Historically, healthcare relied heavily on manual processes and paper-based records. However, like most industries, healthcare has adapted to new demands driven by population growth,1 an increase in the burden of disease,2 and a lack of resources for both.3 To meet these demands, digital technologies have been developed to improve the quality of clinical care and cost efficiency. As healthcare becomes increasingly interconnected through its various stakeholders (e.g., hospitals, clinics, pharmacies, third-party vendors), the attack surface for cybercriminals and the complexity of securing confidential information have also increased, introducing new cybersecurity challenges in ensuring patient safety and privacy. The sensitive information stored in health systems, coupled with inadequate security measures, makes the healthcare infrastructure an appealing target for a variety of cybercriminals, ranging from organized cybercrime groups to violent extremists. Globally, data-related breaches continue to be one of the main threats in the healthcare industry.
From January 2021 to March 2023, healthcare providers in the European Union, particularly hospitals, experienced frequent cyberattacks, with ransomware accounting for 54% of all cyberthreats in the health sector.4 Similarly, the frequency of cyberattacks on US hospitals and health systems more than doubled between 2016 and 2021.5
Research reveals that globally, the healthcare sector experienced a 22% year-on-year increase in cyberattacks.6 In Australia, there was an 84% rise in reported cyberincidents in the healthcare sector between 2019 and 2020 and 85 reported data breaches in the first half of 2021.7 Nationwide, the Australian healthcare sector reported the highest number of data breaches in the second half of 2022.8
The repercussions of cybersecurity negligence in any sector can include financial loss, operational disturbance, and reputational damage, but a cyberbreach in healthcare can also endanger patients. In the United States, the average ransom payment in the healthcare and public health (HPH) sector is US$131,000.9 But beyond the financial consequences, the potential impact on and damage to patient welfare are difficult or even impossible to remediate, and the collateral effects are incomprehensible. The challenge lies in balancing the benefits of digital transformation with the need to secure systems against potential cyberthreats to ensure patient safety.
Emerging Digital Healthcare Solutions
Digital transformation in healthcare is disruptive, but technologies such as artificial intelligence (AI), smart wearables, Internet of Things (IoT) devices, virtual care, and big data can accelerate outcomes by enhancing diagnosis, treatment decisions, selfcare, and professional competence while fostering a continuum of care and evidence-based knowledge.10
Advancements in technology are reshaping the way healthcare is delivered around the world.
AI
AI can enhance the efficiency and effectiveness of healthcare professionals. Currently, AI is deployed at the operational level in some healthcare institutions to optimize tasks by summarizing medical research and clinical notes. It is also being used as a plug-in with existing virtual assistants that manage a range of tasks, from scheduling doctor’s appointments to monitoring vitals.11 By taking over routine tasks that often occupy healthcare workers, AI can help alleviate persistent staffing shortages in hospitals and reduce the workload of the staff, therefore leading to better patient outcomes. Additionally, it will continue to play a growing role in diagnosing a wider range of diseases, particularly using advanced imaging techniques.
Smart Wearables
The rise of wearable tech in healthcare is changing the way care providers monitor health. Sensors can alert a diabetic patient that their blood sugar is getting low12 and smart contact lenses monitor intra-ocular pressure, an indicator of worsening Glaucoma.13 If these technologies are disrupted, the impact can be substantial to the consumer who is dependent on the technology. The adoption of this technology is expected to grow, with GrandviewResearch forecasting the global wearable tech market will have a compound annual growth rate of 14.6% from 2023 to 2030.14
IoT Devices
IoT devices are a revolutionary and rapidly evolving technology that has the promise to change the way healthcare is delivered. In healthcare, IoT is being used to improve patient care and outcomes and is often referred to as the Internet of Medical Things (IoMT). The revolution of IoMT provides new opportunities for remote monitoring, ambulance and hospital coordination, and inventory management of medication and hospital equipment.15
Virtual Healthcare
With the development of emerging digital technologies, unique opportunities have arisen to provide virtual care in the global healthcare system and improve healthcare delivery. For example, in Western Australia, a pilot program at an aged care residency utilizes discreet sensors and emergency alerts to allow remote doctors to monitor daily routines and care needs, enabling more informed care planning.16
Big Data
In healthcare, big data is analyzed to guide decision making, improve patient outcomes, and decrease healthcare costs. Some of the most common sources of big data in health care include biometric data including weight, pressure, and glucose levels; financial data; data from scientific research activities; and data provided by patients.17 This data offers a range of clinical benefits, such as improved diagnostics, patient treatment, and preventative medicine. Secondary benefits include cost reduction, population health support, and enhanced medical research.
