The security architectures and methods of maintaining service levels in use today were created in a world that no longer exists. These paradigms were developed when IT assets could be protected by guards, locks, walls, and sensors. It was possible to identify the digital pathways into, and out of, those assets. Enterprises were largely self-contained, at least from an IT perspective. When there was an outage, it rarely rippled through an ecosystem. The heavy reliance on IT and interdependencies that are common today did not exist.
In today's world, IT is pervasive. The World Economic Forum (WEF) estimates that 60% of the global domestic product is digital.1 More than half of the assets driving corporate valuations are intangible.2 The average person has more data storage and computing power on their phone than was needed to land on the moon and return to Earth. 3
Not too long ago, cyberincidents were not prevalent. But from the daily news cycle, it is obvious that things have changed. Retailers have been hacked through their heating, ventilation, and air conditioning (HVAC) vendors.4 Resorts have been hacked through the vendors who maintain their aquariums.5
It is undeniable that incidents will happen. They may come from unexpected places or manifest in debilitating ways. But with customers and business partners that consider digital trust to be just as important as price and delivery time, modern enterprises must meet the need for resilience.
What Is Resilience?
The US National Institute of Standards and Technology (NIST) defines resilience as "the ability to prepare for and adapt to changing conditions and withstand and recover rapidly from disruption."6 The International Organization for Standardization (ISO) has a similar definition: "Resilience is the ability of an organization to respond and adapt to change. Resilience enables organizations to anticipate and respond to threats and opportunities arising from sudden or gradual changes in their internal and external context."7
Simply put, resilience is about maintaining viability amidst adversity. That means aligning technology strategy with business strategy and operations. It means moving away from technology to mitigate cyberrisk, and this requires collaboration among technology, people, processes, and enterprises.Simply put, resilience is about maintaining viability amidst adversity. That means aligning technology strategy with business strategy and operations. It means moving away from technology to mitigate cyberrisk, and this requires collaboration among technology, people, processes, and enterprises. Resilience is evidence of an organization's acceptance that incidents are going to happen, with the goal of detecting them faster and recovering more quickly. Because no enterprise has unlimited resources, business services must be prioritized, recognizing that they are part of an ecosystem with obligations to customers, vendors, and suppliers while also understanding that the viability of those services depends on outsiders.
The shift toward resilience is real. In the United States, the Office of the National Cyber Director (ONCD) published a national cybersecurity strategy.8 The European Union (EU) passed a directive on cybersecurity.9 Both are heavily focused on resilience.
Resilience has a unique role where the digital world meets the physical world-industrial control systems, operational technology, water, power, and energy. In the United States, the President's Council of Advisors on Sciences and Technology (PCAST) has a working group dedicated to resilience, and it is leveraging the principles contained in the Operational Resilience Framework (ORF).10
What Is Digital Trust?
ISACA® defines digital trust as confidence in the integrity of the relationships, interactions, and transactions among providers and consumers within an associated digital ecosystem. This includes the ability of people, organizations, processes, information, and technology to create and maintain a trustworthy digital world.11
Simply put, resilience promotes digital trust by instilling confidence in stakeholders of all kinds- users, customers, business partners, and investors.
Customers, vendors, suppliers, and partners make decisions based on digital trust. A September 2022 McKinsey survey12 of more than 1,300 business leaders and 3,000 consumers demonstrated that establishing trust in products (e.g., artificial intelligence [AI], digital technologies, data) promotes growth rates of at least 10% and has a positive impact on both the top and bottom lines. The study also found that 52% of business-to-business (B2B) transactions and 40% of consumer purchases were halted when digital trust was violated. Specifically:
- Of the respondents, 87% consider trustworthiness and data protection nearly as important as price.
- Of the respondents, 94% consider trustworthiness and data protection as important as delivery time.
- Of the respondents, 53% of consumers buy only from enterprises recognized for their digital trust.
- Of the respondents, 65% of organizations buy only from other organizations recognized for their digital trust.
