In cyberwarfare,1 data abuse is a potent weapon wielded by state actors, criminal enterprises, and hacktivist groups to achieve strategic objectives and create chaos. One of the most prevalent forms of data abuse is the unauthorized access to and exfiltration of sensitive information from government agencies, military organizations, enterprises, and critical infrastructure providers. Data abuse takes advantage of vulnerabilities in digital systems and exploits weaknesses in cybersecurity defenses to manipulate, compromise, or weaponize information for political, economic, or military gain. This multifaceted tactic encompasses a broad spectrum of malicious activities ranging from espionage and data theft to disinformation campaigns and sabotage of critical infrastructure.
Data abuse takes advantage of vulnerabilities in digital systems and exploits weaknesses in cybersecurity defenses to manipulate, compromise, or weaponize information for political, economic, or military gain.State-sponsored cyberespionage campaigns, such as those attributed to nation-states, often victimize high-value targets to steal classified data, intellectual property, and trade secrets. These covert operations enable adversaries to gain valuable insights into the opposition’s capabilities, intentions, and vulnerabilities, empowering them to shape geopolitical dynamics, advance national interests, and gain competitive advantages in various domains. In addition, data destruction by nation-state actors allows them to target critical systems by rendering the sensitive data useless.
Data abuse also extends beyond traditional espionage tactics to encompass the manipulation and distortion of information to influence public opinion, undermine trust in democratic institutions, and foment social discord. This phenomenon, referred to as “disinformation,” involves disseminating false, misleading, or inflammatory content across digital platforms to manipulate public perceptions, incite unrest, and amplify existing societal divisions. By exploiting vulnerabilities in social media algorithms, malicious actors can weaponize information to spread propaganda, discredit political opponents, and undermine democratic processes, thereby blurring the line between information warfare and traditional forms of conflict.
To mitigate data abuse in cyberwarfare, the authors propose a data abuse attack model that highlights how adversaries impact data integrity to achieve their goals.
Data Abuse Attack Model
The data abuse attack model (figure 1) represents various ways that nation-state attackers and adversaries impact the confidentiality, integrity, and availability of data and conduct unauthorized operations to meet their objectives during a cyberwar.
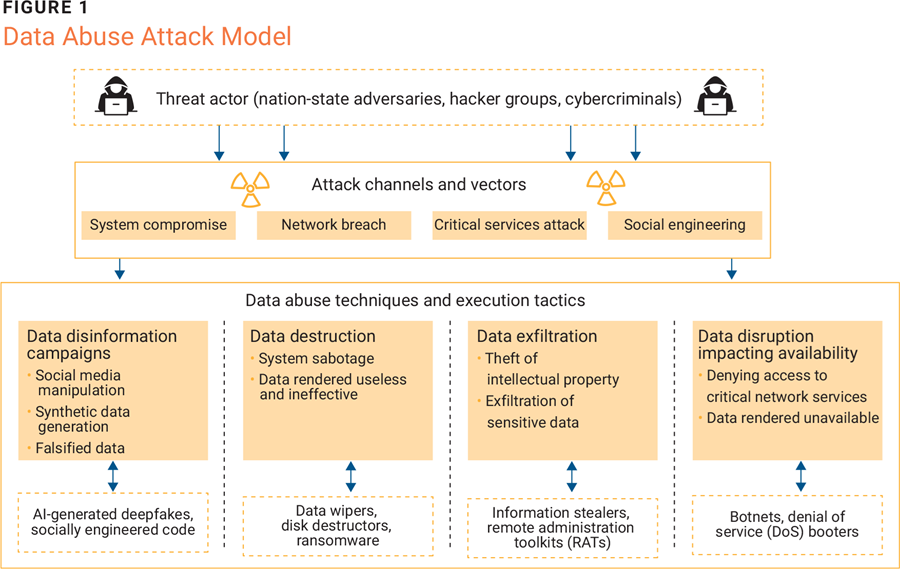
System compromise occurs when an unauthorized entity gains access to a device or computer system. This could potentially lead to the manipulation, theft, or destruction of data and the disruption of services. Once compromised, the system may be used for malicious activities including data exfiltration, further attacks, or alteration of system functionality.