Regulatory Environment
Healthcare systems must navigate a complex regulatory landscape, including the Health Insurance Portability and Accountability Act (HIPAA) in the United States, the General Data Protection Regulation (GDPR) in Europe, and the Privacy Act in Australia.
Health systems must navigate these complex legal and regulatory requirements while also ensuring compliance with data protection laws and industry standards. This requires significant resources and expertise, and noncompliance can result in severe penalties, legal liabilities, and reputational damage, as well as adverse consequences for patients. Breaches involving healthcare data can result in unauthorized access to, theft of, or disclosure of sensitive personally identifiable information (PII), medical records, billing details, and the like. Such breaches not only violate patient privacy but also expose individuals to identity theft and financial fraud. Recognizing the paramount significance of cybersecurity in healthcare, regulatory bodies worldwide are striving to implement measures aimed at strengthening data protection and privacy.
Ransomware Attacks
In May 2017, a dramatic cyberattack created a paradigm shift in healthcare cybercrime. England’s National Health Service (NHS) was hit by WannaCry, ransomware that exploited a known vulnerability in older, unpatched Windows operating systems.18 In addition to the NHS, WannaCry impacted more than 200,000 computers worldwide.19 The attack disrupted approximately 683 NHS or affiliated entities, canceling 19,000 patient appointments and costing £92 million.20
In 2024, the NHS was attacked again by a different cybercriminal organization known as INC Ransom. This time, an estimated 3 terabytes (TB) of clinical and financial information was stolen and dumped on the dark web.21 In the United States, attackers stole millions of health, insurance, and other sensitive records totaling 4 TB from Change Healthcare and sold them to the highest bidder in a dark web marketplace.22 The buyers reportedly paid US$22 million for the information.23
In March 2020, Brno University Hospital in Czechia experienced a ransomware attack, prompting its leadership to shut down the network, transfer patients to other nearby facilities, reschedule planned procedures, and transition staff to less efficient paper-based workflows. This incident occurred just as the country declared a state of emergency in response to the COVID-19 pandemic.24
In September 2022, Medibank, a major Australian healthcare organization, was the victim of a cyberattack resulting in the subsequent disclosure of private information belonging to an estimated 10 million customers (approximately 40% of the population of Australia). In addition to the immeasurable emotional and financial repercussions, the attack led to the shutdown of telecommunications, leaving Australians with limited or no access to the emergency services number. As a result, some citizens who were unable to access ambulances died.25
The COVID-19 pandemic triggered a surge in cyberincidents. In October 2020 the US government warned of an increase in ransomware attacks on hospitals. The exploitation of this crisis for financial gain was noteworthy: In 2018 the average decryption cost for a ransomware attack was US$5,000. However, in 2020, during the pandemic, these demands skyrocketed—ranging from US$200,000 to millions of dollars—as criminal groups realized the critical importance of healthcare systems.26
Health systems must navigate these complex legal and regulatory requirements while also ensuring compliance with data protection laws and industry standards.Managing Cyberhealth in Healthcare
Healthcare enterprises typically face several challenges when seeking to improve their cybersecurity and cyberresilience.
The Emerging Threat Landscape
In addition to patient data, smart IoT devices such as pacemakers, insulin pumps, and infusion pumps present attractive and vulnerable targets for hackers.27 IoT devices are notorious for their insufficient security measures, making them vulnerable to hacking, unauthorized access, and manipulation.28 The exploitation of vulnerabilities in these medical devices can lead to life-threatening outcomes for patients.
