,4 or Payment Card Industry Data Security Standard (PCI DSS)5 apply to the organization, it will impact the cybersecurity budget, resource requirements, and tactical plans.
The Role of Cybersecurity Frameworks
It is imperative for cyberleaders to have a working knowledge of various cybersecurity frameworks to ensure that cyberstrategies align with industry and global best practices. Industry frameworks, such as the US National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF),6 ISO/IEC 27001,7 or PCI DSS consist of industry best practices and help organizations improve their security posture.8 By providing a common language for communication, frameworks allow organizations to benchmark their security programs against other organizations in the same industry. Certain frameworks provide a pathway to certification for organizations and individuals, validating an organization's cybersecurity capabilities and posture, and individuals’ skills.9
Guidelines to Develop a Robust Cybersecurity Strategy
Given the dynamic nature of technology and cyberthreats, a cybersecurity strategy requires ongoing reviews and updates, ideally twice a year. Frequent and regular reviews of the cybersecurity strategy enable organizations to adapt as emerging threats surface and attack methods evolve. Regulatory frameworks and compliance standards may also be updated, requiring organizations to adjust their strategies to remain compliant. Finally, shifts in the business strategy and direction may necessitate changes in the cybersecurity strategy to ensure alignment with organizational goals.
Frequent and regular reviews of the cybersecurity strategy enable organizations to adapt as emerging threats surface and attack methods evolve.The following guidelines prove useful in implementing a successful cybersecurity strategy:
- Adopt a consultative approach. Involve key stakeholders throughout the process. Begin with the cybersecurity team and gradually bring in other internal IT teams and business stakeholders. At all costs, avoid developing a strategy that has not been co-created with business leaders and the broader IT team. Developing a cybersecurity strategy in isolation can result in gaps, inefficiencies, and risk. Failing to consult business leaders and IT leaders may cause misalignment between cybersecurity initiatives and business objectives. This misalignment may result in resource misallocation, as business leaders may not fully understand how cybersecurity supports organizational goals. Failing to involve the broader IT team can result in critical IT dependencies being overlooked, potentially weakening the strategy. Additionally, the lack of stakeholder engagement often leads to reduced buy-in, which can hinder successful implementation of the cyberstrategy.
- Place people at the center of the cybersecurity strategy. Prioritize people development, user awareness and education, and foster a cyber-savvy culture within the organization.10
- Define a methodology to prioritize risk. To best illustrate this guideline, if there are 15 high-risk sources known to the organization, but there is only budget to address five of these sources, there should be a clear methodology in place for choosing the five risk sources that will be addressed. At a minimum, this approach should consider risk, the Pareto Principle,11 and a cost-benefit analysis.
- Limit vendor influence. While vendor roadmaps and insights may shape thinking and create awareness of certain risk factors and market trends, vendor strategies and roadmaps should not unduly influence the cybersecurity strategy. Industry experts and thought leaders who contribute to shaping the strategy should be trusted advisors without conflicts of interest, as opposed to current or potential technology and cybersecurity service providers.
- Focus on adding value. While it is important to consider regulations and risk factors when defining a cybersecurity strategy, demonstrating business value is key to engaging with the board of directors (BoD) and effectively communicating the impact and value of cybersecurity. Cyberleaders should prioritize highlighting the business value of their strategy, rather than solely focusing on risk mitigation.
The Foundational Building Blocks
While cyberattacks can occur at any time, building a comprehensive cyberresilience strategy can be time consuming. To address this, it is important to focus on security controls that deliver the most value and protection in the shortest amount of time. An effective cyberresilience strategy fosters trust with stakeholders by providing transparent insights into the current security posture, the target state, and the most cost-effective path to achieving the target state.