Disaster Recovery, Business Continuity, and Resilience
For many years, disaster recovery (DR) and business continuity (BC) were treated separately: DR recovered IT, and BC recovered the business. Both treated operations as either on or off. Most enterprises were focused on single hazards, usually physical events such as natural disasters. Many plans did not accommodate interdependencies with partners, suppliers, vendors in the supply chain, or external service providers such as cloud service providers.
Modern enterprises are so dependent on technology that one cannot exist without the other. Therefore, ensuring the resilience of one requires ensuring the resilience of the other. Resilience recognizes the paradigm shift and modifies the merger of DR and BC by:
- Focusing on the continuity of critical services, even at reduced levels
- Recognizing all hazards
- Acknowledging that enterprises do not stand alone: Downstream providers impact the delivery of service, and the lack of service delivery causes ripples upstream
Resilience augments existing indicators and metrics to match the resilience paradigm. The ORF is a highly comprehensive source for understanding specifics.13 Developed by the Business Resilience Council (BRC) and sponsored by the Global Resilience Federation (GRF), the ORF is the most developed resilience framework available in the United States.14 It is the result of three years of development by more than 100 organizations. The ORF has been adopted by regulators, with some of its key elements included in the Report to the President Strategy forCyber-Physical Resilience: Fortifying Our Critical Infrastructure or a Digital World15 and "Joint Statement to Leaders from the United States' President's Council of Advisors on Science and Technology and United Kingdom's Prime Minister's Council for Science and Technology."16
The ORF consists of 37 rules grouped into seven domains. A maturity model is attached to the framework to craft an enterprise's resilience journey. Scores are presented numerically and visually in the form of a spider diagram. The ORF is outcome-based, not prescriptive.
Resilience and Business Alignment
Resilience inextricably links technology with business. Given the complexity of modern enterprise ecosystems, it can be mind-numbing to ferret out the relationships between an enterprise and its technology, but it is essential for building resilience.
Resilience is about remaining viable amidst adversity. Decisions must be made about priorities (e.g., service A is more important than service B). To protect, detect, and recover those services it must be understood what technology components, people, and processes are required to keep services viable. Resilience, being a business-driven approach, forces ongoing discussions with business units, executive management, and boards. Incorporation into traditional governance, risk, and compliance (GRC) practices goes a long way. Planning and tabletop exercises are vital.
The business impact assessment (BIA) is also an excellent place to start. The BIA prioritizes business services and identifies interdependencies. It becomes the baseline from which resilience evolves. In practice, the codevelopment of scenarios among IT, business, and other departments is a key step.
Based on the common sources of threats and vulnerabilities identified by entities such as the Cloud Security Alliance (CSA) and Open Web Application Security Project (OWASP), it is clear that misconfiguration and human error are common causes of cyberincidents. It is natural for humans to lose objectivity. Traditional GRC practices such as the three (or four) lines of defense provide an extra set of eyes coupled with checks and balances that can catch misconfigurations and human errors before they cause problems. It is unlikely that all mistakes can be caught, but reducing their number makes the attacker's job harder and limits the impact when an incident occurs.
From Technical Defenses to Human Defenses
Historically, cybersecurity was treated as a technology problem that required a technology solution; therefore, it was the domain of IT. Robust technical defenses were developed to thwart malicious actors.
As the objective moved from protection to detection to recovery, technology's role decreased, people's role increased, and the importance of process and the organization remained constant (figure 1).