As the medical industry has digitally evolved, four elements of the cybercriminal ecosystem have synergized, directly impacting the digital transformation of healthcare and putting lives at risk: the initial access broker (IAB) market, malicious use of jailbroken large language models (LLMs), ransomware as a service (RaaS), and infostealers:
- IAB market—IABs generate income by gaining access to an enterprise’s network and selling remote access to other cybercriminals on the dark web.29 IABs gain access by stealing credentials, phishing, exploiting vulnerabilities, or loading remote-access malware by means of physical penetration.30 The IAB market thrives in the shadows, driven by anonymity and the illicit trade in access credentials. It is a dark economy operating parallel to the traditional economies that leverage digital vulnerabilities for profit.
- LLMs—Malicious generative AI, or jailbroken LLMs, have lowered the barrier to exploiting enterprises, including those in the healthcare sector.31 LLMs such as ChatGPT, Gemini, and others are commonly used to optimize work processes, find answers, and derive insights from large datasets. However, cybercriminals have adapted these technologies and developed their own versions such as WolfGPT, WormGPT, and FraudGPT.32 All cybercriminals need is intent; enabled by generative AI, they can launch sophisticated social engineering attacks and develop advanced malware with ease.
- RaaS—Parallel to existing software as a service (SaaS) models, RaaS is a subscription-based service that allows users to rent ransomware as if they were using a software license.33 These users, called ransomware affiliates, can launch a campaign against a vulnerable target with little to no programming knowledge. The ease of launching these types of attacks has lowered the barrier to entry for attackers, contributing to the year-on-year increase in losses related to ransomware attacks (figure 1).34
- Infostealers—There has been an uptrend in the distribution of information-stealing malware.35 This malware, which is deployed on endpoints unknown to the victim, collects and transmits sensitive data such as credentials, passwords, personal and enterprise information, and system information to a remote host. This information is sold on several dark web forums, with access brokered in the IAB market. Similar to the RaaS model, subscriptions to infostealers can be obtained, with software prices ranging from US$50 to more than US$1,000 per month.36
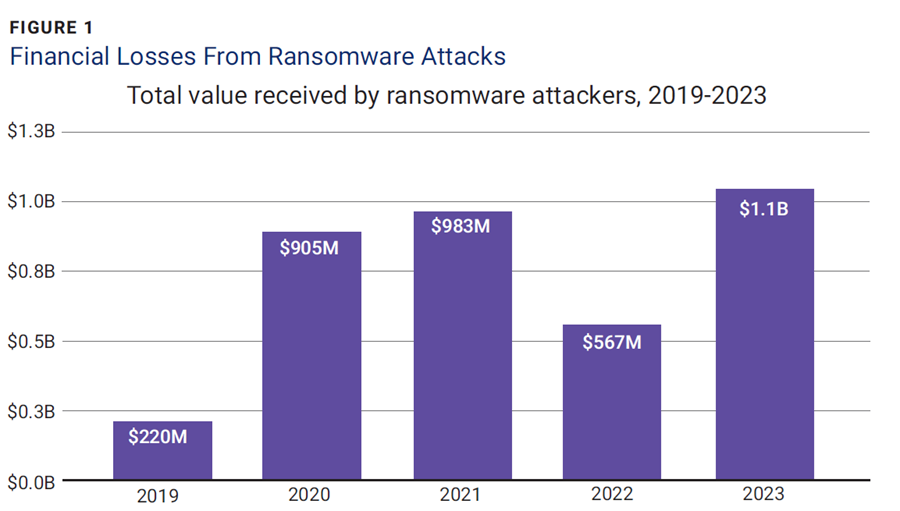
Source: Team, C.; “Ransomware Payments Exceed $1 Billion in 2023, Hitting Record High After 2022 Decline,” Chainalysis, 7 February 2024
These four threats can merge and cause damage that undermines the digital transformation of the healthcare industry. The breakdown of this emergent kill chain is as follows: Initial access is gained and sold by IABs (potentially with the help of infostealers), followed by the creation and deployment of specialized malware developed via jailbroken LLMs to assist in penetration, resulting in attacks against sensitive healthcare information facilitated by RaaS.