There is value in exploring the critical success factors for the effective implementation of a cybersecurity strategy. By prioritizing the following actions, one can ensure that the strategy aligns with business objectives, people are placed at the center, and sufficient resources are made available to proactively manage cyberthreats, mitigate risk, and add value:
- Ensure effective GRC. Effective governance, risk, and compliance (GRC) is the foundation of a robust cyberresilience strategy. Governance ensures that cybersecurity policies and projects align with the organization's objectives and supports accountability, effective decision making, and continuous improvement. Risk management minimizes the impact of cyberincidents by identifying, assessing, and mitigating potential threats proactively. Compliance ensures adherence to legal, regulatory, and industry standards, reducing the risk of financial penalties, negative impact on stakeholder trust, and reputational damage.
- Determine the active risk profile. Understanding the active risk profile is crucial when developing a cyberstrategy, as it provides a view of the current vulnerabilities and threats specific to the organization. This visibility allows for security measures to be tailored to address the sources of highest risk, thereby ensuring that resources are effectively allocated to protect the organization’s critical assets.
The Pillars
To build cyberresilient organizations, it is crucial to do the right things effectively. To achieve this, a solid foundation established through a GRC framework, coupled with a clear understanding of the current risk posture and exposure, is vital.
The importance of adopting a pillar-based approach is similar to construction: Just as the strength of a structure depends on its pillars, so too does the strength of cybersecurity resilience. In this context, figure 2 illustrates the seven pillars of cybersecurity resilience. When all pillars are effectively implemented, they enable organizations to thrive. However, if any pillar is missing, the entire program becomes ineffective, putting the entire organization at risk.
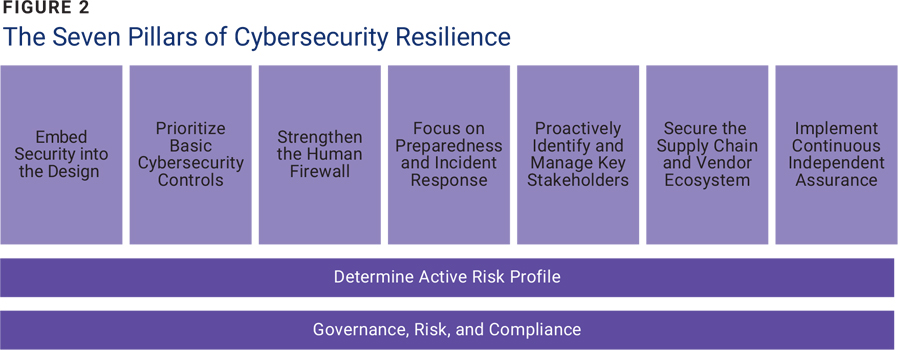
The seven pillars are:
- Embed security into the design. Security by design is a proactive approach that allows security controls to be embedded into the design of a solution. This allows vulnerabilities to be identified and addressed early in the process, saving time and resources compared to bolting security on at the end. By building security into the design, organizations can build resilient systems that are able to withstand cyberattacks and safeguard sensitive information, infrastructure, and stakeholder trust.12 People must be acknowledged as a critical part of the cybersecurity strategy. When adequately enabled, employees and suppliers can be an extension of the security team.
- Prioritize the basics. Regardless of organizational complexity, region, or regulatory environment, basic security controls are essential.13 All organizations, even those lacking a formal cybersecurity strategy, should:
- Maintain an up-to-date inventory of all critical assets, including data storage locations.
- Enforce multifactor authentication (MFA) for all critical applications and those facing the internet.
- Implement a patch, vulnerability, and configuration management program.
- Conduct regular penetration testing and configuration reviews to validate control effectiveness.
- Develop and test a documented incident response plan that is accessible to all incident responders.
- Establish an identity and access management capability that incorporates privileged access management
- Address human risk elements through a security awareness program with regular phishing simulations and tailored security messages.
- Strengthen the human firewall. People are constantly targeted by cybercriminals. There are several measures that will address human risk and improve resilience within the organization:14
- Encourage users to develop a skeptical attitude regarding unusual or urgent requests.
- Personalize awareness messages to equip employees to protect their personal information, home devices, and families.
- Enforce dual approval for all payment transactions.
- Urge employees to use strong passwords and not to reuse passwords across multiple platforms.