A network breach involves unauthorized access to a computer network, often with the intent of stealing sensitive data, disrupting operations, or further infiltrating connected systems. Network breaches can have far-reaching consequences, including data loss, financial damage, operational downtime, and erosion of trust.
A critical services attack is highly disruptive and targets essential systems and infrastructure that are vital to the operation of an organization or society, such as power grids, healthcare systems, financial networks, or government services leading to service outages, data breaches, and widespread panic.
A social engineering attack often involves bypassing technical defenses to manipulate individuals into revealing confidential information to compromise security. These attacks exploit human psychology rather than relying on technical vulnerabilities, using tactics such as phishing emails, pretexting, baiting, or impersonation to deceive victims.
Data Disinformation Campaigns
During cyberwarfare, data disinformation campaigns are a sophisticated and insidious tactic used to manipulate public opinion, sow discord, and undermine trust in institutions.2 These campaigns involve disseminating false or misleading information disguised as factual data, often through online channels and forums. By leveraging data-driven narratives and fabricated evidence, attackers seek to shape public perceptions, manipulate electoral processes, and destabilize targeted societies.
Techniques
Adversaries employ various techniques to orchestrate data disinformation campaigns, including creating deepfakes, fake personas, and social media accounts; using botnets to amplify misleading content; and manipulating algorithms to promote divisive or inflammatory narratives. These campaigns may exploit vulnerabilities in human psychology, such as confirmation bias and echo chambers,3 to spread misinformation and undermine critical thinking among target audiences. By manipulating the digital landscape’s interconnected nature, attackers can disseminate disinformation with minimal effort or resource investment.
Impact
The consequences of data disinformation campaigns during cyberwarfare can be profound, leading to social polarization, erosion of trust in democratic institutions, and even the destabilization of entire nations. By manipulating public discourse and shaping political narratives, adversaries have the potential to influence electoral outcomes, incite social unrest, and impact the integrity of democratic processes. Moreover, the long-term effects of data disinformation campaigns, including the erosion of trust in media, can have lasting repercussions on societal cohesion, public discourse, and the democratic fabric of affected nations.
During the conflict between Ukraine and Russia,4 disinformation campaigns have shaped public perceptions in both nation-states, influenced international opinion, and exacerbated tensions between the two countries.
Data Destruction
Data destruction is a popular technique used by adversaries to impact the sanctity of data. It involves the deliberate and irreversible deletion, corruption, or manipulation of essential data stored within systems or networks, rendering it inaccessible or unusable. This tactic impedes the victim’s ability to function effectively, disrupts critical infrastructure, causes significant economic losses in many cases, and undermines public confidence in government institutions and enterprises.
Techniques
Cyberadversaries utilize advanced techniques to destroy data during cyberwarfare, ranging from targeted attacks on specific systems to widespread campaigns against entire networks or sectors. Nation-state actors may also exploit software, network, or human vulnerabilities to compromise systems and deploy destructive payloads, leveraging zero-day exploits or social engineering tactics. This includes using malicious code, such as data wipers or logic bombs,5 designed to overwrite or delete files, databases, or system configurations. Through data wiping, which irreversibly erases critical information from storage systems, and data corruption, which renders files or databases unusable or unreliable, adversaries can disrupt essential services, compromise sensitive information, and undermine the integrity of digital assets. Additionally, techniques such as disk formatting and logical destruction can render entire systems or networks inoperable, increasing the impact on targeted entities.
Impact
Data destruction results in significant financial loss, operational disruption, and reputational damage to the affected enterprises and governments. Critical infrastructures, including energy, transportation, and financial systems, are particularly vulnerable to data destruction attacks, which can lead to widespread service outages, economic disruption, and public safety concerns. Moreover, the psychological impact, including the loss of trust and confidence in the reliability and security of digital systems, can have lasting effects on a society’s resilience and ability to recover from cyberwarfare incidents. Throughout the Ukraine-Russia conflict, state-sponsored actors and independent hacking groups have engaged in data destruction operations targeting critical infrastructures, government agencies, military organizations, and civilian entities in both countries.6
Data Exfiltration
Data exfiltration is a dominant cyberwarfare tactic used by adversaries to gain strategic advantages and inflict significant harm on targeted entities.7 It involves the unauthorized extraction and transfer of sensitive information from compromised systems or networks to external locations controlled by the attackers. Data exfiltration serves various objectives in cyberwarfare, including espionage, intelligence gathering, economic espionage, and sabotage. The stolen data may include classified government documents, proprietary business information, intellectual property, personally identifiable information (PII), and other sensitive assets crucial for national security, economic competitiveness, or public safety.