Even with technological protections in place, insider threats and human error continue to be notable cybersecurity problems in healthcare. Malicious insiders, such as disgruntled employees and rogue contractors, might purposefully undermine systems or pilfer sensitive data for their own benefit. Conversely, employees with good intentions may unintentionally succumb to phishing schemes, click on harmful links, or mishandle patient information, resulting in inadvertent data breaches and security lapses.
Advances in technology have provided a significant number of benefits, but the barrier to entry by cybercriminals has never been lower. If these trends continue, healthcare services will be left with a choice: Either include cybersecurity in the risk management framework or risk endangering lives.
Vulnerable Healthcare Systems
A variety of networked technology exists within healthcare systems, ranging from managed desktops and intensive care unit (ICU), electronic medical record (EMR), and protected health information (PHI) systems to insulin, infusion, and syringe pumps, endoscope cameras, imaging systems, and even defibrillators. These diverse elements pose interesting challenges that are not present in most industries.
One study identified EMR systems, wireless infusion pumps, endoscope cameras, and radiology information systems as possessing the greatest number of vulnerabilities.37 The primary causes of these vulnerabilities were identified as:
- Improper management of credentials and authentication or incorrect privilege management
- Out-of-bounds reading and writing causing data corruption, crash, or improper code execution
- Hard-coded credentials that allow an attacker to bypass the authentication process and communicate with external devices and systems
Figure 2 illustrates that the number of critical vulnerabilities tends to increase over time.
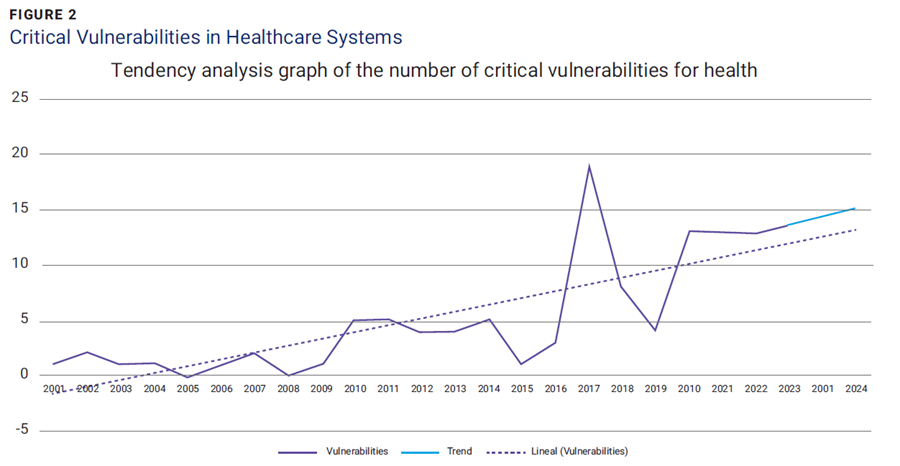
Source: Mejía-Granda, C.M.; Fernández-Alemán, J.L.; et al.; “Security Vulnerabilities in Healthcare: An Analysis of Medical Devices and Software,” Medical & Biological Engineering & Computing, vol. 62, iss. 1, 2024, p. 257-273, . Reprinted under a Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/).
Managing these vulnerabilities in conjunction with existing cybersecurity concerns can be overwhelming, which is why it is important to be brilliant at the basics: IT asset inventory, configuration management, and change management. First, it is imperative to understand which digital devices are in the organization and identify their access vectors (hardcoded or not). Second, it is imperative to establish a secure baseline, which in this case includes enforcing the principle of least privilege, minimizing access vectors, and implementing the principle of least functionality to ensure that devices operate only within their authorized parameters. Last, ensure that any changes to the baseline are captured and evaluated for additional assurance. An organizational security policy should be implemented that addresses these vulnerabilities directly by ensuring that digital healthcare devices known to contain these vulnerabilities are assessed before procurement and use.