- Enforce MFA on all critical systems and encourage users to enable MFA on all personal accounts.15
- Test employee behavior and awareness through regular social simulated phishing campaigns.16
- Purchase all domains that closely resemble the organization to make it difficult for fraudsters to impersonate the official domains and websites.
- Focus on preparedness and incident response. It is widely accepted that data breaches and cyberattacks cannot be completely avoided. To this end, preparedness and incident response are crucial parts of a robust cybersecurity strategy. Being prepared allows for early detection and containment of security incidents and has the potential to minimize damage and downtime. A well-defined incident response plan includes roles, responsibilities, and detailed procedures required to ensure a coordinated and efficient response during cyberincidents. The main benefit of a defined response plan is the organization’s ability to quickly recover from cyberincidents with minimal disruption.17
- Identify and manage stakeholders. Effective stakeholder management is crucial for developing a robust cybersecurity strategy. By clearly communicating and educating each group, organizations can significantly increase the likelihood of successful cyberresilience plan implementation. Key stakeholders and their roles include:
- BoD and executive leadership—Educating the C-suite about the potential business impact presented by cyberthreats helps ensure informed decisions on security investments and resource allocation.
- IT management—As IT managers are responsible for executing the plan, their involvement is crucial for successful strategy implementation.
- Business leaders—Understanding how security measures impact operations and aligning them with business objectives fosters trust and integrates security into overall enterprise goals.
- Human resource (HR), finance, legal, and risk teams—These departments oversee areas vulnerable to cyberattacks. Their involvement ensures that the cyberstrategy is effective and aligned with broader business needs and goals.
- Supplier and partner ecosystem—Engaging with suppliers and partners helps identify potential risk, as they may connect to the organization’s network or handle data.
- Customers—Transparency about data security builds trust and loyalty, though care must be taken to avoid oversharing. Sharing sensitive details about organizational security controls can inadvertently aid malicious actors. For example, informing customers that a behavior analytics system is in place to protect against insider threats may build trust. However, it also has the potential to result in the disclosure of valuable information to cybercriminals, potentially helping them plan future attacks against the organization.
- Regulatory compliance—Adhering to regulatory requirements helps organizations avoid penalties and reputational harm.
By proactively engaging these stakeholders, organizations can create a strong, business-aligned cybersecurity strategy that has the support of key decision makers.
- Secure the supply chain. A strong cybersecurity strategy extends beyond internal controls and accounts for risk posed by third-party vendors and partners. The objective is to proactively manage and minimize the potential impact of a breach within their supply chain ecosystem. To adequately manage third-party risk, organizations can evaluate the security posture of third parties through security questionnaires, penetration testing, and ongoing monitoring. Contractual safeguards can further help to enforce security requirements and expectations. These may include data security clauses, incident response protocols, and audit rights. Continuous monitoring of third-party risk through automated tools that create technical cybersecurity ratings based on Open-Source Intelligence (OSINT), vulnerability assessments, and penetration testing, ensures that third parties maintain adequate security controls and identify emerging risk swiftly.
- Perform continuous independent assurance activities. Continuous independent assurance involves a combination of internal and external activities to constantly verify the effectiveness of security controls. Internal activities may include regular security reviews and assessments, vulnerability assessments, and penetration tests. External assessments involve the engagement of independent security audits or third-party certifications compared to industry standards. By continuously validating security controls, organizations can strengthen their risk posture and ensure ongoing control effectiveness.
By implementing these basic security controls, organizations can establish a strong security foundation before a comprehensive strategy is developed and approved.
People must be acknowledged as a critical part of the cybersecurity strategy. When adequately enabled, employees and suppliers can be an extension of the security team.
Barriers to Cyberresilience (and Possible Solutions)
To get the seven pillars in place, cyberleaders must overcome numerous barriers and pitfalls. While certain challenges are unavoidable, it is best to be aware of them early in order to formulate mitigation strategies. Common challenges cyberleaders may encounter when implementing cyberresilience strategies include:
- Lack of leadership commitment—Insufficient buy-in from senior management may result in inadequate resource allocation and a lack of prioritization for cyberinitiatives. To overcome this challenge, cyberleaders must clearly communicate the business risk of cyberattacks (e.g., service downtime, payment fraud, business email compromise). Business leaders will better understand risk that is communicated at the appropriate technical level. Relevant case studies and reminders of leadership's responsibilities will further aid management commitment.