Techniques
Data exfiltration during cyberwar often occurs through sophisticated, stealthy techniques designed to evade detection and circumvent traditional security measures. Cyberadversaries may exploit software, network, or human vulnerabilities to access targeted systems and extract sensitive information without raising alarms. Standard data exfiltration methods include covert channels, encrypted communications, steganography (hiding data within other files or media), protocol tunneling, and leveraging legitimate tools and protocols for malicious purposes. Adversaries may also employ advanced persistent threats (APTs) and malicious code tailored to exfiltrate data while persisting within compromised environments.
Impact
The consequences of data exfiltration during cyberwar can be far-reaching and severe, posing a significant risk to national security, economic stability, and individual privacy. Hostile actors may use stolen data to gain insights into military capabilities, intelligence operations, diplomatic strategies, or critical infrastructure vulnerabilities. The exfiltrated data allows them to formulate countermeasures, launch attacks, or conduct coercive actions. Moreover, data breaches resulting from exfiltration can lead to reputational damage, financial losses, regulatory fines, and legal liabilities for the affected enterprises and governments. Both Ukraine and Russia have engaged in data exfiltration attacks as part of the broader cyberconflict focused on stealing sensitive information from government agencies, military installations, and media outlets.8 Nation-state actors from both sides have employed sophisticated cyberespionage tactics, such as APTs and custom malware, to infiltrate target networks, maintain access, and exfiltrate valuable information without detection.
Data Disruption Through Denial of Service
Denial of service (DoS) attacks are a powerful weapon in the cyberwarfare arsenal. They hamper the availability of online services or networks by overwhelming them with malicious traffic. These attacks can have devastating effects, crippling vital infrastructure and causing significant economic and social disruption. DoS attacks interfere with the availability of critical services and impede data access. By saturating the target’s resources, DoS attacks can block access to services and data, causing significant disruptions and financial losses and rendering the target unable to respond to legitimate requests.
Techniques
Adversaries employ DoS attacks strategically in broader cyberwarfare operations to disrupt critical infrastructure services, often exacerbating political tensions between nations. Attackers utilize botnets and networks of compromised systems to launch massive requests, rendering numerous online services inaccessible to users during critical times. There are various types of DoS attacks, including volumetric attacks, protocol attacks, and application layer attacks. Adversaries prefer to launch DoS attacks that hinder response and recovery efforts, resulting in data unavailability for extended periods.
In addition to directly targeting the availability of data and services, DoS attacks can serve as a diversionary tactic, drawing attention and resources away from other attack vectors such as data breaches or sabotage attempts. By causing chaos and confusion within the target’s defenses, adversaries can exploit vulnerabilities, infiltrate systems, or conduct reconnaissance activities undetected. Thus, DoS attacks can amplify the overall impact of coordinated cyberoperations.
Impact
DoS attacks on nation-states can yield multifaceted results beyond mere technological disruptions. These attacks can cripple critical infrastructure, impairing essential services such as power grids, transportation networks, and communication systems and causing widespread chaos and economic damage. Moreover, targeting military operations and command structures can undermine national security, impeding military coordination and intelligence dissemination. The subsequent loss of public trust and confidence in governmental institutions can foster political instability and social unrest, exacerbating domestic and international tensions. DoS attacks have been launched on the telecommunications infrastructure in Ukraine and several important portals of the Ukrainian government, such as the cabinet of ministers and the ministries of defense, foreign affairs, education, and science, as well as on public and private banks and radio stations, impacting their availability for several hours.9 Overall, DoS attacks seriously threaten the availability and accessibility of critical services and data, highlighting the importance of implementing robust cybersecurity measures.