By integrating these COBIT governance and management objectives into a holistic cybersecurity strategy, healthcare enterprises can ensure the security of patient data and the continuity of critical healthcare services.As the use of public cloud services rises, the data and resources of healthcare information systems will be shared with other systems to facilitate remote access, decision making, emergency response, and other aspects of healthcare. If these infrastructures are not configured and maintained properly, they will be highly vulnerable to data breaches, threatening the privacy and security of patients and healthcare systems alike.
Cyberresilience
Resilience, or the ability to recover quickly from adversity, is a key goal when establishing a stable digital architecture. The healthcare industry faces myriad challenges in achieving a resilient digital transformation, however, there are four primary issues:38
- Obsolete systems—Networked medical equipment and workstations frequently lack sufficient security measures, making them susceptible to exploitation. Worldwide, 83% of medical imaging devices depend on outdated technologies,39 significantly increasing their vulnerability. To build cyberresilience, healthcare leaders must prioritize system upgrades and updates and implement a consistent information and communications technology (ICT) strategy that ensures up-to-date and securely configured systems.
- Poor staff cyberliteracy—A substantial number of hospital compromises have originated from email-based attacks or insider threats. To cultivate a workforce that is knowledgeable about cybersecurity, healthcare enterprises must prioritize staff education and vigilance. Additionally, system and security administrators need to be aware of the unconventional vulnerabilities within the plethora of networked ICT systems and incorporate this awareness into their IT asset inventory, configuration management, and change management programs.
- Complex multiagency systems—Patients often engage with numerous healthcare institutions and providers, any of which might pose a security risk. Given this extensive healthcare network that ranges from government agencies to insurance providers to medical equipment manufacturers, sharing unsecured health data with third parties presents a notable danger. Health services should undertake extensive background checks and examine the reporting and data privacy policies of their end-to-end supply chains.
- Lack of strategic investment choices—When healthcare leaders confront strategic choices about investing in patient outcomes versus cybersecurity, the optimal approach is to prioritize both. Effective patient care cannot be achieved without guaranteeing patient confidentiality and safety, data integrity, and system security. As a result, executives are increasingly recognizing that cybersecurity is an essential component of healthcare delivery.40
Achieving Security Outcomes With COBIT
COBIT® 2019 outlines a series of governance and management objectives that can be implemented to govern healthcare enterprises’ security concerns.41 Key COBIT objectives include:
- APO12 Managed Risk—Ensures that vulnerabilities across access points, networked technologies, and public cloud services are methodically identified and mitigated, reducing overall risk
- DSS05 Managed Security Services—Improves security measures, from network security to protection against malicious software, ensuring that security controls are effective against emerging threats
- APO13 Managed Security and APO07 Managed Human Resources—When integrated, improves credential management practices and enhances the staff’s cyberliteracy, reducing the risk of insider threats and human error
- BAI07 Managed IT Change Acceptance and Transitioning—Assures that system changes such as updates are securely implemented, protecting against new vulnerabilities and system outages
- APO09 Managed Service Agreements—Assures that third-party suppliers and vendors adhere to security standards, mitigating risk within complex multiagency systems
- APO06 Managed Budget and Costs—Balances financial investments through cost-benefit analysis, ensuring that both patient care and cybersecurity receive sufficient funding to support resilient healthcare delivery
By integrating these COBIT governance and management objectives into a holistic cybersecurity strategy, healthcare enterprises can ensure the security of patient data and the continuity of critical healthcare services.