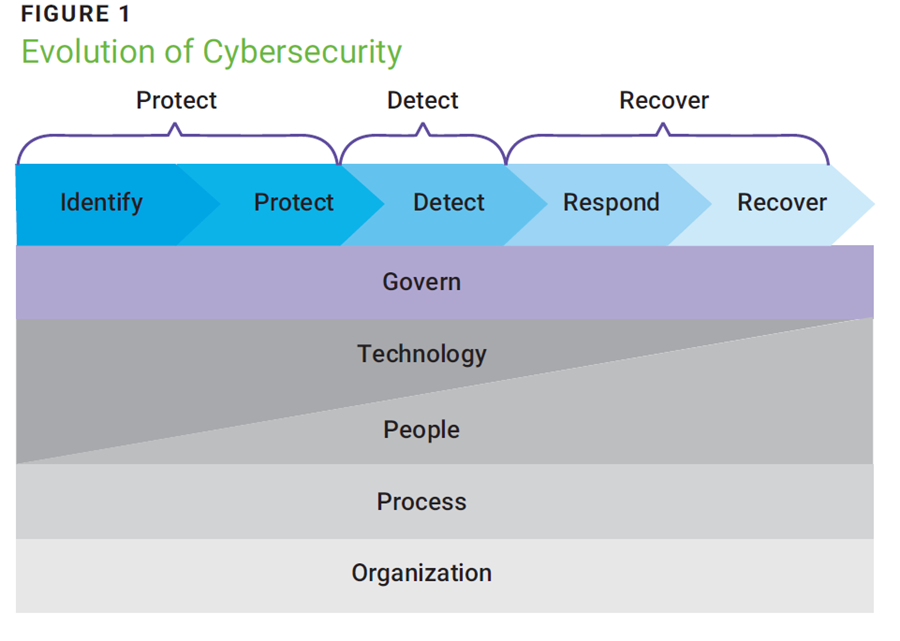
For clarity and to foster adoption, the relationship with NIST Cybersecurity Framework Version 2.0 (CSF 2) is illustrated.17 In essence, NIST decomposes the main phases of Protect, Detect, and Recover into five phases while adding the Govern element to address "The organization's cybersecurity risk management strategy, expectations, and policy [which] are established, communicated, and monitored."18 Resilience requires cooperation among technical defenses, processes, people, and organizations. The bad actors know this. They also know that technical defenses are strong, so attacking them costs money, takes time, requires skill, and involves a greater risk of detection. The payoff is excellent, but why would a bad actor commit valuable resources to technical defenses when softer targets are available?
Verizon's 2023 report on data breaches19 found that:
- The human element is the most common threat vector, causing 82% of data breaches.
- At least two-thirds of cyberattacks involve the impersonation of trusted users and systems to gain access to vital data or critical systems.
- A phishing attack is the first move in 91% of successful breaches.
Awareness and training are increasingly important as people become the primary targets of cyberattacks. Building a cyberaware culture is vital to building resilience. Fortunately, awareness and training are low-cost efforts with high returns. One report found that without training, 33% of users fell victim to social engineering (e.g., phishing attacks). Six months after instituting a training and awareness program, that number was almost cut in half to 18.5%. After a year, only 5.4% of people fell victim. These numbers vary by industry, but the positive results are consistent.20
Protection is not only about reducing the likelihood of a breach. It is also about reducing the impact. Anything that limits damage promotes resilience, reduces the total loss, and accelerates recovery. The principles underlying zero trust, such as segmentation, are excellent ways to accomplish this.21
Because most incidents target the human dimension and privilege escalation, the basic principles of identity and access management (IAM) go a long way toward reducing both the likelihood of a breach and its impact:
- Never trust, always verify
- Principle of least privilege
- Principle of least functionality
- Separation of duties
- Separation of roles
Detection and Containment
Enterprises detect only about 33% of incidents.22 Most incidents (40%) are detected by third parties (including law enforcement).23 In 27% of cases, enterprises find out about an incident because the attacker contacts the enterprise looking for payment.24 Ransomware and extortion are prime examples.