Recommendations and Security Measures
Defending against cyberattacks during cyberwarfare requires a comprehensive approach that combines technical and nontechnical measures. Figure 2 lists several security recommendations to help defend against data abuse during cyberwars. Deploying robust security controls helps protect against data abuse and prevent unauthorized operations during cyberwars. Enterprises and military networks should use continuous control enforcement strategies10 and harness the power of AI-driven cybersecurity solutions11 to ensure proactive security measures to mitigate attacks during cyberwars.
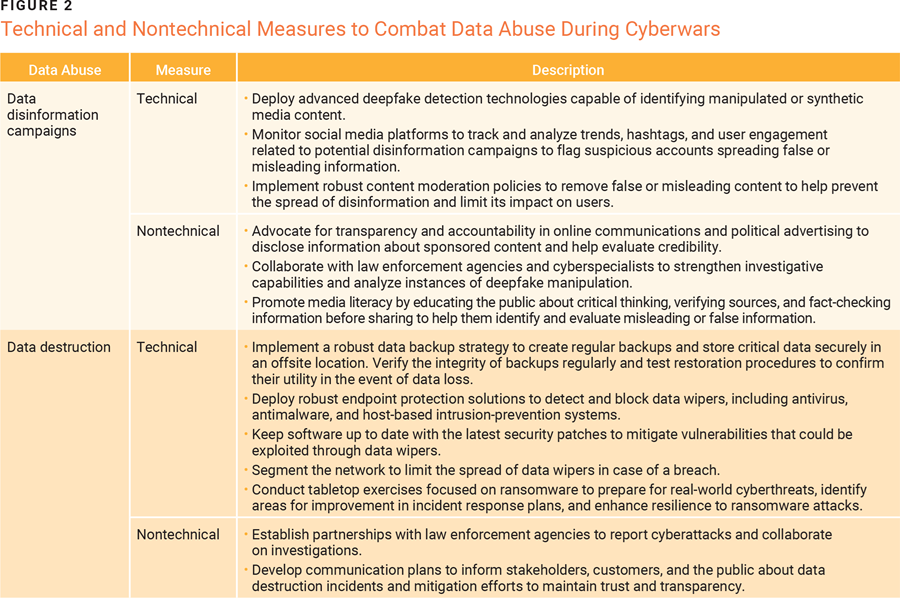
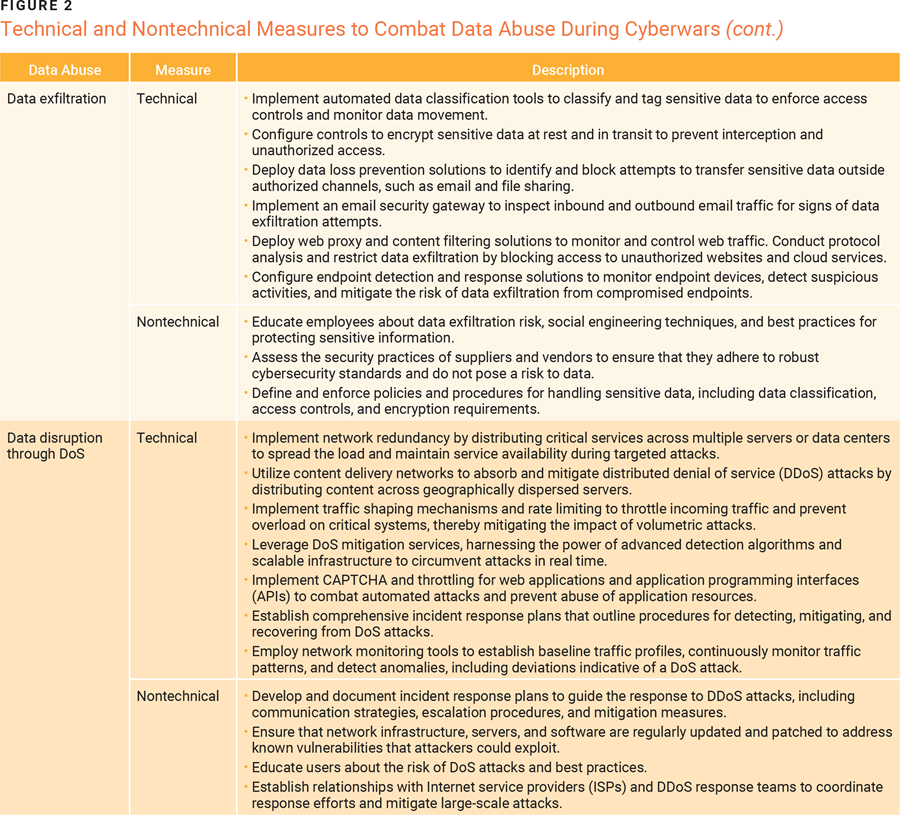
Deploying robust security controls helps protect against data abuse and prevent unauthorized operations during cyberwars. Enterprises and military networks should use continuous control enforcement strategies10 and harness the power of AI-driven cybersecurity solutions11 to ensure proactive security measures to mitigate attacks during cyberwars.