Conclusion
Shedding light on current and emerging cybersecurity threats facing the healthcare industry helps policymakers, cybersecurity professionals, and healthcare providers consider risk when integrating technology into the fabric of the digital healthcare ecosystem. Addressing cybersecurity issues in healthcare requires a multifaceted approach that integrates technological advancements, regulatory adherence, and human vigilance. Healthcare entities must invest in a robust cybersecurity infrastructure, institute comprehensive training for staff, and cultivate a culture of security awareness and responsibility. Collaboration among industry stakeholders, governmental bodies, and cybersecurity specialists is imperative for crafting proactive protection mechanisms and safeguarding against the improper disclosure, alteration, or unavailability of patient data amidst the ever-evolving digital healthcare landscape.
Endnotes
1 United Nations, “Global Issues, Population”
2 Ritchie, H.; Roser, M.; et al.; “Burden of Disease,” Our World in Data, February 2024
3 Southwick, R.; “Hospitals Continue to Wrestle With Staffing Shortage,” Chief HealthCare Executive, 25 October 2023; Huntley, K.; Jongenelis, M.; et al.; “Our Duty of Care to Those Who Care,” University of Melbourne, Australia, 24 November 2023
4 European Union Agency for Cybersecurity, “Checking Up on Health: Ransomware Accounts for 54% of Cybersecurity Threats,” European Union, 5 July 2023
5 Neprash, H. T.; McGlave, C.; et al.; “Trends in Ransomware Attacks on US Hospitals, Clinics, and Other Health Care Delivery Organizations, 2016–2021,” JAMA Health Forum, vol. 3, iss. 12, 2022, p. e224873
6 Check Point Research, “Global Cyberattacks Continue to Rise With Africa and APAC Suffering Most,” 27 April 2023
7 Industrial Cyber, “Cyber Threats in Australian Healthcare Sector Face Increase in Complexity and Volume, Following Global Patterns,” 8 March 2023
8 Office of the Australian Information Commissioner, Notifiable Data Breaches Report, Australia, 8 March 2023
9 US Department of Health and Human Services, Health Sector Cybersecurity Coordination Center, “Ransomware Trends 2021,” USA, 6 March 2021
10 World Health Organization, Global Strategy on Digital Health 2020-2025, 2021
11 Alowais, S.A.; Alghamdi, S.S.; et al.; “Revolutionizing Healthcare: The Role of Artificial Intelligence in Clinical Practice,” BMC Medical Education, 22 September 2023
12 National Diabetes Services Scheme, “Continuous and Flash Glucose Monitoring”
13 Kazanskiy, N.L.; Khonina, S.N.; et al.; ”Smart Contact Lenses-A Step Towards Non-Invasive Continuous Eye Health Monitoring,” Biosensors (Basel), vol. 13, iss. 10, 2023
14 GrandViewResearch, Wearable Technology Market Size, Share & Trends Analysis Report By Product (Head & Eyewear, Wristwear), By Application (Consumer Electronics, Healthcare), By Region (Asia Pacific, Europe), And Segment Forecasts, 2023 – 2030
15 Parihar, A.; Prajapati, J.B.; et al.; “Role of IOT in Healthcare: Applications, Security & Privacy Concerns,” Intelligent Pharmacy, vol. 2, iss. 5, 2024
16 Government of Western Australia WA Country Health Service, “Virtual Care Helping Country Aged Care Residents Live Independently,” Australia, 21 October 2024
17 Batko, K.; Slęzak, A.; “The Use of Big Data Analytics in Healthcare,” Journal of Big Data, vol. 9, iss. 1, 2022
18 Kaspersky, “What Is WannaCry Ransomware? Ransomware WannaCry: All You Need to Know”
19 Collier, R.; “NHS Ransomware Attack Spreads Worldwide,” Canadian Medical Association Journal (CMAJ), 5 June 2017
20 Smart, W.; “Lessons Learned: Review of the WannaCry Ransomware Cyber Attack,” UK Department of Health and Social Care, 2018
21 Hollingworth, D.; “Patient Data Published Following INC Ransom Attack on NHS Dumfries and Galloway,” Cyberdaily, 9 May 2024