- Failure to align cybersecurity with business objectives—In some organizations, cybersecurity may still be perceived as an IT function rather than a business enabler. This may lead to a misalignment with organizational goals. This pitfall can be avoided by establishing a cross-functional cybersecurity governance structure that includes business stakeholders. This approach ensures alignment with the business strategy and provides the cyber leadership team with the opportunity to educate, communicate, and reinforce the business value of cybersecurity.
- Neglecting the human factor—Failing to understand the role of humans (employees, contractors, suppliers) in risk posture can lead to an approach that is not human-centric, making it more likely that people will circumvent security controls. This challenge can be addressed through regular cybersecurity awareness training and phishing simulations. The overall objective is to foster a culture of security within the organization.
- Overreliance on technology—Relying solely on technology to solve business challenges can result in scenarios where critical aspects such as people and processes are neglected. To mitigate this issue, all technological solutions should follow a formal adoption process that includes defining processes and owners to manage and maintain the technology throughout its life cycle.
- Failure to prioritize—Attempting to address all security gaps at once could strain resources and result in risk exposure. To address this, a risk assessment must be conducted to determine the current risk profile. Cyber projects should be prioritized based on measurable risk to the organization, which should be regularly reassessed.
- Lack of incident readiness—Developing and deploying a cyberresilience strategy can take months or even years before its value is realized. However, cyberattacks wait for no one and can occur at any time. Being unprepared to respond to a cyberattack because the strategy is still being developed may undermine confidence in the cybersecurity function. To address this challenge, an incident response plan must be documented as soon as possible, with regular tabletop exercises conducted to test it. Communication channels for incident response must be established, along with clear roles, responsibilities, and contact information for all relevant stakeholders.
- Neglecting supply chain risk—Organizations may overlook risk associated with vendors, partners, and service providers, leaving critical gaps in their security posture. To mitigate this risk, cyberleaders must swiftly implement a third-party risk management framework that includes supplier categorization based on risk, cybersecurity contract clauses, and technology to monitor third parties on an ongoing basis.
- Emerging cyberthreats—Disruptive technologies, while providing numerous benefits, have also introduced new sources of risk:
- AI-powered cyberattacks—AI introduces new risk, as attackers develop more sophisticated attacks. AI-driven defense systems, where machine learning (ML) is integrated into defenses, and behavioral analytics are two methods organizations can deploy to prevent or detect anomalies or indicators of attack.
- Quantum attacks—Quantum computing presents an existential threat to traditional cryptography in that it could potentially render widely used encryption algorithms, such as RSA and elliptic curve cryptography (ECC) obsolete.18 To mitigate the associated risk, NIST has launched a global project to develop and standardize post-quantum cryptographic algorithms. This includes CRYSTALS-Kyber for key encapsulation and CRYSTALS-Dilithium for digital signatures.19
- Unmanageable vulnerability information—With the advancement of cybersecurity tools, a significant challenge has emerged: the excessive volume of information that cybersecurity teams must process to prioritize and mitigate vulnerabilities. The overwhelming number of vulnerabilities across diverse platforms and technology stacks makes it difficult to effectively prioritize effort.20 One approach to this problem is continuous threat exposure management (CTEM). CTEM provides a comprehensive framework that reduces exposure by unifying risk data and prioritizing remediation efforts based on real threats to critical assets. Unlike conventional tools, CTEM answers two critical questions: "What can attackers see?" and "What should we fix first?" By consolidating and enhancing data analysis, CTEM enables organizations to proactively manage risk and strengthen their overall security posture.
By acknowledging and addressing these common pitfalls early, organizations can significantly enhance their cyberresilience while minimizing the most critical risk.