Conclusion
The data abuse attack model represents adversaries’ strategies to achieve their objectives during cyberwarfare operations. Data abuse in cyberwarfare encompasses a range of tactics aimed at undermining targets, gaining intelligence advantages, or causing operational disruptions. These techniques include unauthorized access to and theft of sensitive information, manipulation or fabrication of data to deceive or mislead, and the weaponization of data to disrupt critical infrastructure or destabilize political systems. Data abuse poses significant challenges to governments, enterprises, and individuals and can lead to severe consequences such as economic loss, reputational damage, and threats to national security. Addressing data abuse requires robust cybersecurity measures, international cooperation, and the development of legal and ethical frameworks to deter malicious actors and protect data integrity in the digital domain.
Endnotes
1 Flowers, A.; Zeadally, S.; “” IEEE Technology & Society Magazine, vol. 33, iss. 3, 2014
2 Voas, J.; “‘Propagating’ Disinformation,” Computer, vol. 56, iss. 12, p. 25-26, 2023
3 Mahmoudi, A.; Jemielniak, D.; Ciechanowski, L.; “,” IEEE Access, vol. 12, p. 9594-9620, 2024
4 Przetacznik, J.; Tarpova, S.; “Russia’s War on Ukraine: Timeline of Cyber-Attacks,” European Parliamentary Research Service, European Union, 2022
5 Recorded Future, Overview of the 9 Distinct Data Wipers Used in the Ukraine War, 12 May 2022
6 CERT-EU, Russia’s War on Ukraine: One Year of Cyber Operations, European Union, 25 February 2023
7 King, J.; Bendiab, G.; Savage, N.; et al.; “” 2021 IEEE International Conference on Cyber Security and Resilience (CSR), p. 442-447, 2021
8 Canadian Centre for Cybersecurity, Cyber Threat Bulletin: Cyber Threat Activity Related to the Russian Invasion of Ukraine, 2022
9 Center for Strategic and International Studies, Cyber War and Ukraine, 16 June 2022
10 Sood, A.; Nagal, A.; “AI as the Bedrock for Next- Generation Cyber Security Solutions,” Network Security, vol. 2024, iss. 1, 2024
11 Sood, A.; “Defensive Cyber Security: Continuous Controls Enforcement and Infrastructure Hygiene,” Network Security, vol. 2023, iss. 8, 2023
ADITYA K SOOD
Is the vice president of security engineering and AI strategy at Aryaka. With 17 years of experience in cybersecurity, he has worked for companies such as F5, Symantec, Bluecoat, and KPMG. Sood authored Empirical Cloud Security and Targeted Cyber Attacks, and frequently speaks at industry leading security conferences.
SHERALI ZEADALLY
Is a university research professor and Alumni Association-endowed professor at the University of Kentucky (USA). He is also a distinguished visiting professor at the University of Johannesburg (South Africa). His research interests include cybersecurity, privacy, Internet of Things, vehicular networks, and energy-efficient communications. He is a fellow of the British Computer Society and the Institution of Engineering and Technology.