22 Cluley, G.; “Change Healthcare Data for Sale on Dark Web as Fallout From Ransomware Attack Spirals out of Control,” Bitdefender, 19 April 2024
23 Greenberg, A.; “Hackers Behind the Change Healthcare Ransomware Attack Just Received a $22 Million Payment,” Wired, 4 March 2024
24 Porter, S.; “Cyberattack on Czech Hospital Forces Tech Shutdown During Coronavirus Outbreak,” HealthCare IT News, 19 March 2020
25 Kost, E.; “What Caused the Medibank Data Breach?,” Upguard, 16 September 2024
26 Newman, L.H.; “Ransomware Hits Dozens of Hospitals in an Unprecedented Wave,” Wired, 29 October 2020
27 Pallardy, R.; “The Unique Cyber Vulnerabilities of Medical Devices,” Information Week, 15 November 2023
28 Williams, P.; Dutta, I.K.; et al.; “A Survey on Security in Internet of Things With a Focus on the Impact of Emerging Technologies,” Internet of Things, vol. 19, 2022, p. 100564
29 Cyber Threat Intelligence Team, “Initial Access Brokers: How They’re Changing Cybercrime,” Center for Internet Security
30 Dutta, T.S.; “Hackers Released New Black Hat AI Tools XXXGPT and Wolf GPT,” Cybersecurity News, 1 August 2023
31 National Cyber Security Centre, “The Near-Term Impact of AI on the Cyber Threat,” United Kingdom, 24 January 2024, US Department of Health and Human Services, Health Sector Cybersecurity Coordination Center, AI-Augmented Phishing and the Threat to the Health Sector, USA, 26 October 2023
32 Dutta, “Hackers Released New Black Hat”; Tosin, J.; “WormGPT, WolfGPT, FraudGPT and the Weaponization of Generative AI,” Medium, 3 October 2023
33 Roncato, C.; “Five Cybercriminal Entities Sell Access to 2,300 Networks,” Watchguard, 5 April 2023
34 Palo Alto Networks, “What Is Ransomware as a Service (RaaS)?”
35 Verton, D.; “New Study by Uptycs Exposes Alarming Rise in Infostealers Dangers,” Uptycs, 23 August 2023
36 Counter Threat Unit Research Team, “The Growing Threat From Infostealers,” Secureworks, 16 May 2023
37 Mejía-Granda, C.M.; Fernández-Alemán, J.L.; et al.; “Security Vulnerabilities in Healthcare: An Analysis of Medical Devices and Software,” Medical & Biological Engineering & Computing, vol. 62, iss. 1, 2024, p. 257-273
38 Arora, R.; Smart, J.; et al.; “Proven Precautions to Help Protect Health Organisations and Patients From Cyberattacks,” PwC Australia, 12 April 2022
39 Newman, L.H.; “Most Medical Imaging Devices Run Outdated Operating Systems,” Wired, 10 March 2020
40 Arora; “Proven Precautions”
41 ISACA®, “COBIT 2019 Framework: Governance and Management Objectives,” 2018
SAMUEL ROMANOV | CISM, CRISC, CISA, CCSP, CGRC, CISSP, IRAP
Is a cybersecurity professional specializing in governance, risk, and compliance across enterprise organizations, healthcare institutions, and not-for-profits. As the owner and director of Cornerstone Technology Solutions, Romanov primarily provides cybersecurity strategy, risk management, and security assessment/audit services. Furthermore, he has a passion for educating the public about cyberthreats and mentoring the next wave of cyberprofessionals through his social media channels, @cybersecurity.sam.
MARLIEN VARNFIELD | PH.D
Is a principal research scientist at CSIRO and the group leader of digital therapeutics and care at the Australian eHealth Research Centre. Varnfield specializes in developing digital health innovations for chronic illnesses and vulnerable populations. Her significant contributions include the commercialization of a groundbreaking cardiac rehabilitation platform and the development of a digital management system for gestational diabetes, which has become standard care in several health services. Varnfield's work is widely published, with articles published in Diabetic Medicine and Digital Health, highlighting her research on mobile health applications and their impact on patient care. A respected leader in her field, she is a frequent keynote speaker at major international conferences.