Conclusion
Adapting to change is imperative. Consider this example: In 1996, a group set out to climb Mount Everest. They had the right equipment, and were well trained and fit, but on Everest there is a rule: If climbers do not reach the summit by a certain time of the day, they must abandon the attempt. This day, there was a traffic jam of sorts as four different expeditions all attempted to reach the summit, and these climbers did not reach the summit by the specified time. At this point, the hikers should have turned around, but they did not. The hikers reached the summit too late and had to climb down in the darkness and were caught unprepared by an unexpected storm. Sadly, they all died during the attempt.21
This tragedy offers a valuable lesson for cyber and enterprise leaders. Organizations often commit to a three-year plan or an eighteen-month road map, and then, as time passes, the business context may change or the threat landscape may evolve, and evidence will start to emerge that the current strategy is a bad idea. At that point, leaders should stop, reevaluate, and readjust the strategy. However, it is often difficult to admit that mistakes have been made, so security leaders may continue heading in the wrong direction. Regardless, if it becomes apparent that a cybersecurity strategy is no longer effective or appropriate, cyberleaders have a responsibility to rectify it.
It is therefore imperative not to view the cybersecurity strategy as a one-off exercise. The threat landscape is continuously evolving and therefore the cybersecurity strategy must be reviewed and updated regularly.
Endnotes
1 Harrison, G.; “Any Road,” Brainwashed, Dark Horse/EMI/Parlophone, 2002
2 Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation[or GDPR]) (OJ L 119, 4.5.2016, p. 1)
3 International Organization for Standardization, ISO/IEC 27001:2022—Information Security, Cybersecurity and Privacy Protection: Information Security Management Systems, 2022
4 Swift, “Swift Standards”
5 PCI Security Standards Council, PCI DSS: V4.0
6 National Institute of Standards and Technology, Cybersecurity Framework, USA
7 ISO, ISO/IEC 27001:2022
8 Valle, N.; “Cybersecurity Frameworks Explained: What They Are and Top Ones to Know,” InvGate, 16 August 2024
9 Ryerse, J.; “The Importance of a Cybersecurity Framework,” Security Magazine
10 Zongo, P.; The Five Anchors of Cyber Resilience: Why Some Enterprises Are Hacked Into Bankruptcy, While Others Easily Bounce Back, CISO Advisory, USA, 2018
11 Guy-Evans, O.; “Pareto Principle (The 80-20 Rule): Examples & More,” Simply Psychology, 21 September 2023
12 Cybersecurity and Infrastructure Security Agency, “Secure by Design,” USA
13 Center for Internet Security (CIS), “The 18 CIS Critical Security Controls,” USA
14 Zongo, The Five Anchors
15 Malik, Z.; “Eight Benefits of Multi-Factor Authentication (MFA),” 18 October 2021, Ping Identity Blog
16 Grimes, R.; “Simulated Phishing Tests Matter,” KnowBe4, 26 June 2024
17 Threat Intelligence, “A ComprehensiveGuide to Incident Response: What It Is, Process and Examples,” 29 May 2023
18 Harishankar, R.; Schaefer, J.; et al.; Security in the Quantum Computing Era, IBM, 2 December 2022
19 National Institute of Standards and Technology (NIST), “NIST Announces First Four Quantum-Resistant Cryptographic Algorithms,” USA, 5 July 2022
20 The Hacker News, “NIST Cybersecurity Framework (CSF) and CTEM – Better Together,” 5 September 2024
21 History, “Eight Climbers Die on Mt. Everest,” 13 November 2009
GRANT HUGHES | CISA, CISM, CDPSE, CASP, CCSK, CCSP, CEH, CIH, CISSP, SSCP
Is a head of cybersecurity at Engen Petroleum Ltd. He is a strategic thinker, thought leader, and public speaker with a background in security strategy, architecture, cybersecurity risk, and security operations. Hughes has delivered multiple keynotes and has more than 14 years of experience in IT, eight of which have been spent in information and cybersecurity. He is a trusted advisor certified in many disciplines within the information security domain. He can be contacted on LinkedIn.