On average, it takes an enterprise more than nine months (277 days) to detect a breach.25 If we exclude the 27% of incidents that were detected due to the attacker's demands, the number in question would be significantly higher. Stolen or compromised credentials were the most common cause of a data breach in 2022, and these types of attacks took about 327 days to identify.26 It cost roughly US 4.35 million to recover from a data breach, with attacks on the healthcare sector having the highest cost.27
Detection and containment are full of opportunities for automation and planning. This is borne out by the numbers:
- Enterprises with extensive use of automation, including AI, identified and contained a data breach 108 days faster than those without.28
- Enterprises with an incident response team that practiced dealing with identified breaches contained breaches 54 days faster.29
- Enterprises using threat intelligence identified breaches 28 days faster.30
Advanced persistent threats (APTs) and activities by nation-states likely go undetected for much longer periods. Their long-term goal is espionage (e.g., stealing intellectual property) or lying in wait to take operations offline at a time of their choosing. SolarWinds is a prime example. Public statements indicate that the attackers were inside SolarWinds for at least 15 months before being accidentally detected by a third party.31 It is clear that detection is an area that needs improvement.
Incident Response
Incident response in a resilient world requires an external view and a focus on the intangible. Given today's highly interconnected world, incident response requires partnering with external parties and managing the expectations of stakeholders and shareholders. The numbers illustrate this:32
- 12% of enterprises identified a software supply chain attack as the source of a data breach.
- 15% of enterprises identified a supply chain compromise as the source of a data breach.
- 82% of breaches involved data stored in the cloud (public, private, hybrid).
In addition, reporting requirements are being included in agreements, regulations, and legislation affecting how an incident response is planned and executed. The cybersecurity rules recently adopted by the US Securities and Exchange Commission (SEC) are one example.33
The global threat environment, combined with legislative and regulatory requirements, justifies the engagement of law enforcement. The impact of cyberincidents is approximately 10% lower for enterprises that involve law enforcement.34 Engaging law enforcement provides greater insights, promotes better decisions, and provides access to a wider array of resources. In the case of bad actors from overseas and nation-states, the engagement of law enforcement provides potential access to diplomatic, financial, and other international assets.
The known impact of cyberincidents on digital trust and the ripple effect across an ecosystem justifies the need for crisis communication as part of incident response. Today's incidents deal with intangible assets such as reputation and goodwill.
One survey showed that about 60% of enterprises raised prices after a data breach, passing costs on to consumers.35
Conclusion
Resilience, or the ability to remain viable despite adversity, represents a paradigm shift that calls for alignment between business strategy, technology strategy, and operations. Enterprises exist in an ecosystem where an incident in one party can affect all the others. Resilience requires collaboration among technology, people, processes, and organizations through the cycle of protection, detection, and recovery. By evaluating an organization using the ORF and turning that self-assessment into a roadmap to achieve resilience, customers and business partners will be ready to act if digital trust is violated.
Endnotes
1 Ekudden, E.; "A Digital Silver Bullet for the World: Digitalization," World Economic Forum, 19 May 2022, https://www.weforum.org/agenda/2022/05/a-digital-silver-bullet-for-the-world/
2 Eisfeldt, A.L.; Kim, E.; Papanikolaou, D.; "Intangible Value," National Bureau of Economic Research (NBER), USA, November 2021, https://www.nber.org/papers/w28056
3
Madrigal, A.C.; "Your Smart Toast Can't Hold a Candle to the Apollo Computer," The Atlantic, 16 July 2019, https://www.theatlantic.com/science/archive/2019/07/underappreciated-power-apollo-computer/594121/
4
Chappell, B.; "U.S. HVAC Firm Reportedly Linked To Target's Data Security Breach," National Public Radio, 5 February 2014, https://www.npr.org/sections/thetwo-way/2014/02/05/272101928/u-s-hvac-firm-reportedly-linked-to-target-s-data-security-breach
5
Mathews, L.; "Criminals Hacked A Fish Tank To Steal Data From A Casino," Forbes, 27 July 2017, https://www.forbes.com/sites/leemathews/2017/07/27/criminals-hacked-a-fish-tank-to-steal-data-from-a-casino/?sh=d0b262532b96
6
National Institute of Standards and Technology, "Glossary," Computer Security Resource Center, USA, https://csrc.nist.gov/glossary/term/resilience
7
International Organization for Standardization, https://www.iso.org/obp/ui/#iso:std:iso:22316:dis:ed-1:v1:en
8
Office of the National Cyber Director, "National Cybersecurity Strategy," USA, March 2023, https://www.whitehouse.gov/wp-content/uploads/2023/03/National-Cybersecurity-Strategy-2023.pdf
9
European Commission, "Directive on Measures for a High Common Level of Cybersecurity Across the Union (NIS2 Directive)," European Union, https://digital-strategy.ec.europa.eu/en/policies/nis2-directive
10
White House, "PCAST Initiating Working Group in Cyber-Physical Resilience," USA, 15 March 2023, https://www.whitehouse.gov/pcast/briefing-room/2023/03/15/pcast-initiating-working-group-on-cyber-physical-resilience/; Global Resilience Federation, "The Operational Resilience Framework," https://www.grf.org
11
ISACA, https://www.isaca.org/
12
McKinsey, Why Digital Trust Truly Matters, 12 September 2022, https://www.mckinsey.com/capabilities/quantumblack/our-insights/why-digital-trust-truly-matters
13
Op cit Global Resilience Federation
14
Op cit Global Resilience Federation
15
Executive Office of the President, President's Council of Advisors on Science and Technology, Strategy for Cyber-Physical Resilience: Fortifying Our Critical Infrastructure for a Digital World, USA, February 2024,https://www.whitehouse.gov/wp-content/uploads/2024/02/PCAST_Cyber-Physical-Resilience-Report_Feb2024.pdf
16 Council for Science and Technology, "Joint Statement to Leaders from the United States' President's Council of Advisors on Science and Technology and United Kingdom's Prime Minister's Council for Science and Technology," March 2024, https://www.whitehouse.gov/wp-content/uploads/2024/03/PCAST-CST-Joint-Statement-March2024.pdf
17 National Institute of Standards and Technology, Cybersecurity Framework Version 2.0, USA, 26 February 2024, https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.29.pdf
18 Ibid.
19 Verizon, 2023 Data Breach Investigation Report, 2023, https://www.verizon.com/business/resources/reports/dbir/
20 KnowBe4, "Report: 2023 Phishing by Industry Benchmarking," https://info.knowbe4.com/en-us/phishing-by-industry-benchmarking-report
21 Cloud Security Alliance, "Zero Trust Guiding Principles," 18 July 2023, https://cloudsecurityalliance.org/artifacts/zero-trust-guiding-principles/
22 IBM, "Cost of a Data Breach Report 2023," https://www.ibm.com/reports/data-breach
23 Ibid.
24 Ibid.
25 Ibid.
26 Ibid.
27 Ibid.
28 Ibid.
29 Ibid.
30 Ibid.
31 Ramakrishna, S.; "New Findings From Our Investigation of SUNBURST," Orange Matter, 11 January 2021, https://orangematter.solarwinds.com/2021/01/11/new-findings-from-our-investigation-of-sunburst/
32 Op cit Executive Office of the President, President's Council of Advisors on Science and Technology
33 US Securities and Exchange Commission (SEC), "SEC Adopts Rules on Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure by Public Companies," USA, 26 July 2023, https://www.sec.gov/news/press-release/2023-139
34 Op cit IBM
35 Huang, K.; Wang, X.; et al.; "The Devastating Business Impacts of a Cyber Breach," Harvard Business Review, 4 May 2023, https://hbr.org/2023/05/the-devastating-business-impacts-of-a-cyber-breach
ALEX SHARPE
Is a cybersecurity, governance, and digital transformation expert with more than 30 years of operational experience. He has led business units, influenced national policy, and helped corporations and government agencies create value while mitigating cyberrisk. Sharpe began his career at NSA before moving into the management consulting ranks and building two practices. He subsequently cofounded two firms with successful exits and has participated in more than 20 mergers and acquisitions. Sharpe has delivered to clients in more than 20 countries on six continents. He can be reached at https://www.linkedin.com/in/alex-sharpe-3rd/.
